January 31, 2026
access control policyISO 27001cybersecurity policyinformation securitycompliance
Your Essential Guide to Building an Access Control Policy
Build an effective access control policy from scratch. Our guide covers key components, models like RBAC, and how to align with ISO 27001 for robust security.
23 min readAI Gap Analysis

An access control policy is the formal document that outlines how your organization manages access to its information, systems, and even physical locations. In simple terms, it's the official rulebook that dictates who gets to access what, and under what conditions. This document is a cornerstone of any serious cybersecurity and governance program.
What Is an Access Control Policy and Why Does It Matter
Think of your company as a large, secure building with a lot of different rooms, each holding valuable assets. Your access control policy is the master key system for the entire facility. It’s what ensures only the right people have the correct keys to enter specific rooms, stopping intruders while letting employees do their jobs without friction.
A senior executive’s key might open almost every door, while a marketing intern's key might only grant access to their own office and the break room. The policy is the blueprint that decides who gets which key, why they need it, and how that access is managed throughout their time at the company. Without it, you'd have chaos—every door would either be wide open or completely locked down.
The Core Goals of Access Control
At its core, a good access control policy is all about protecting the three pillars of information security, famously known as the CIA triad:
- Confidentiality: This is about preventing sensitive information from falling into the wrong hands. The policy makes sure that things like private customer data or proprietary financial records are only ever seen by people with a legitimate need to know.
- Integrity: This means keeping your data accurate, consistent, and trustworthy. Proper access controls stop unauthorized users from changing or deleting critical information, whether it’s by accident or on purpose.
- Availability: This ensures that systems and data are actually accessible to authorized users when they need them. The policy helps prevent disruptions that could lock legitimate users out of the tools they need to work.
An effective access control policy moves security from a reactive to a proactive state. Instead of just responding to breaches, you are building a foundational defense that systematically reduces your organization's attack surface.
Why This Policy Is Non-Negotiable
Trying to operate without a clear access control policy is just asking for trouble. Consider this: a staggering 34% of data breaches involve internal actors, which shines a bright light on the dangers of poorly managed permissions. And the consequences go far beyond security incidents.
Without a formal policy, you're leaving your organization wide open to:
- Costly Data Breaches: Unauthorized access is one of the most common ways attackers get in. With the average cost of a data breach now in the millions, it's a financial blow most businesses can't afford.
- Failed Compliance Audits: Regulations like HIPAA, GDPR, and PCI DSS all have explicit requirements for strict access controls. A weak or missing policy is an automatic red flag for any auditor.
- Operational Inefficiency: When access isn't defined, employees waste time struggling to get the permissions they need. At the same time, IT teams get buried under a mountain of manual, inconsistent access requests.
Ultimately, a well-crafted access control policy isn't just a technical document you file away for compliance. It’s a living framework that protects your most valuable assets, builds trust with your customers, and fosters a secure, efficient workplace.
The Building Blocks of an Effective Access Control Policy
A great access control policy isn't one giant, intimidating document. It’s actually a framework made up of several distinct parts, all working together to protect your company's most valuable assets. Think of it like building a secure facility: you need a solid blueprint, strong walls, locked doors, and a clear system for who gets which keys.
By breaking the policy down into these core components, it becomes much easier to write, implement, and, most importantly, maintain. This approach ensures you've covered all your bases, from high-level strategic goals down to the everyday procedures that keep your data safe.
Defining Your Policy Scope and Purpose
The first thing you need to nail down is the policy's scope and purpose. This is the foundation for everything else. It answers the big questions right up front: What exactly are we protecting? Who has to follow these rules? And what's the ultimate goal here?
Your scope needs to draw clear lines in the sand. Does the policy only cover digital systems, or does it extend to physical access, like server rooms and keycard-protected offices? You also need to state precisely who it applies to—full-time employees, contractors, third-party vendors, and even interns. If you don't define the scope clearly, you'll end up with gaps that are impossible to enforce.
Getting this section right sets the stage, ensuring everyone from the IT team to a brand-new hire understands what the policy is for and how they fit into it.
