January 15, 2026
audit risk assessmentrisk managementinternal auditcompliance frameworksISO 27001
Mastering Audit Risk Assessment for Modern Compliance
Go beyond the checklist with our guide to audit risk assessment. Learn how to scope audits, prioritize risks, and use AI to strengthen your compliance strategy.
22 min readAI Gap Analysis

Let's get one thing straight: the old way of doing audit risk assessments is broken. Ticking boxes on a stale checklist won't cut it anymore. A modern audit risk assessment is about something more—it’s a strategic deep dive that digs up hidden vulnerabilities and turns compliance from a headache into a real competitive edge. It's how you systematically find threats, figure out how bad they could be, and then focus your audit on the things that actually matter.
From Compliance Burden to Strategic Advantage
With the maze of regulations like ISO 27001 and the constant drumbeat of new cyber threats, treating a risk assessment as just another compliance task is not only outdated, it's downright dangerous. A well-run assessment isn't about just getting a passing grade on your audit; it's about building a tougher, smarter organization.
Thinking this way is a game-changer. A solid assessment gives you a clear, practical roadmap for your entire compliance program, making sure you put your time and money where they'll do the most good. It gets your team out of "firefighting" mode and into a position where you're anticipating problems before they blow up. The payoff goes way beyond a clean audit report.
- Smarter Decision-Making: When you can put a number on your risks, you give leadership the hard data they need to make smart calls on where to invest in security and resources.
- More Efficient Operations: It shines a light on clunky processes and weak controls, leading to improvements that cut waste and make day-to-day work smoother.
- A Genuinely Stronger Security Posture: Honestly, a thorough risk assessment is one of the best tools you have for finding and fixing security gaps before an attacker does.
The Modern Assessment Workflow
A proper audit risk assessment isn't a "one and done" project; it's a living, breathing cycle. You have to clearly define the audit's scope, hunt down the real threats, measure their potential impact, and then actually do something about them.
This flowchart breaks down the high-level journey of a modern audit risk assessment, showing how it flows from scoping and assessment all the way through to remediation.
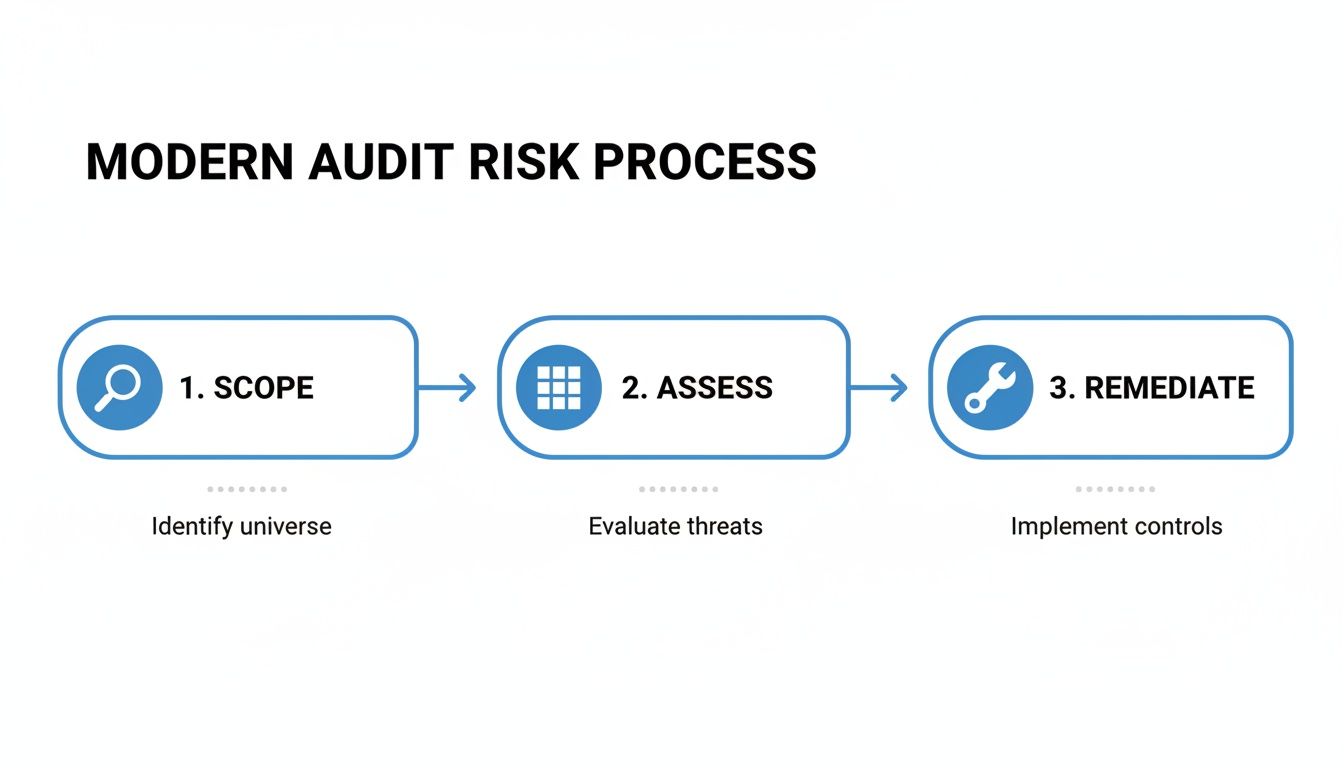
As you can see, each stage logically builds on the one before it. It’s a structured path that takes you from just understanding your risk landscape to actively making it better.
