January 13, 2026
iso 27001 auditsisms auditaudit preparationinformation securitycompliance guide
Passing Your ISO 27001 Audits A Practical Guide
Master ISO 27001 audits with this complete guide. Learn the audit process, evidence requirements, and practical strategies to prepare and pass with confidence.
24 min readAI Gap Analysis

So, what exactly is an ISO 27001 audit? At its core, it's a formal, independent review to confirm that your organization's Information Security Management System (ISMS) truly aligns with the ISO 27001 standard. It's the ultimate test to prove your security practices aren't just written down, but are actively working and getting better over time. This audit is the final hurdle to cross for earning—and keeping—that coveted certification.
Demystifying The ISO 27001 Audit Journey
Think of it like getting a professional inspection before buying a house. You wouldn't just take the seller's word that everything is perfect. You'd bring in an expert to verify the foundation is sound and the electrical systems are safe. An ISO 27001 audit does the same thing for your information security, offering an objective, third-party confirmation that your digital "house" is in order.
The point isn't to catch you out or find faults. Instead, the audit provides concrete proof that your ISMS is a robust, well-managed system capable of protecting your data and adapting to new threats. This verification is what builds deep-seated trust with your customers, partners, and regulators, showing them you're serious about safeguarding sensitive information.
Key Players And The Audit Roadmap
The audit process involves a few key people. On your side, you'll have an internal team, usually headed by a compliance manager or CISO, who have built the ISMS and are responsible for collecting all the necessary evidence. The external lead auditor is the independent expert from an accredited certification body who evaluates your system against the standard's rigorous criteria.
The path to certification is generally split into two main stages:
- Stage 1 Audit: This is essentially a "desktop audit." The auditor focuses on your documentation—your policies, risk assessments, and Statement of Applicability (SoA)—to make sure your ISMS is designed correctly on paper.
- Stage 2 Audit: Once you pass Stage 1, the auditor comes back for a much deeper look. They'll conduct interviews and review evidence to confirm that the controls you've documented are actually in place and working effectively throughout the business.
The ultimate goal of any ISO 27001 audit is to confirm a cycle of continuous improvement. Auditors want to see that your ISMS is a living system that learns from incidents, adapts to changes, and consistently refines its defenses.
The need for this kind of formal validation is growing fast. ISO 27001 adoption has really taken off, with 81% of organizations reporting they either have or plan to get certified by 2025. That’s a huge leap from 67% in 2024. With more than 70,000 certificates expected worldwide by 2025, it’s clear that audits are shifting from a nice-to-have to a business imperative. You can explore more on these compliance trends to see where the industry is headed.
Getting a handle on this journey from the start gives you a clear mental map, helping you understand the "why" behind each request and setting you up for a smooth and successful audit.
Navigating The Two Stages Of Certification Audits
The journey to an ISO 27001 certification isn't a single exam; it's a two-part process. Think of it like getting a custom suit made. First, the tailor takes your measurements and draws up the patterns—that’s Stage 1. Then, you come back for a final fitting where they check the actual garment on you, ensuring every stitch is perfect and it fits exactly as planned—that’s Stage 2.
This two-stage approach for ISO 27001 audits is designed to be thorough. It ensures your Information Security Management System (ISMS) isn't just a great idea on paper, but a living, breathing part of your organization's culture that works in the real world.
Stage 1: The Documentation Review
The Stage 1 audit is essentially a readiness check. It’s a “desktop” review where the external auditor examines all your ISMS documentation, usually remotely. Their main job is to confirm that you’ve designed a system that—in theory—meets every requirement of the ISO 27001 standard.
At this point, they aren't looking for live proof that a control is working. They're focused squarely on the foundational documents that act as the blueprint for your entire security program.
Here are the key documents they'll put under the microscope:
- ISMS Scope Document: This document clearly outlines the boundaries of your ISMS, specifying which departments, locations, and assets are included.