Clarifying Roles and Responsibilities
With the scope set, your next move is to assign clear roles and responsibilities. A policy without designated owners is just words on a page. You have to specify who is accountable for each piece of the access control puzzle, from granting access to revoking it. This step is critical for preventing security tasks from falling through the cracks.
Here are the key roles you'll want to define:
- System Owners: These are the people or teams in charge of a specific application or dataset. They are the ones who have the authority to approve or deny access requests for the resources they "own."
- IT Administrators: This is the technical crew responsible for actually implementing, configuring, and maintaining the access controls according to the rules laid out in the policy.
- Users: Every single person granted access has a part to play. Their responsibility is to safeguard their credentials and follow the rules.
- Management/HR: This group is essential for keeping the system updated. They communicate promotions, role changes, and departures that trigger necessary changes to someone's access rights.
By documenting these roles, you create a clear chain of command and accountability that makes your entire security posture stronger.
A well-structured access control policy isn't about restricting people; it's about enabling the right people with the right access at the right time. It transforms security from a barrier into a business enabler.
The Principle of Least Privilege
If there’s one guiding philosophy that should be at the heart of your policy, it's the Principle of Least Privilege (PoLP). The idea is brilliantly simple but incredibly powerful: a user should only have the absolute minimum permissions needed to do their job. Nothing more.
For example, a marketing coordinator needs access to the company’s social media scheduling tool and blog platform. They absolutely do not need to get into the finance department's payroll system or the engineering team's code repository. On the other hand, a senior database administrator needs high-level permissions to manage critical databases, but they shouldn't have access to the HR team's applicant tracking system.
Putting PoLP into practice dramatically shrinks your organization's attack surface. If a user's account ever gets compromised, the damage is contained only to the specific systems they could access. The data backs this up. A 2023 survey found that a remarkable 71% of organizations using this approach had five or fewer serious unauthorized access incidents per year, proving how well it works. The same research from ASIS International on access control effectiveness noted that two-thirds of security professionals have to meet regulatory requirements, with ISO 9001 being a common driver.
Structured Access Review Procedures
Finally, no access control policy is complete without a plan for regular access reviews. People’s jobs change. They switch teams, get promoted, or leave the company. If you don't periodically check permissions, you'll end up with "privilege creep"—where users slowly accumulate access they no longer need, creating a major security risk.
Your policy must outline a formal review process, spelling out:
- Frequency: How often will you review access rights? Quarterly for most users and monthly for highly privileged accounts is a common starting point.
- Process: Who is responsible for doing the review? This is typically a manager or system owner who has to sign off on their team's current access levels.
- Documentation: Every review needs to be documented. This creates a clear audit trail that proves you're doing your due diligence and staying compliant.
These scheduled checks are your best defense against outdated permissions, ensuring your access controls always align with the principle of least privilege.
Choosing the Right Access Control Model
Once your policy lays down the rules, you need a system to actually enforce them. Think of your access control policy as the "what" and the "why"—what needs protecting and why. The access control model is the "how." It's the engine that brings your rules to life.
These models are the operational frameworks that systems use to answer a single, critical question every time someone tries to do something: "Should this user be allowed to access this resource right now?" The three most common models—RBAC, ABAC, and MAC—each tackle this question in a very different way.