To give you a clearer picture, I've broken down the core stages into a simple table.
Key Stages of a Modern Audit Risk Assessment
| Stage | Primary Objective | Key Output |
|---|---|---|
| Scoping | Define the boundaries and focus of the audit. | A clear audit scope statement and plan. |
| Assess | Identify threats, evaluate controls, and score risks. | A prioritized risk register or heat map. |
| Remediate | Develop and track action plans for high-priority risks. | Documented remediation plans and progress reports. |
This table neatly summarizes the journey from planning to action, which is the heart of an effective risk assessment.
An audit's value isn't found in the checklist but in the action it inspires. The goal is to move beyond simply identifying findings to driving tangible improvements that protect the business and support its objectives.
Regulations are always changing, and your risk assessment process has to keep up. For example, new rules might suddenly require annual cybersecurity audits or detailed privacy risk assessments for high-risk data. Getting ready for these demands means getting your legal, tech, and operations teams working together to create processes you can repeat and prove. Nailing this workflow is a huge part of any successful compliance effort. If you're just getting started, our comprehensive guide on creating an effective audit readiness checklist is a great resource for laying the right groundwork.
Defining the Scope and Identifying Threats
An audit risk assessment that kicks off without a clear scope is like a road trip without a map. You'll definitely end up somewhere, but it's probably not where you wanted to go. The very first thing you need to do is draw some firm boundaries around the audit.
This means getting specific about which systems, business processes, data, and compliance frameworks are on the table. If you don't nail this down, you’ll fall victim to scope creep—the audit's objectives will just keep expanding, burning through time and resources for no good reason.
For an ISO 27001 audit, you might decide the scope includes all production servers with customer data, the development lifecycle, and the HR process for onboarding engineers. At the same time, you'd explicitly declare things like internal training sites as out of scope.
Setting these boundaries isn't just a paperwork exercise; it's a strategic move. It forces important conversations with stakeholders and gets everyone on the same page about the audit's purpose and limits. Getting this right from the start is critical, much like the initial work we outline in our complete gap assessment process, which also hinges on a well-defined scope.
From Boundaries to Real-World Threats
Once your scope is locked in, you can pivot to identifying the threats. This isn't some theoretical, abstract activity. It's about brainstorming the plausible, real-world scenarios that could actually hurt the assets you've put in scope. You have to think like an attacker, a disgruntled employee, or even just a tired developer who might make an honest mistake.
Let’s walk through a practical example. Imagine a fintech company gearing up for its first SOC 2 audit. The scope covers their mobile app, the cloud infrastructure it runs on, and the API that handles all the financial transactions.
A brainstorming session focused on threat scenarios might come up with these:
- Threat Scenario 1: An insecure API endpoint could let an attacker pull transaction data belonging to other users.
- Threat Scenario 2: A misconfigured cloud storage bucket accidentally exposes sensitive customer ID documents to the entire internet.
- Threat Scenario 3: A customer support rep falls for a phishing attack, leading to stolen credentials and fraudulent account takeovers.
See how each of those is specific and tied directly to the audit scope? That's far more useful than just listing vague concepts like "hacking" or "data loss."
Mapping Existing Controls to Identified Threats
The good news is, you're not starting from zero. Your organization already has controls—policies, procedures, and technical tools meant to keep risks in check. Now, you need to map these existing controls to the specific threats you just came up with.