- Risk Assessment and Treatment Plan: The auditor needs to see that you have a formal, repeatable process for identifying, analyzing, and mitigating information security risks.
- Statement of Applicability (SoA): This is a critical one. It lists every Annex A control and your justification for including or excluding it from your scope.
- Information Security Policy: This high-level policy is your proof that top management is committed and has set the tone for information security across the company.
If the auditor is satisfied that your documentation is complete, logical, and covers all the standard's requirements, they'll give you the go-ahead for Stage 2. Think of it as passing the theory test before you can take the practical driving exam.
The process flow below shows how this readiness check is the critical first step on the path to certification.
As you can see, the Stage 1 review lays the foundation for the more hands-on implementation check that follows.
Stage 2: The Implementation Audit
After you've successfully passed Stage 1, the Stage 2 audit kicks off, typically a few weeks or months later. This is where the rubber meets the road. The auditor moves from checking your blueprints to inspecting the finished building. Their goal is simple: verify that the policies and procedures you so carefully documented are actually being followed in your day-to-day operations.
This is all about "show, don't tell." The auditor will collect evidence in three main ways:
- Observation: They might watch how staff handle sensitive documents or observe the physical security controls in your server room.
- Interviews: They will talk to employees from various departments to see if they understand their security responsibilities, from incident reporting to clean desk policies.
- Record Inspection: Auditors will ask for hard evidence. This could be anything from server patch management logs and firewall rule reviews to new hire security training records.
An auditor's job in Stage 2 is to find objective evidence. They need to draw a straight, undeniable line from a control objective in your Statement of Applicability to a real-world activity that proves it’s effective.
For instance, to check your access control policy (Annex A control A.5.15), an auditor might interview someone from HR about the offboarding process. They'll then ask to see the system logs proving that a recently departed employee's access was revoked within the timeframe your policy dictates. Any gap between what your policy says and what your records show can result in a nonconformity.
ISO 27001 Audit Stages Compared
To make the distinction clearer, let’s break down what happens in each stage. The table below compares the objectives, activities, and outcomes of both audits.
| Aspect | Stage 1 Audit (Documentation Review) | Stage 2 Audit (Implementation Review) |
|---|---|---|
| Primary Goal | Verify the ISMS design is complete and compliant on paper. | Confirm the documented ISMS is fully implemented and operating effectively in practice. |
| Location | Typically remote or "desktop" review. | On-site (or remote interviews) to observe operations and interview staff. |
| Focus | Review of core documents: Scope, Risk Assessment, SoA, Policies. | Collection of objective evidence: Records, logs, interviews, direct observation. |
| Key Question | "Have you planned to do what the standard requires?" | "Are you actually doing what you planned to do?" |
| Outcome | A report detailing documentation strengths, areas for improvement, and readiness for Stage 2. | A final audit report with findings (nonconformities) and a recommendation for or against certification. |
As you can see, Stage 1 is about the "what" and "why," while Stage 2 is all about the "how" and "prove it."
The Role Of Internal Audits As A Dress Rehearsal
Long before the external auditors show up, ISO 27001 requires you to audit yourself. This is mandated by Clause 9.2, and it's far more than just a box-ticking exercise—it’s your single most important preparation tool. Think of the internal audit as the full dress rehearsal before opening night.
This process mirrors the external audit, but it’s conducted by your own trained personnel or a consultant you hire. The entire point is to find and fix the gaps, weaknesses, and nonconformities before the certification body discovers them. A well-executed internal audit gives management a clear-eyed view of how the ISMS is really performing and powerfully demonstrates your commitment to continual improvement, which is a core theme of the entire standard.