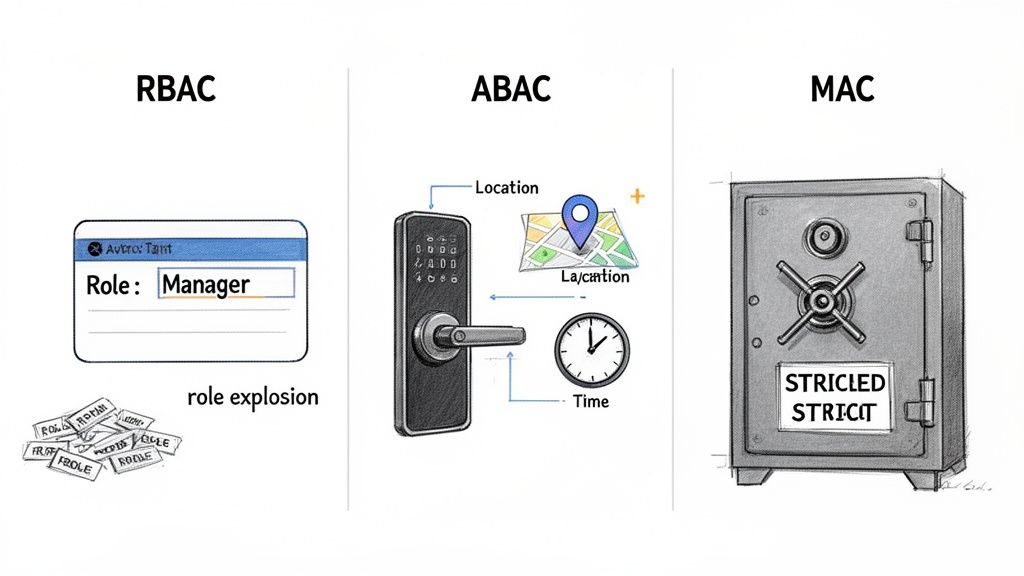
Role-Based Access Control (RBAC)
By far the most common model you'll find in the business world is Role-Based Access Control (RBAC). Its appeal is simplicity. Instead of assigning permissions to every single person, you group permissions by job function. You create a "Project Manager" role, an "Accountant" role, or a "System Administrator" role, and then you simply drop people into the right bucket.
It’s like giving out keycards in a hospital. All nurses get a card that opens patient rooms and supply closets on their floor. Doctors get a card with broader access to labs and records. The system doesn't know or care if it's Nurse Miller or Nurse Davis; it just checks the role assigned to the card. This makes onboarding new hires a breeze—just assign them the right role, and they're good to go.
But RBAC has a well-known scaling problem called "role explosion." As your organization gets more complex, so do the roles. Soon you have "Accountant-EastCoast" and "Junior_Accountant_AccountsPayable," and the clean simplicity is gone. One real-world study of a retailer with 2,040 users across 380 stores found that managing access required at least 2,380 individual policies. As you can imagine, that gets messy fast. You can discover more insights about RBAC scalability challenges on immuta.com.
Attribute-Based Access Control (ABAC)
This is where Attribute-Based Access Control (ABAC) comes in. It's a more dynamic and intelligent way to manage access. Instead of relying on a static job title, ABAC looks at a combination of real-time attributes—or characteristics—of the user, the data, and the environment.
Think of it like the security for a high-tech lab. The door doesn't just check if you're a "Scientist" (your role). It asks a series of questions:
- User Attributes: Is this person assigned to Project X?
- Resource Attributes: Is the data they're trying to access classified as "Top Secret"?
- Environmental Attributes: Are they trying to access it during business hours from a company-issued laptop inside the building?
The door only unlocks if all the conditions are met. This context-aware logic is incredibly powerful and is the foundation for modern security philosophies like Zero Trust, where every single access request is treated with suspicion and verified.
ABAC shifts the question from "who are you?" to "what's the full context of this request?" It's this situational awareness that makes it so effective for today's complex environments.
Mandatory Access Control (MAC)
At the other end of the spectrum is Mandatory Access Control (MAC), the most rigid and restrictive model of them all. In a MAC system, a central authority assigns security labels to everything—users get a clearance level, and resources get a classification level (e.g., "Confidential," "Secret," "Top Secret").
The rule is simple and absolute: you can only access information if your clearance is equal to or higher than the data's classification. End of story. This is the gold standard for government, military, and intelligence agencies where protecting classified information trumps all other concerns. The system administrator enforces the rules, and not even the person who created a file can change its security level. Flexibility is sacrificed for absolute, top-down control.
Comparison of Access Control Models
Choosing the right model is a strategic decision that depends entirely on your organization's specific needs. To help you decide, this table breaks down the core differences between RBAC, ABAC, and MAC.
