January 28, 2026
what is iso 27001 complianceiso 27001 certificationinformation securitycompliance guideannex a controls
What Is ISO 27001 Compliance? A Plain English Guide
What is ISO 27001 compliance? Learn how an ISMS works, understand Annex A controls, and see the clear steps to prepare for your ISO 27001 audit.
19 min readAI Gap Analysis

If you’re new to ISO 27001, the term "compliance" can sound a bit intimidating. In plain English, it just means your organization has built and is running a system to manage information security that meets the standard's specific rules. It's a comprehensive, business-wide commitment that brings together people, processes, and technology to keep your data safe and sound.
What ISO 27001 Compliance Really Means
Think of it this way: anyone can buy a high-tech security camera, but that doesn't make their house secure. ISO 27001 is the complete architectural blueprint for building a secure fortress from the ground up. The core of this blueprint is the Information Security Management System (ISMS).
Your ISMS is the living, breathing heart of your security program. It's the documented, risk-aware system that defines exactly how you protect information across the entire organization.
Getting "compliant" isn't a one-and-done task. It means you've successfully constructed this system and are committed to keeping it running. It's a continuous cycle of planning what you'll do, doing it, checking if it's working, and making it better.
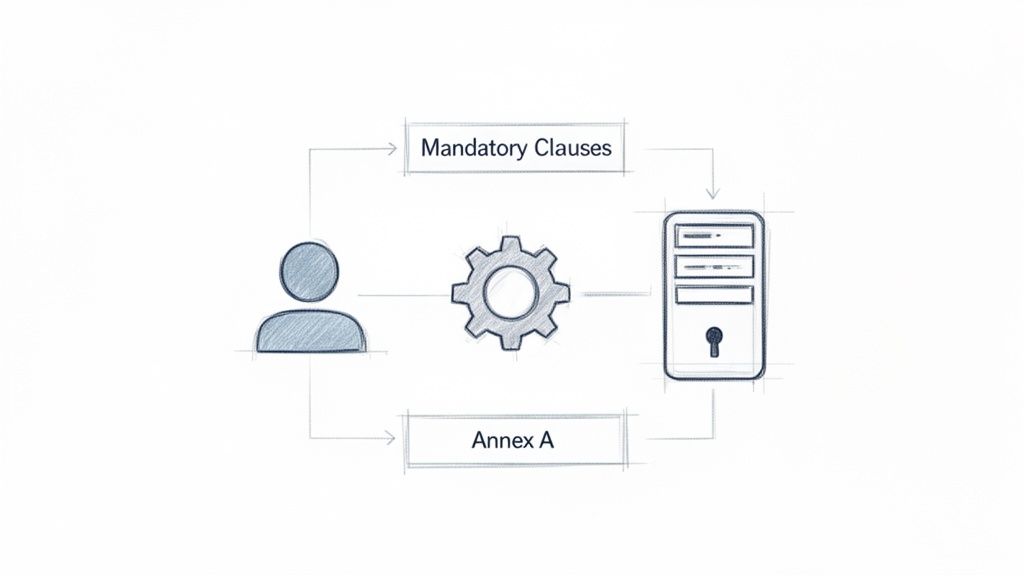
The Two Core Pillars of the Standard
To really get a handle on ISO 27001, you need to understand its two fundamental parts. They work hand-in-hand to create a security framework that's both rock-solid and flexible enough to fit your specific business.
This table breaks down the two main components of an ISMS that you need to address.
| Component | Purpose | Analogy |
|---|---|---|
| Mandatory Clauses (4-10) | These are the non-negotiable requirements that outline how to build, operate, and maintain the ISMS itself. They are the "what" and "why" of your security program. | Think of these as the building code for your fortress. They dictate the essential structural elements—the foundation, the wall thickness, the emergency exits—that every secure structure must have, no matter what it's protecting. |
| Annex A Controls | This is a reference list of 93 security controls that you can choose from to manage specific information security risks. They are the "how-to" solutions for your identified threats. | This is your security hardware catalog. It’s filled with different types of locks, surveillance systems, and reinforced doors. You don't install every single one; you pick the specific items that address the unique vulnerabilities of your fortress. |
Together, these two components give ISO 27001 its real strength.
The standard doesn't force a specific piece of software on you or tell you which firewall to buy. Instead, it provides a risk-based framework that empowers you to select the security controls that actually make sense for your operations and the threats you face.
This is why an ISMS for a small e-commerce shop will look very different from one for a multinational bank. Both must follow the same mandatory clauses (the building code), but they will choose very different Annex A controls (the security hardware) to protect what's most important to them. The end result is a security program that is both relevant and genuinely effective.
To go a level deeper, you can explore the complete ISO 27001 certification requirements in our detailed article.