Gathering Evidence That Auditors Actually Need
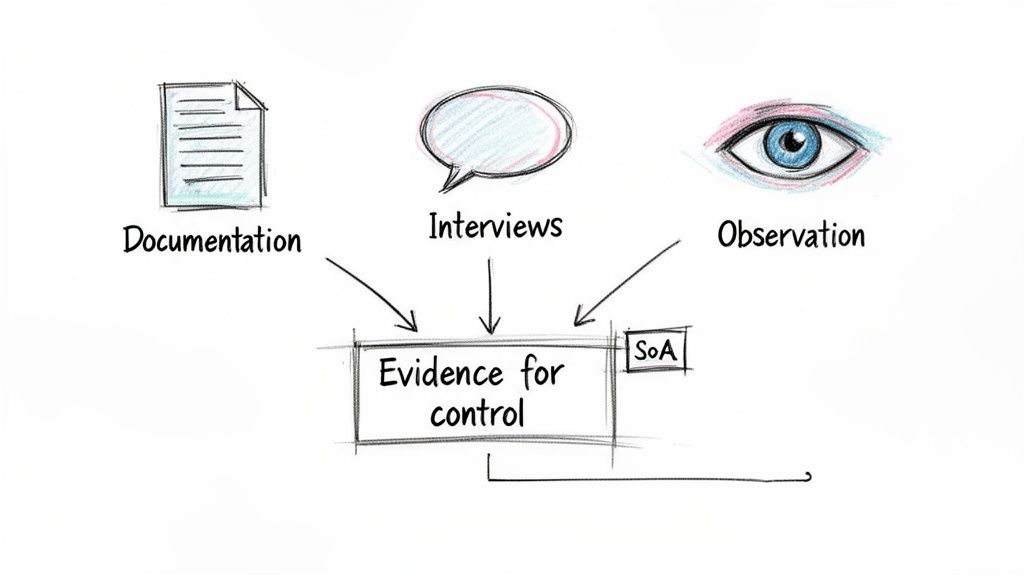
During any ISO 27001 audit, the auditor’s job boils down to one thing: verifying your claims. They live by a simple but unbreakable rule: "Say what you do, do what you say, and prove it." Evidence is the only language they speak, making your ability to provide clear, objective proof for every single control the most critical factor for a successful audit.
This goes way beyond just having a policy tucked away in a shared drive. A policy is just a statement of intent. An auditor needs to see that intent put into practice. They're looking for the complete story—a clear, unbroken line connecting your high-level security goals all the way down to the day-to-day activities that make them real. That’s the core of what audit evidence is all about.
The Three Pillars Of Audit Evidence
Think of an auditor like a detective building a case. A single witness isn't enough; they need documents, testimony, and physical evidence to piece together the full picture. Similarly, auditors gather evidence from three distinct sources to form their conclusions.
- Documentation: This is your paper trail. It includes your high-level policies, sure, but more importantly, it covers the records, logs, and reports that show those policies are actually being followed.
- Interviews: Auditors will talk to your people. This is their way of checking that security isn't just a document nobody reads, but a living concept that your team understands and applies in their roles.
- Observation: This means seeing your controls in action. An auditor might ask you to share your screen and demonstrate a process or physically inspect a server room.
A solid audit defense is built on evidence from all three pillars. A policy without records is just a good idea. Records without employee awareness point to a process no one follows. But when you have all three, you create a powerful, compelling case that your ISMS is working effectively.
From Control To Concrete Proof
So, how does this work in the real world? An auditor needs to draw a direct line from a specific Annex A control to the proof that it’s working. For every single control you’ve listed in your Statement of Applicability (SoA), you need to have your evidence ready to go.
Here are a couple of practical examples:
- For Control A.8.2 (Labeling of Information): The auditor will start by asking to see your data classification policy (documentation). Then, they might ask a project manager to show them how a "Confidential" project plan is labeled in your system (observation). Finally, they could ask a developer why certain information gets the classification it does (interview).
- For Control A.5.15 (Access Control): They’ll begin with your access control policy (documentation). Next, they'll want to see the access logs for your primary database for the last 30 days (more documentation). To tie it all together, they may ask an IT admin to walk them through the process for removing a former employee's access (observation).