| Model | Basis for Access | Pros | Cons | Best For |
|---|---|---|---|---|
| RBAC | User's job role or function. | Simple to implement and manage, especially in smaller organizations. Low administrative overhead for stable role structures. | Can lead to "role explosion" as the organization grows. Not granular enough for complex scenarios. | Businesses with clearly defined job functions and relatively static hierarchies. |
| ABAC | Attributes of the user, resource, action, and environment. | Highly flexible, dynamic, and granular. Adapts to real-time context and supports Zero Trust principles. | Complex to set up and manage. Requires sophisticated policy engine and attribute sources. | Large, dynamic organizations, cloud environments, and companies with complex data-sharing needs. |
| MAC | System-enforced security labels and clearance levels. | Highest level of security and control. Prevents data leaks and unauthorized modifications. | Inflexible and rigid. High administrative burden. Not suitable for collaborative environments. | Government agencies, military, and any organization handling highly classified information. |
Ultimately, the best model is the one that aligns with your security requirements, operational complexity, and future growth plans. Some organizations even use a hybrid approach, applying RBAC for general access and ABAC for more sensitive, context-dependent resources.
How to Create and Implement Your Access Control Policy
An access control policy sitting on a server is just a collection of ideas. The real challenge—and where the work truly begins—is turning those ideas into a living, breathing part of your company's security culture. This isn't just about writing a document that gets filed away; it's about building a practical, enforceable framework that weaves together people, processes, and technology.
Getting from concept to reality happens in phases. It starts with getting the right people in the room, figuring out exactly what you need to protect, and then carefully writing the rules. After that, it’s all about getting buy-in, training your team, and plugging the policy into the technology you already use.
Step 1: Assemble Your Cross-Functional Team
Trying to create an access control policy from within the IT department alone is a recipe for failure. To get this right, you need a team with different perspectives to make sure the policy is solid, workable, and legally compliant. Without that collaboration, you risk creating rules that look great on paper but are impossible to follow in the real world.
Your core team should have a seat at the table for:
- Information Technology (IT): These are the folks who understand the technical guts of your systems. They’ll be the ones actually implementing and enforcing the rules.
- Human Resources (HR): HR owns the employee lifecycle—hiring, role changes, and departures. These are the most critical moments for managing access rights.
- Legal and Compliance: This team is your safeguard. They make sure the policy checks all the boxes for regulations like GDPR or HIPAA and keeps the company out of legal trouble.
- Department Heads: Business leaders know what information is most important for their teams to function. Their input is crucial for defining who really needs access to what.
Bringing these groups together from the start ensures the final policy actually works for everyone and gets the support it needs to succeed.
Step 2: Inventory and Classify Your Assets
You can't protect what you don't know you have. The next logical step is to take a complete inventory of every critical asset in your organization, both digital and physical. This isn't just about making a list; it's about understanding the value and sensitivity of each item on that list.
Start by mapping out everything that holds important information, such as:
- Systems and Applications: Think financial software, CRMs, and any custom-built internal tools.
- Databases: This is where your most sensitive data lives—customer lists, employee records, and intellectual property.
- Physical Locations: Don’t forget about server rooms, R&D labs, or even locked filing cabinets.
Once you have your list, classify each asset based on how sensitive it is. A simple framework like Public, Internal, Confidential, and Restricted works well. This classification directly tells you how tight the access controls need to be, so you can focus your strongest defenses on your most valuable data.
Step 3: Define User Roles and Access Levels
With your assets neatly classified, it’s time to define who gets access to them. This is where the Principle of Least Privilege comes into play. The goal is to group employees by their job function and give them the absolute minimum level of access they need to do their jobs—and not a bit more. Resist the urge to grant sweeping permissions just because it seems easier.
For every role, spell out the specific permissions they need. For example, a "Marketing Analyst" might need read-only access to customer analytics, but they should never be able to touch the production database. On the other hand, a "Database Administrator" absolutely needs high-level privileges for that same database. This precise mapping is the very heart of your access control policy.
A common pitfall here is creating roles that are too generic. Get specific. The more granular your roles are, the tighter your security will be and the easier it becomes to audit permissions down the line.
Step 4: Draft and Socialize the Policy
Now, you can finally start writing. Use plain English and steer clear of technical jargon. The document needs to make sense to everyone, from a new hire in sales to a senior developer. Make sure your policy explicitly covers key scenarios like remote access, permissions for third-party vendors, and the formal process for requesting changes to access rights. If you need more guidance on structuring security documents, you might find our guide on creating a comprehensive information security policy helpful.