Building Your Information Security Management System
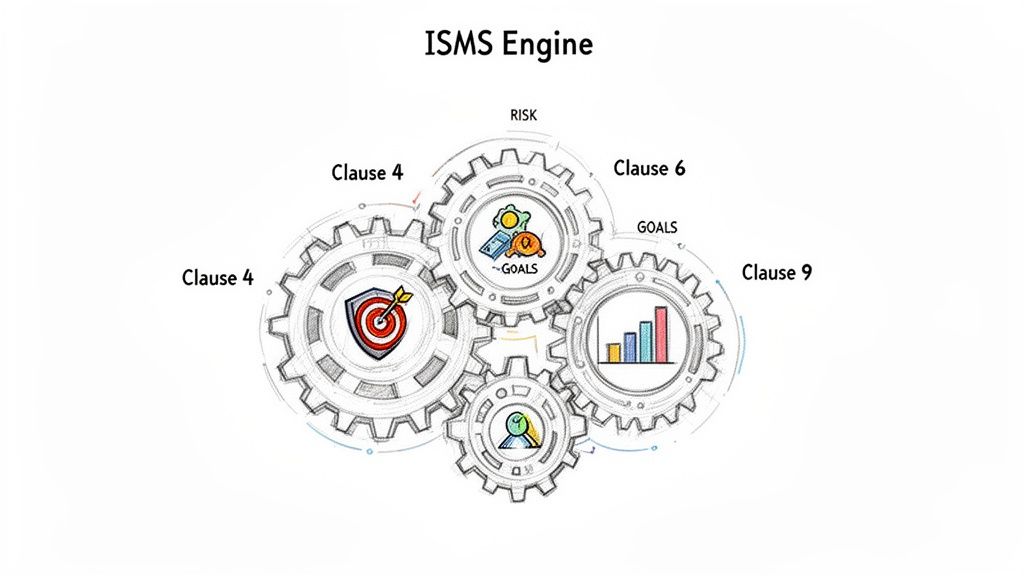
At the heart of ISO 27001 compliance is your Information Security Management System, or ISMS. Don't think of this as a piece of software you install. It's much bigger than that. Your ISMS is the strategic framework—the engine—that powers and steers your entire security program. It’s the systematic, documented way you manage your company’s sensitive data.
This engine is built according to a specific blueprint: Clauses 4 through 10 of the ISO 27001 standard. These aren't just bureaucratic hurdles. They are the core components that ensure your security efforts are effective, comprehensive, and actually support your business goals.
Understanding Your Organization's Context (Clause 4)
You can't protect what you don't understand. Before you do anything else, Clause 4 forces you to take a hard look at the world you operate in. This is about defining the "context of the organization"—pinpointing all the internal and external forces that could affect your information security.
This means asking some fundamental questions:
- Who are our interested parties? Think customers, employees, regulators, and investors. What do they expect from us when it comes to security?
- What are our internal challenges? Be honest about your company culture, the resources you have, and your existing technology stack.
- What external pressures are we facing? This could be anything from new privacy laws and competitor actions to emerging cyber threats.
Getting this right lays the foundation for everything else. It ensures your ISMS is tailored to your unique reality, not some generic template. This is also a key part of scoping your ISMS, a process you can dig into with our guide to conducting an ISO 27001 gap assessment.
Leadership and Planning (Clauses 5 & 6)
An ISMS without buy-in from the top is doomed from the start. Clause 5 (Leadership) makes it mandatory for top management to be actively involved. They need to show their support, provide resources, and make sure security is woven into the fabric of the business, not just bolted on. It’s about championing a culture of security, not just signing a check.
Once you have that backing, Clause 6 (Planning) is where you turn your high-level understanding into a concrete plan. This is where the formal risk assessment happens. You'll identify, analyze, and evaluate your information security risks and then set clear, measurable security objectives that align with what the business is trying to achieve.
For example, a risk might be "unauthorized access to customer data." A strong objective would be to "implement multi-factor authentication for all critical systems within the next quarter and reduce unauthorized access attempts by 90%."
Support, Operation, and Evaluation (Clauses 7, 8, & 9)
A great plan is useless without the resources to make it happen. Clause 7 (Support) ensures you have what you need to run your ISMS. This covers everything from making sure your people are competent and aware of their security duties to keeping all your processes properly documented.
Clause 8 (Operation) is the "get it done" phase. Here, you put your plans and controls into action, implementing the risk treatments you defined back in Clause 6 and managing your day-to-day security operations.
Clause 9 (Performance Evaluation) is the crucial "check" step in the cycle. It requires you to constantly monitor, measure, and analyze your security performance. This clause makes sure your ISMS is actually working by demanding internal audits and regular management reviews.
Driving Continual Improvement (Clause 10)
Finally, an ISMS is never "finished." Clause 10 (Improvement) embeds the idea of constant evolution into your security program. It requires you to fix any issues (nonconformities) you find during your evaluations and to continually make your ISMS better. It has to adapt to new threats, new technologies, and new business goals.
This structured, cyclical approach is why so many companies rely on ISO 27001. Recognized in over 150 countries, it has become a global standard for proving security maturity, helping to slash data breach costs and accelerate business partnerships.