This means digging into your current documentation—security policies, system configuration guides, incident response plans, and so on. For the fintech's insecure API threat, you’d be looking for evidence of controls like:
- Mandatory code reviews for any change to the API.
- Automated security scanning tools running in the CI/CD pipeline.
- Strict role-based access control (RBAC) on production systems.
Key Takeaway: The goal here is to find the gaps. Any threat that doesn't have a solid control mapped to it represents a major risk that the audit needs to focus on. This is really the heart of a gap analysis within your broader risk assessment.
Honestly, this mapping can be a slog. It often involves days of poring over dense policy documents. This is one area where modern tools can be a game-changer. AI-powered platforms can ingest all your documentation and automatically connect control statements to threats, even providing citations back to the source material. It can turn days of work into hours.
The Dominance of Cybersecurity in Risk Assessment
While you still need to think about operational and financial risks, let's be real: cybersecurity now dominates the audit risk landscape. The data on this is impossible to ignore.
A recent Risk in Focus 2025 Global Report from the Internal Audit Foundation found that a staggering 73% of internal auditors globally see cybersecurity as a top risk. That number is even higher in some places, hitting 88% in North America and 83% in Europe. It’s a clear signal that perceived digital threats, fueled by things like rapid AI adoption and geopolitical tensions, are at an all-time high.
What this means for your audit is that when you define your scope and identify threats, your attention will—and should—naturally be pulled toward your digital assets and security posture. To be effective, your audit risk assessment has to reflect the world we live in today.
How to Score and Prioritize Your Risks
So, you've got a list of potential threats. Now what? The real challenge is figuring out which ones actually matter. Let’s be honest, not all risks are created equal. Without a solid way to rank them, you could easily burn through your budget on minor issues while a major vulnerability sits there, waiting to blow up.
This is exactly where a structured approach to risk scoring comes in.
A risk matrix is your best friend here. It’s a simple but incredibly powerful tool that helps you visualize risk by pitting its likelihood against its potential impact. This lets you quickly sort threats into high, moderate, and low priorities. But the secret sauce isn't the matrix itself—it's getting everyone to agree on the definitions before you start plugging in numbers.
If you skip that step, scoring becomes a subjective mess. My "high impact" might be your "moderate," and suddenly the whole exercise is inconsistent and, frankly, unreliable.
Establishing Clear Scoring Criteria
To sidestep that problem, you need to hammer out clear, quantitative definitions for both impact and likelihood. I’ve found a 5x5 matrix hits the sweet spot—it gives you enough detail to be meaningful without getting bogged down in complexity.
Here’s a look at how you might define those scales:
-
Likelihood Scale (How likely is this to happen within a year?)
- Highly Unlikely: Has less than a 10% chance of occurring.
- Unlikely: Has an 11% to 40% chance of occurring.
- Possible: Has a 41% to 60% chance of occurring; it's a coin toss.
- Likely: Has a 61% to 90% chance of occurring.
- Highly Likely: Has a 91% or greater chance; it's practically a sure thing.
-
Impact Scale (If this happens, how bad will it be?)
- Insignificant: Minor operational hiccup, financial loss under $10,000.
- Minor: Noticeable disruption, financial loss between $10,001 and $50,000.
- Moderate: Significant operational impact, moderate brand damage, loss between $50,001 and $250,000.
- Major: Serious operational shutdown, significant brand damage, regulatory fines, loss between $250,001 and $1M.
- Catastrophic: A business-threatening event, severe penalties, widespread public distrust, financial loss over $1M.
With these definitions locked in, everyone on the team is scoring from the same playbook. This shared understanding is the bedrock of a defensible audit risk assessment.
Here's an example of how this looks when you bring it all together in a matrix. This helps visualize how the combination of likelihood and impact determines the final risk level, guiding your team to focus on what's truly critical.
Example Risk Scoring Matrix
| Likelihood | Impact Level 1 (Insignificant) | Impact Level 2 (Minor) | Impact Level 3 (Moderate) | Impact Level 4 (Major) | Impact Level 5 (Catastrophic) |
|---|---|---|---|---|---|
| 5 (Highly Likely) | 5 (Low) | 10 (Medium) | 15 (High) | 20 (Critical) | 25 (Critical) |
| 4 (Likely) | 4 (Low) | 8 (Medium) | 12 (High) | 16 (Critical) | 20 (Critical) |
| 3 (Possible) | 3 (Low) | 6 (Medium) | 9 (Medium) | 12 (High) | 15 (High) |
| 2 (Unlikely) | 2 (Low) | 4 (Low) | 6 (Medium) | 8 (Medium) | 10 (Medium) |
| 1 (Highly Unlikely) | 1 (Low) | 2 (Low) | 3 (Low) | 4 (Low) | 5 (Low) |
By plotting each risk on a table like this, you can immediately see what falls into the "Critical" and "High" zones, which is where you need to direct your attention first.