Once you have a draft, don't just publish it. Take it on a roadshow. Get executive sign-off to show that security is a company-wide priority. Walk department heads through it to make sure the roles and permissions you’ve defined actually align with how their teams work. This feedback is critical for ironing out the kinks and preventing pushback later.
Step 5: Train Employees and Integrate with Technology
The final step is where the policy comes to life. This happens on two fronts at once: educating your people and configuring your tech.
Run training sessions for all employees. Don’t just read the rules—explain the why behind them. When people understand the risks you're trying to prevent, they're much more likely to get on board.
At the same time, your IT team will be busy configuring your systems—like Active Directory, cloud IAM tools, and other platforms—to automatically enforce the policy. This is where the roles you defined on paper become real, system-enforced permissions, turning your access control policy into an active, automated line of defense.
Aligning Your Policy with ISO 27001 and Other Frameworks
If you're a compliance or GRC professional, this is where the rubber meets the road. A solid access control policy isn't just an internal best practice—it's one of the first things an auditor will ask to see. It’s the tangible proof that your organization takes security seriously and has a documented strategy to back it up.
Trying to demonstrate compliance without a formal policy is a nightmare. You end up scrambling for scattered pieces of evidence and trying to explain ad-hoc processes. A well-written policy, on the other hand, gives you a clear, auditable roadmap that links your security controls directly to internationally recognized standards.
Mapping Policy Components to ISO 27001 Controls
When it comes to information security management, ISO 27001 is the gold standard. A huge chunk of its Annex A controls deals specifically with access control, making your policy a cornerstone of any certification effort. Your policy doesn't just support compliance; it actively fulfills specific control objectives.
Let's draw a straight line from what's in your policy to the clauses an auditor will check:
- A.9.1 Business requirements of access control: Your policy's scope and purpose statement hit this nail on the head. It's the formal documentation of your organization's rules for who can access what.
- A.9.2 User access management: The procedures you’ve laid out for creating, changing, and deleting user accounts are direct evidence for this control. It proves you have a structured process for the entire user lifecycle.
- A.9.4 System and application access control: This is covered by your rules on password complexity, session timeouts, and restrictions on powerful admin tools.
The Principle of Least Privilege is a perfect real-world example of this alignment. By making it a core part of your policy, you directly satisfy the requirements of ISO 27001's A.9.2.2 (User access provisioning), which demands that access rights are granted strictly on a need-to-know and need-to-use basis.
The diagram below shows how a good policy gets built from the ground up—by getting the right people involved, knowing what assets you have, and clearly defining everyone's role.