An auditor's primary goal is to establish traceability. They need to see a verifiable trail leading from a control objective listed in your SoA directly to the tangible evidence—the logs, records, and employee actions—that proves the control is operating as intended.
The stakes for getting this right are only getting higher. The global ISO 27001 certification market is projected to hit USD 18.59 billion by 2025 and is expected to skyrocket to USD 74.56 billion by 2035. For any compliance team, this means ISO 27001 audits are a massive business driver, demanding rock-solid proof and continuous improvement. Learn more about the market's explosive growth and its impact on compliance.
How AI Streamlines Evidence Discovery
Let's be honest—manually digging through hundreds of documents to find the right snippet of evidence for each control is one of the most painful parts of getting ready for an audit. It’s a time-consuming, error-prone process that can leave you with dangerous gaps in your audit defense.
This is where modern tools are changing the game. AI-powered platforms can automate this entire discovery process. You can upload your library of policies, procedures, and reports, and an AI agent will read, understand, and map the content. It then connects specific sentences and paragraphs directly to the relevant ISO 27001 controls.
Instead of spending weeks hunting for proof, you get an evidence map with direct citations. This doesn't just speed up your prep time; it builds a verifiable audit trail that gives you the confidence to answer any question an auditor throws your way.
Don’t Get Tripped Up: Sidestepping Common Audit Pitfalls
Going through an ISO 27001 audit can feel like a high-stakes exam. But here’s the good news: most organizations don't fail because of some massive security disaster. They stumble over a handful of common, and completely preventable, mistakes. These are usually small, overlooked gaps in paperwork, processes, or evidence. Knowing where these traps are hidden is your best line of defense.
In auditor-speak, any mistake they find is called a nonconformity. All this means is that some part of your ISMS doesn't line up with a specific requirement in the ISO 27001 standard. These findings aren't all the same; they’re typically sorted into two buckets.
- Minor Nonconformity: Think of this as a small slip-up or a one-off issue. Maybe a single employee missed their annual security awareness training. It’s a problem you need to fix, but it doesn’t signal that your whole system is broken.
- Major Nonconformity: This is the big one. It points to a fundamental breakdown in your management system. A classic example is not having an internal audit program at all, which is a mandatory part of Clause 9.2.
If you get hit with a Major nonconformity, you can pretty much forget about getting certified until you can prove it’s been completely resolved. And be careful—enough Minor nonconformities can be bundled together and upgraded to a Major if they all point to the same underlying weakness. Getting ahead of these issues is the key to walking into your audit with confidence.
The Statement of Applicability Isn't Just a Checklist
One of the most common hurdles is a sloppy or poorly justified Statement of Applicability (SoA). This is the master document that lists all 114 Annex A controls and requires you to state whether you've implemented each one and, crucially, why.
The classic mistake here is just marking a control as "not applicable" without a rock-solid reason. For instance, you can't just ignore physical security controls because you're on a cloud platform like AWS. You have to clearly explain why that responsibility is fully handled by your vendor and show the paperwork to prove you did your homework on their security.
To get this right, make sure every single exclusion in your SoA has a clear, logical justification that traces right back to your risk assessment. Your auditor needs to see that you’ve thoughtfully considered every control, not just shrugged off the ones that seemed like a hassle.
Your Risk Assessment Needs Real Substance
Another major pitfall is a risk assessment that’s too shallow. ISO 27001 demands a formal, repeatable way of finding, analyzing, and dealing with information security risks. A generic list of threats you downloaded from the internet just won't fly.
An auditor will dig in and look for proof that you've:
- Pinpointed relevant assets, threats, and vulnerabilities: Your risk register should feel like it was built for your company, not anyone else's.
- Assigned risk owners: Every single risk needs a person’s name next to it—someone who is responsible for keeping an eye on it.
- Documented your risk treatment decisions: Whether you decide to mitigate, accept, avoid, or transfer a risk, that decision and the thinking behind it has to be written down.