A Practical Scoring Example
Let's walk through a real-world scenario. Imagine a mid-sized tech company working toward its ISO 27001 certification. One of the threats they've flagged is "unauthorized access to the production customer database due to a compromised developer credential."
Now, the team gets together to score it using their new scales:
-
Likelihood: The CISO points out they've seen several targeted phishing attacks against developers in the past year. While they have multi-factor authentication (MFA), it's not consistently enforced on all internal tools. They land on a likelihood of Possible (3).
-
Impact: A breach of the production database would be an absolute nightmare. We're talking regulatory reporting, massive fines, customer exodus, and a brand reputation that's been torched. The team quickly agrees the impact is Catastrophic (5).
Multiply those scores (Likelihood 3 x Impact 5), and you get a total risk score of 15. On our 5x5 matrix, that lands squarely in the "High Risk" red zone.
A risk score is more than just a number; it's a conversation starter. The process of debating likelihood and impact forces your team to confront uncomfortable truths and build a shared understanding of your organization's vulnerabilities.
From Scores to an Actionable Roadmap
You repeat this scoring process for every single risk you've identified. The output is a prioritized risk register—your master list of threats, neatly sorted from most to least severe.
This risk register becomes your roadmap for the entire audit. You now have a data-driven reason to focus your limited time and resources on the things that pose a genuine danger to the business. That "compromised developer credential" risk? With its high score, it just shot to the top of the list for control testing and remediation planning.
One common trap I see people fall into is analysis paralysis. They spend way too much time debating whether a score should be a 14 or a 15. Don't do it. The goal isn't academic perfection; it's practical prioritization. Get a "good enough" score, document why you chose it, and move on. You can always tweak the scores in future assessments. This is how you turn a long, overwhelming list of problems into a focused and effective audit plan.
Connecting Evidence to Your Audit Test Plan
Alright, you’ve identified and prioritized your risks. Now, the audit risk assessment process pivots from planning to doing. This is where the rubber meets the road—where you have to prove that your controls aren't just well-written documents, but are actually alive and working in your day-to-day operations.
Every auditor lives by a crucial distinction: the difference between a control’s design effectiveness and its operating effectiveness. It's a simple concept, but one that trips up many teams. A control can look brilliant on paper yet be completely useless in practice. You have to test both.
- Design Effectiveness: Ask yourself, if this control worked perfectly as described, would it actually stop the bad thing from happening? For instance, a policy requiring quarterly access reviews for critical systems is, in theory, a solid design to mitigate unauthorized access risks.
- Operating Effectiveness: Now for the real-world test: Is the control actually being followed, consistently and correctly? Using our example, are those access reviews really happening every quarter? Is there documented proof? And most importantly, is access actually revoked when it's supposed to be?
A breakdown in either area means the control isn't working. A poorly designed control is a waste of time, and a perfectly designed control that nobody follows might as well not exist.
From Abstract Controls to Concrete Proof
This phase is all about creating a clear, undeniable link between each control and the evidence that proves it’s functioning. Vague assurances mean nothing to an auditor. You need to produce tangible artifacts.
Let’s stick with our control: "Quarterly user access reviews are performed for all production databases." What does real, defensible evidence for this look like? It’s certainly more than a manager saying, "Yep, we're on it."
To truly prove this control, you'd want to pull together a package of evidence, such as:
- System-generated reports showing all user accounts and permissions at the beginning and end of the review period.
- Dated sign-off sheets or completed tickets in a system like Jira, showing exactly who performed the review and on what date.
- Email chains or meeting minutes where the review's findings were discussed and formally approved.
- Follow-up actions, like helpdesk tickets confirming that access was removed for former employees or those who changed roles.
Each piece of evidence builds on the others to create a complete, verifiable audit trail. Without this trail, you're left with an opinion, not proof.
The Grind of Manual Evidence Collection
For most organizations, gathering all this evidence is a painful, time-consuming slog. It means chasing down different department heads with emails, digging through labyrinthine shared drives, and manually matching screenshots to line items on a massive spreadsheet. It's tedious work, ripe for human error, and a huge drain on your team's time.