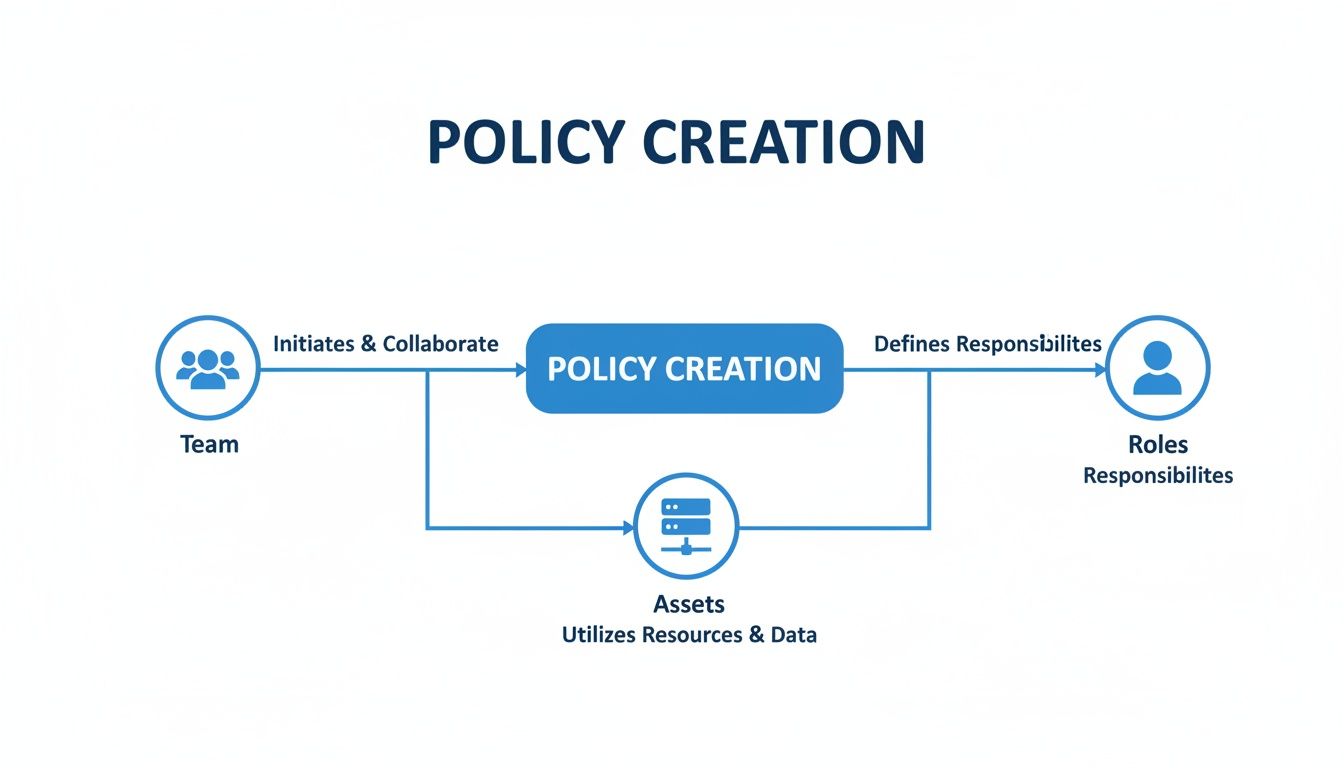
This just goes to show that a compliant policy starts with a clear, collaborative process. For a deeper dive into the standard itself, check out our guide on what ISO 27001 compliance entails.
Beyond ISO 27001: Connections to HIPAA, GDPR, and More
The beauty of a strong access control policy is that it does triple duty. The same components that satisfy ISO 27001 also serve as powerful evidence for a whole host of other critical regulations.
Take the HIPAA Security Rule, for instance. It requires healthcare organizations to implement safeguards for electronic protected health information (e-PHI). Your access control policy directly addresses sections like §164.312(a)(1) on unique user identification and §164.308(a)(4), which covers procedures for authorizing and supervising staff.
It's the same story for financial rules like PCI DSS and privacy laws like GDPR, both of which have strict requirements for limiting access to sensitive data. In any of these audits, your policy is the first document they’ll want to see.
This growing web of regulations is why the global access control market, valued at USD 18.01 billion in 2024, is projected to grow at a CAGR of 8.5% through 2032. As more organizations adopt these frameworks, the need for well-documented and enforceable policies only gets bigger.
Using AI Gap Analysis to Automate Compliance Mapping
In the past, mapping policy clauses to framework requirements was a grueling, manual job. Compliance teams would live in spreadsheets, spending hours cross-referencing documents—a process that was slow, tedious, and prone to human error.
This is where modern tools can make a world of difference.
AI-powered gap analysis platforms can automate this entire workflow. Instead of you manually slogging through documents, these tools ingest your policies and use advanced language models to map your controls directly against the specific requirements of frameworks like ISO 27001, HIPAA, or SOC 2.
The system can instantly show you where your policy is strong and, more importantly, where your gaps are. It provides clear, evidence-linked answers that you can take straight to an auditor.
By automating evidence discovery and mapping, you do more than just speed up audit prep. You get a real-time, continuous view of your compliance posture. This means you can spot and fix weaknesses long before an auditor does, ensuring your access control policy is always ready for primetime.
Keeping Your Access Control Policy Effective and Audit-Ready
Getting your access control policy written and approved is a huge step, but it’s just the beginning. A policy is really just a document—its true value comes from how well it's enforced and maintained day in and day out. If you're not constantly monitoring and auditing, even the most carefully crafted rules will inevitably erode, leaving you exposed.
Think of it like a garden. You can’t just plant seeds and hope for the best; it needs regular attention to flourish. Your access control environment is the same. It requires consistent care to stay effective and, just as importantly, to be ready for an audit at a moment's notice.