A huge red flag for auditors is undocumented risk acceptance. If you decide to live with a risk because fixing it would be too expensive, that decision needs to be formally signed off by management. Without that paper trail, an auditor won't see a strategic business choice; they'll see a risk you simply ignored.
Where’s the Proof of Management's Buy-In?
Finally, auditors are trained to look for evidence of management's involvement, which is a core requirement of Clause 5.1. Leadership can't just sign the policy and then vanish. They have to be actively involved in the ISMS. The number one piece of evidence for this is the management review.
This is a formal meeting—not just a quick chat in the hallway—that must happen at planned intervals. It’s where the leadership team gets together to review how the ISMS is performing. A common stumble is treating this meeting too casually. Auditors will flat-out ask for the meeting minutes, who was there, and what action items came out of it.
If you can't produce those records, or if they show that key topics like audit results, security metrics, and the current risk picture were glossed over, you're getting a nonconformity. Why? Because it shows a lack of commitment from the top, and without that, an ISMS is just a binder of documents on a shelf.
It’s crucial to recognize these common problem areas so you can address them proactively. The table below outlines some frequent nonconformities auditors find and practical ways to get them fixed.
<br>| Common Nonconformity | Potential Classification (Major/Minor) | Effective Remediation Action |
|---|---|---|
| Lack of documented management review meetings | Major | Schedule recurring management review meetings. Use a standard agenda covering all required inputs (e.g., audit results, risk status). Document minutes, attendees, and action items rigorously. |
| Incomplete or unjustified Statement of Applicability (SoA) | Major | Review every Annex A control. For each exclusion, write a clear justification linked directly to your risk assessment. Ensure the SoA is version-controlled and approved. |
| Superficial risk assessment | Major/Minor | Revisit the risk assessment methodology to ensure it's robust. Identify specific assets, threats, and vulnerabilities. Assign owners to all risks and document treatment decisions, including formal acceptance. |
| Missing evidence of internal audits | Major | Implement a full internal audit cycle covering the entire ISMS scope before the certification audit. Create an audit plan, conduct the audits, and document findings and corrective actions. |
| Outdated or inaccessible policies and procedures | Minor | Establish a document control process (Clause 7.5). Ensure all ISMS documents are reviewed and approved periodically. Make them easily accessible to all relevant personnel via an intranet or shared drive. |
| Inadequate evidence of employee security training | Minor | Implement a security awareness program with tracking. Maintain records of who has completed the training and when. Follow up with anyone who is overdue. |
| Poorly defined ISMS scope | Major | Clearly document the boundaries of your ISMS, including processes, locations, and assets. Ensure the scope is aligned with your business objectives and stakeholder requirements. |
| No process for corrective actions | Major/Minor | Create a formal procedure for identifying nonconformities (from audits, incidents, etc.), analyzing root causes, and implementing and verifying corrective actions. Maintain a log of all actions taken. |
By treating this table as a pre-audit checklist, you can catch and resolve many of the most common issues before your auditor even sets foot in the door. It's all about turning potential weaknesses into demonstrations of your ISMS's strength and maturity.
Your 90-Day ISO 27001 Audit Preparation Plan
Successfully passing an ISO 27001 audit isn’t about a last-minute scramble. It’s the result of careful, methodical preparation. A structured 90-day plan is the best way to turn what feels like a monumental task into a series of calm, manageable steps.
Think of this timeline as your roadmap. It breaks the journey into three distinct phases, each with its own focus. By following this sequence, you build momentum and make sure nothing critical gets missed before the auditor walks through the door.
Phase 1: The Foundation (90 to 60 Days Out)
Your first 30 days are all about laying the groundwork. This is where you lock down your ISMS framework and get all your high-level documentation signed, sealed, and delivered. It's like checking the blueprints one last time before the building inspector arrives. Nail this phase, and you’ll avoid major headaches later.
The focus here isn't on collecting granular evidence. Instead, it’s about making sure your policies, scope, and risk assessments are rock-solid and truly reflect how your business operates.