This old-school manual approach is quickly becoming unsustainable. Audits are getting more frequent and far more complex, thanks to tougher regulations and greater stakeholder scrutiny. In fact, 58% of organizations recently reported conducting four or more audits in a single year, with large enterprises averaging over six. At the same time, adoption of frameworks like ISO 27001 has jumped 14% year-over-year—a clear indicator of the rising compliance pressure.
The success of your entire audit boils down to the quality and availability of your evidence. If you can't produce it on demand, an auditor has to assume the control isn't working. An unproven control is a failed control.
This is especially critical for rigorous certifications. If your company is gearing up for an information security audit, knowing the specific evidence requirements is half the battle. You can get a much deeper look into what that entails in our guide to navigating ISO 27001 audits.
A Smarter Way to Link Your Evidence
This is where the right technology can be a game-changer. Instead of your team spending a week hunting for documents, modern GRC or compliance platforms can automate the heavy lifting.
Imagine being able to upload your entire library of policies, procedures, and system documentation. An AI-powered agent can then read and index all of that information in minutes.
The next time you need to find evidence for a control like "background checks are required for all new hires," the system can instantly pinpoint the exact clause in your HR onboarding policy that mandates it. It doesn't just find the text; it gives you a direct citation and a link to the specific page and paragraph.
This changes the task from a frustrating scavenger hunt into a simple, direct query. What used to take days of manual labor can now be done in moments. This frees your team to focus on what really matters: analyzing the quality of the evidence, not just finding it in the first place.
Reporting Findings and Driving Remediation
An audit risk assessment creates a mountain of data, but that data is worthless if it doesn't spark real change. I've seen technically perfect audits fail completely because the final report landed with a thud, got filed away, and was never acted on. The real win isn't finding the problems; it's getting them fixed.
Your first job is to stop thinking of the audit report as a technical document for other auditors. It's a communication tool for leadership—the people who control budgets and assign resources. It needs to tell a compelling story they can understand, not just list a bunch of jargon-filled control failures.
What Makes a Finding Actionable?
Think about the difference between these two statements:
- Weak Finding: "The firewall configuration is incorrect."
- Strong Finding: "A misconfiguration in our primary firewall leaves the customer data network exposed to external threats. This creates a high risk of a data breach, which could lead to significant regulatory fines and do serious damage to our reputation."
The first one is a fact. The second one is a problem that demands a solution because it connects a technical issue directly to business pain.
Every finding you write needs to be a mini-business case. Vague findings get you vague (or zero) action. For a finding to have teeth, it has to be built on a solid foundation. I always make sure every single one includes these four C's:
- Condition: What’s broken? Be specific. "Quarterly access reviews for the finance database weren't done in Q2."
- Criteria: What rule, policy, or best practice is being ignored? "This violates section 4.2 of our Information Security Policy, which requires quarterly reviews for all systems with sensitive financial data."
- Cause: Why did it happen? This is the key to making sure it doesn't happen again. "The team lead was on extended leave, and no one was assigned as a backup."
- Consequence: So what? What’s the real-world impact if this isn't fixed? "This means unauthorized or inappropriate access to sensitive financial information could go undetected."
Building your findings this way leaves no room for ambiguity. It tells the reader exactly what's wrong, why it's wrong, how it happened, and what the fallout could be.
From Problems to a Plan
A report that's just a list of problems is essentially just a well-documented complaint. To make it useful, you have to provide a clear, actionable remediation plan. This is where you create accountability. From my experience, the number one reason audit findings fester for months is a weak or non-existent plan.
A solid remediation plan makes the solution official. You're not just suggesting a fix; you're creating a project with clear ownership.
| Component | Description | Example |
|---|---|---|
| Action Item | A specific, measurable task to solve the problem. | Implement a recurring, automated ticket in Jira for the access review. |
| Owner | The single person responsible for getting it done. | Jane Doe, IT Security Manager |
| Due Date | A realistic but firm deadline. | October 31, 2024 |
| Status | A simple way to track progress. | Not Started |
When you assign a name and a date, a passive observation becomes an active task. It gives you something concrete to follow up on and makes it clear who is on the hook.
The best audit reports I've ever written were seen as a catalyst for collaboration, not a tool for confrontation. Frame your findings as opportunities to get stronger and present the remediation plan as a shared roadmap to a more resilient organization.
How to Talk to Leadership About Risk
Finally, you have to sell your findings to the C-suite. Executives are short on time and have little patience for technical weeds. They think in terms of business impact, so you need to speak their language.