Proving Your Policy Works: Evidence for Auditors
When an auditor walks through your door, they aren't going to simply accept your policy document as proof of security. They need to see hard evidence that you're actually following your own rules. Having this documentation organized and ready to go can transform a high-stress audit into a straightforward validation process.
So, what are auditors actually looking for? They'll want to see specific proof, including:
- Access Logs: These are the raw records from your systems, applications, and network gear that show who accessed what, where, and when.
- User Access Reviews: You'll need signed and dated reports from your regular reviews, where managers have personally confirmed that their team members have the correct permissions—and nothing more.
- Change Management Tickets: Show them the paper trail. Every request for new access, a change in permissions, or the removal of access should have a corresponding ticket with the proper approvals.
- Training Records: Auditors will want to see proof that your employees have actually been trained on the access control policy and know their responsibilities.
The Rhythm of Continuous Improvement
To keep your policy from going stale and prevent predictable security failures, you need to establish a consistent schedule for review and monitoring. This isn't about just passing an audit; it's about catching issues before they become real problems.
One of the biggest culprits we see is privilege creep, which happens when employees gradually collect access rights as they move between roles, long after they no longer need them. Another classic problem is dormant or orphan accounts—credentials that remain active after someone has left the company. Both are massive red flags for auditors and easy targets for attackers.
A static access control policy is an insecure one. The goal is to create a living security framework that adapts to organizational changes, evolving threats, and new compliance requirements.
The best way to fight this is to build a formal review cycle into your operations. A good starting point is to conduct quarterly reviews of all user access, but for high-privilege accounts like system administrators, you should be doing this monthly. These regular checks are your best tool for enforcing the principle of least privilege and showing you’re serious about due diligence. To understand this better, you can learn about the different types of tests of controls that auditors perform.
Don’t forget about technology's role here. Tools like Security Information and Event Management (SIEM) systems are incredibly helpful. They give you a real-time window into access events across your network, allowing you to spot policy violations or suspicious behavior right away. This kind of continuous monitoring is what turns a policy from a document on a shelf into a truly effective security practice.
Common Questions About Access Control Policies
Digging into the details of an access control policy often brings up a few key questions, especially when you're in the thick of writing or implementing one. Let's tackle some of the most common hurdles teams run into.
What's the Difference Between a Policy and an Access Control List (ACL)?
It’s incredibly common to mix these two up, but they operate on completely different levels.
Think of your access control policy as the constitution. It’s the high-level document that lays out the rules, principles, and philosophy for who gets access to what across the entire organization. It's the "why."
An Access Control List (ACL), on the other hand, is the specific, technical enforcement of those rules. It's a list of permissions bolted onto an actual resource—like a specific file, server, or application—that tells the system exactly who can do what (read, write, execute, etc.). The policy sets the strategy; the ACL is the tactical tool that gets the job done.
How Often Should We Review and Update Our Policy?
An access control policy can't be a "set it and forget it" document. The security landscape, your technology stack, and your business goals are constantly shifting, and your policy has to keep up.
As a rule of thumb, plan on a formal, deep-dive review of the entire policy at least once a year. But don't stop there. Individual user access rights need more frequent attention to prevent "privilege creep"—check them quarterly for standard users and monthly for anyone with elevated permissions.
Certain events should also trigger an immediate policy review, no matter when your last one was:
- A major security incident or data breach.
- New laws or industry regulations that affect you.
- Significant changes to the business, like a merger, acquisition, or major restructuring.
We're a Small Business. Where Do We Even Start?
If you're a small business, creating a formal policy from scratch can feel like a massive undertaking. The key is to not try and boil the ocean. Start small and focus on what matters most.
First, identify your crown jewels. What one or two systems would cause the most chaos if they were compromised? It might be your customer database, your financial records, or your core application.
Once you have your target, write a simple, one-page policy just for that asset. Define who absolutely needs access and apply the Principle of Least Privilege. This gives you a quick, tangible win and builds the foundation you can expand on later.
Ready to stop guessing and start knowing where your policies stand against compliance frameworks? AI Gap Analysis automates evidence discovery by reading your documents and mapping them to standards like ISO 27001, highlighting gaps in seconds. Streamline your audit preparation at https://ai-gap-analysis.com.