Key tasks for this phase include:
- Confirm ISMS Scope: Get the key stakeholders in a room and formally re-confirm the boundaries of your Information Security Management System. Your scope document needs to be crystal clear, accurate, and have official leadership approval.
- Finalize Core Documentation: Review and get the final sign-off on your keystone documents. This means your Information Security Policy, Risk Assessment Methodology, and Statement of Applicability (SoA) should be finalized.
- Review Risk Register: Carve out time for a dedicated session to go through the risk assessment and treatment plan. Make sure every risk has an owner and that all decisions—especially for any accepted risks—are clearly documented.
Phase 2: Evidence and Internal Review (60 to 30 Days Out)
With a solid foundation in place, the next 30 days are about proving your ISMS works in the real world. This is easily the most intense part of the process, shifting from planning to execution. You'll be gathering the tangible proof auditors need to see and, just as importantly, running your own mandatory self-assessment.
Think of this period as your dress rehearsal. It’s your best opportunity to find and fix issues before an external auditor turns them into official nonconformities.
Your checklist for this critical month:
- Conduct the Mandatory Internal Audit: As required by Clause 9.2, you have to perform a complete internal audit of your ISMS. Document every finding, good and bad, in a formal report.
- Hold the Management Review Meeting: Schedule and run the official management review. The agenda must cover all the required inputs, like the results from your internal audit and key security metrics. Meticulously document the minutes, who attended, and any action items that come out of it.
- Gather Implementation Evidence: Now it’s time to start collecting proof for every single Annex A control listed in your SoA. This includes things like system logs, access reports, employee training records, and screenshots of configurations that show you’re doing what you say you’re doing.
Phase 3: Final Polish and Logistics (30 Days to Audit)
The final month is all about organization, communication, and logistics. You've done the heavy lifting. Now, it’s time to package it all up for a smooth and professional presentation. Your goal is to make the auditor's job as easy as possible by having everything they need right at their fingertips.
This is also when you'll prepare your team, making sure everyone knows what’s coming and how to conduct themselves during the audit.
An organized team is a confident team. The final days should be spent on presentation and communication, ensuring the auditor sees a mature, well-managed security program from the moment they arrive.
Final preparation steps:
- Remediate Internal Audit Findings: Take action on any nonconformities you found during your internal audit. Be sure to document the corrective actions you took to fix the root cause, not just the symptom.
- Organize Your Evidence: Create a central, easy-to-navigate repository for all your audit evidence. A great approach is to link your proof directly to the relevant ISO 27001 clauses and Annex A controls.
- Brief the Team: Hold a pre-audit briefing for any employees who might interact with the auditor. Walk them through the process, do a quick review of key policies, and answer their questions to help ease any anxiety.
For a more granular breakdown, you can use a detailed audit readiness checklist to track every item. This approach ensures nothing falls through the cracks as you move toward a successful certification.
How AI Can Fast-Track Your Audit Readiness
Anyone who has prepared for an ISO 27001 audit knows the pain of the evidence hunt. It’s a tedious, manual slog where your team spends days, if not weeks, digging through mountains of policies, procedures, and system reports. You're searching for that one specific sentence that proves a control is being met, and the whole process is slow, stressful, and wide open to human error.
Now, imagine you could skip that entire step. That's what new AI-powered tools bring to the table. Instead of manually combing through documents, you can upload your entire ISMS library into a secure platform. The AI then reads, digests, and connects the dots across all your documentation in minutes.
From Piles of Documents to a Clear Evidence Map
Think of the AI as a dedicated research assistant, not just a simple keyword finder. It actually understands the context of your policies and procedures. For every single ISO 27001 control, it delivers a clear answer backed by direct citations, pointing you to the exact page and paragraph in your source documents.
This gives you an instant, birds-eye view of your compliance posture. You can see exactly where your documentation is solid and—more importantly—where the gaps are. What was once a messy pile of PDFs becomes an interactive, organized evidence map.