Don't lead your presentation by diving into the technical details of a vulnerability. Lead with the money.
For example, instead of explaining the intricacies of a server misconfiguration, start like this: "Our assessment found three high-priority risks that, if exploited, could expose the company to over $500,000 in potential regulatory fines and incident response costs. Let's walk through our plan to get these fixed."
That kind of opening immediately gets their attention. It frames the entire discussion around business risk, not just IT problems. By translating your technical work into the language of financial and reputational impact, you demonstrate the real value of the audit and get the buy-in you need to see the remediation through to the end.
Using AI to Sharpen Your Audit Risk Assessment
Technology is no longer just a nice-to-have in the audit world; it's a core part of any smart strategy. Artificial intelligence, especially, is completely reshaping how we approach audit risk assessments. It's taking tasks that used to be manual and tedious and turning them into fast, data-driven exercises.
This isn't about replacing an auditor's judgment. It's about amplifying it. Think of AI as a powerful assistant that handles the repetitive, detail-heavy work with a level of speed and precision humans simply can't match. This frees you up to focus on what really matters: strategic analysis, digging into root causes, and communicating your findings in a way that resonates with stakeholders.
Find Evidence in Minutes, Not Days
Let's get real about evidence collection. We've all been there—trying to verify a single control by hunting for a specific clause buried in thousands of pages of policy documents, system logs, and old meeting notes. It can feel like a multi-day scavenger hunt that brings the entire audit to a grinding halt.
This is exactly where AI agents can be a game-changer. These tools can read and make sense of your entire library of documents in minutes. When you need proof for a control, like "quarterly access reviews," you can simply ask the AI. It will instantly pinpoint the relevant sections, complete with citations and direct links to the exact page.
- Sift through thousands of pages instantly: AI can chew through huge amounts of unstructured data—from policies and procedures to technical reports—to find the specific evidence you need.
- Get direct citations: No more vague references. AI provides links directly to the paragraph or clause, making verification a breeze.
- Minimize human error: Automating the search process means you're far less likely to miss crucial evidence because of fatigue or simple oversight.
What was once a week-long headache becomes a task you can knock out in a few minutes, fundamentally speeding up your entire audit workflow.
Move from a Snapshot to Continuous Monitoring
A traditional risk assessment is a snapshot in time. The second you finalize it, it starts getting stale. New systems get rolled out, policies get tweaked, and configurations change. These shifts can quietly introduce new risks that won't be caught until the next annual audit cycle.
AI flips the script by enabling continuous monitoring. An AI agent can keep a constant watch over your document ecosystem. The moment a key policy is updated or a new system configuration file is uploaded, the AI can re-evaluate it against your control framework and flag any new gaps or inconsistencies right away.
An audit’s real value comes from its ability to adapt to a changing risk environment. AI helps shift the audit function from a reactive, backward-looking review to a proactive process that spots risks as they emerge.
This forward-looking approach is quickly becoming non-negotiable. The risk landscape is evolving fast, and our tools have to keep up. The Risk in Focus 2026 report found that 58% of Chief Audit Executives expect new technologies and AI to be a top-five audit priority within three years. On top of that, recent findings show that nearly 40% of CAEs are already planning to invest in GenAI to boost their risk assessment and anomaly detection efforts. You can discover more insights about these emerging internal audit topics.
Let Your Team Focus on What Humans Do Best
Ultimately, bringing AI into your risk assessment process isn't about getting rid of the human element—it's about making it more powerful. By taking the grunt work of data collection and initial analysis off your team's plate, AI tools create the time and space for auditors to do the work that truly requires human experience and critical thinking.
- Zero in on strategic analysis: With evidence at their fingertips, auditors can spend their time analyzing the effectiveness of controls and understanding why issues are happening.
- Improve stakeholder communication: Less time digging for documents means more time crafting clear, impactful reports that actually drive leadership to take action.
- Tackle more complex audits: AI gives your team the leverage to take on more challenging audits and cover more ground without having to dramatically expand your headcount.
Integrating AI makes the entire audit risk assessment process smarter, faster, and more valuable. It allows your team to evolve from compliance checkers into strategic advisors who help the organization navigate a complex world with more confidence.
Accelerate your audit readiness and streamline compliance with AI Gap Analysis. Our platform uses AI agents to automate evidence discovery from your documents, so you can map controls to proof in minutes, not weeks. Start your first analysis for free at https://ai-gap-analysis.com.