The real win here is how quickly and accurately you can connect the standard’s requirements to what you already have, shining a bright light on both your strengths and weaknesses from the get-go.
Better Collaboration, Quicker Fixes
This technology does more than just find evidence faster; it improves the entire team's workflow. The moment a gap is flagged, you can start working on the fix right there in the platform. It becomes a central hub for collaboration, progress tracking, and building a solid audit trail for when the real auditors show up.
This means your team can finally stop wasting time on the grunt work of document hunting and start focusing on what actually matters: improving security controls and refining your processes.
Automating this initial analysis gives you some serious advantages:
- Massive Time Savings: A task that used to eat up weeks of your team's time can now be done in just a few hours. This radically shrinks your audit prep timeline.
- Fewer Errors: AI doesn't get tired or overlook details. It reduces the risk of missing key evidence or misinterpreting a policy, resulting in a much more accurate assessment.
- Greater Confidence: There's nothing better than walking into an audit with a complete, verified map of all your evidence. It gives your team the confidence to answer any question an auditor throws their way.
Using AI for audit prep helps your team work smarter, not harder. It turns a dreaded compliance task into a straightforward, strategic activity. To see how this fits into the bigger picture of getting ready, it's worth learning about the full gap assessment process and how to spot these issues early on.
Your ISO 27001 Audit Questions, Answered
As you get closer to the finish line, practical questions always come up. Let's tackle some of the most common ones I hear about the ISO 27001 audit process so you can move forward with a clear head.
How Long Does An ISO 27001 Audit Take?
There's no single answer here—it really comes down to the size of your company and how complex your ISMS is. But I can give you some solid ballpark figures.
The Stage 1 audit, which is mostly a documentation review, is pretty quick, usually taking just 1 to 3 days. The real heavy lifting happens in the Stage 2 audit. For a small to mid-sized company, you can expect the auditors to be onsite (or virtual) for anywhere from 3 to 10 days. Your certification body will give you an exact estimate based on your employee count, number of office locations, and the scope of your ISMS.
What Is The Difference Between Internal And External Audits?
While both audits look at your ISMS, they have completely different goals.
Think of the internal audit as a self-check. It's something you have to do (mandated by Clause 9.2) to find and fix issues before the real auditors show up. You can use your own trained staff or bring in a consultant for a fresh pair of eyes.
The external audit, however, is the formal review conducted by an accredited certification body. Their one and only job is to see if your ISMS meets the standard's requirements and is worthy of certification.
In simple terms, internal audits are your dress rehearsal to prepare for opening night. External audits are the final performance where the critics decide if you’ve earned the award.
Can We Actually Fail An ISO 27001 Audit?
You can, but "failing" isn't a dead end. If the auditor finds a "Major" nonconformity—meaning a critical part of your ISMS is broken or missing—they won't issue the certificate right away. You’ll need to fix the problem completely and show them proof before you can get certified.
For "Minor" nonconformities, the process is a bit more relaxed. You'll just need to submit a plan detailing how you're going to address the issue. The best way to think about an audit is as a diagnostic tool. It’s there to show you where the weaknesses are so you can strengthen them. To dive deeper, you can explore our educational resources on compliance readiness.
How Much Do ISO 27001 Audits Cost?
This is another "it depends" answer. The cost is all over the map based on your company's size, scope, and which certification body you choose.
For a smaller business, you could be looking at anywhere from $5,000 to $15,000 for the external audit fees spread across the initial three-year certification cycle. Keep in mind, that's just the auditor's bill. It doesn't factor in your internal costs like staff time, consultant fees, or any new security software you might need. My best advice? Get quotes from at least three different accredited certification bodies to compare and find one that fits your budget.
Ready to accelerate your audit preparation? AI Gap Analysis transforms your documents into an audit-ready evidence map, instantly highlighting strengths and gaps. Stop digging and start fixing. Discover how it works at ai-gap-analysis.com.