Navigating the 93 Security Controls in Annex A
If the main clauses of ISO 27001 are the blueprint for your security program, then Annex A is the detailed catalog of tools and defenses you can choose from. Staring at a list of 93 security controls can feel overwhelming, but here's the most important thing to remember: you don't have to implement every single one.
Think of Annex A as a comprehensive menu of security best practices. The specific risks you uncovered back in your risk assessment (Clause 6) will tell you exactly which items to "order" from this menu. This approach is incredibly practical, ensuring your security measures are relevant, affordable, and aimed squarely at the threats you actually face.
Thankfully, the latest version of the standard groups these controls into four logical themes, making it much easier to see how everything fits together.
The Four Themes of Annex A Controls
These categories help organize your efforts, creating a clear structure for protecting your information from every angle—from boardroom policies all the way down to the code running on your servers.
- Organizational Controls (37 controls): This is the foundation. These are the big-picture controls that set up your security governance, covering things like policies, roles and responsibilities, and how you classify your information. Think of this as the strategic rulebook for your entire security program.
- People Controls (8 controls): At the end of the day, security comes down to people. This group is all about the human element, from background checks and security awareness training to your remote work policies. A fortress is only as strong as the people guarding the gates.
- Physical Controls (14 controls): These controls protect the physical spaces where your data is stored and handled. We're talking about securing offices, server rooms, and equipment from theft, damage, or anyone who shouldn't be there. This covers everything from keycard access to fire suppression systems.
- Technological Controls (34 controls): As the largest category, this is where the tech comes in. It covers the digital nuts and bolts of security, like access control, encryption, network security, secure development practices, and data backups. These are the digital locks, alarms, and firewalls defending your information.
Grouping the 93 controls this way provides a roadmap for building a defense that has multiple layers of protection.
Practical Examples from Each Theme
To bring this out of the clouds, let's look at a few real-world examples of what these controls look like in practice.
Organizational Control Example: A.5.1 Policies for Information Security
This is the very first control for a reason—it's your cornerstone. It simply means you need to define and write down your company's information security policies. These policies have to be approved by management and shared with everyone who needs to see them, setting the tone for security across the organization.
People Control Example: A.6.3 Information Security Awareness, Education, and Training
Your team is your first and best line of defense. This control is about making sure everyone in the company gets regular security training. This isn't just a one-off webinar; it's an ongoing program covering how to spot phishing attacks, why strong passwords matter, and how to handle sensitive data properly.
It's easy to make security training a check-the-box exercise. But with human error still a factor in over 80% of data breaches, an ongoing awareness program is one of the most effective security investments you can make.
Physical Control Example: A.7.2 Physical Entry
This one is straightforward: keep unauthorized people out of sensitive areas. In the real world, this looks like key card readers on server room doors, visitor sign-in logs at the front desk, and policies that prevent tailgating into secure zones.
Technological Control Example: A.8.24 Use of Cryptography
Cryptography is just a fancy word for scrambling data so it can't be read without a key. This control requires you to have a policy on when and how you use it. A perfect example is enabling full-disk encryption on all company laptops—if a device is lost or stolen, the data on it remains unreadable and secure.
Ultimately, Annex A gives you the flexibility to build a security program that is both strong and sensible. The goal is not to blindly implement all 93 controls, but to thoughtfully choose the ones that provide the right protection for your company’s most valuable information.
Your Path to ISO 27001 Certification
Getting ready for ISO 27001 certification often feels like studying for a big final exam. It takes a lot of structured prep work and a formal assessment at the end to prove you’ve got everything covered. The journey is a logical one, starting with a hard look at where you are today and ending with an audit that validates your entire security program.
But this isn't just about passing a test. It's about building a security posture that’s genuinely resilient and trustworthy. Every step is designed to make sure your Information Security Management System (ISMS) isn't just a set of documents, but a living, breathing part of your organization that actually works.
The First Steps: Gap Analysis and Scoping
The very first thing you need to do is a gap analysis. Think of it as a diagnostic quiz before you even start studying. It shows you exactly where the gaps are between your current security practices and what ISO 27001 demands. The result is a clear, actionable roadmap for the entire project.
Right after that, you’ll define the scope of your ISMS. This is a critical decision that determines which parts of your organization will fall under the ISMS umbrella. Are you certifying the whole company, or just a specific product line, department, or office? A well-defined scope keeps the project focused and prevents things from spiraling out of control later.
Risk Assessment and Bringing the ISMS to Life
With your scope locked in, it’s time to tackle the risk assessment. This is where you methodically identify, analyze, and evaluate all potential information security risks. The findings from this process feed directly into your Risk Treatment Plan, which spells out how you'll handle each risk—whether you decide to accept, avoid, transfer, or mitigate it using the Annex A controls.
Then comes the real work: ISMS implementation. Using your gap analysis and risk assessment as your guide, you'll start writing policies, defining procedures, and putting the necessary Annex A controls into place. This is where your security blueprint starts to become a functional reality.
The controls from Annex A fall into four main themes, which create layers of defense across your entire organization.
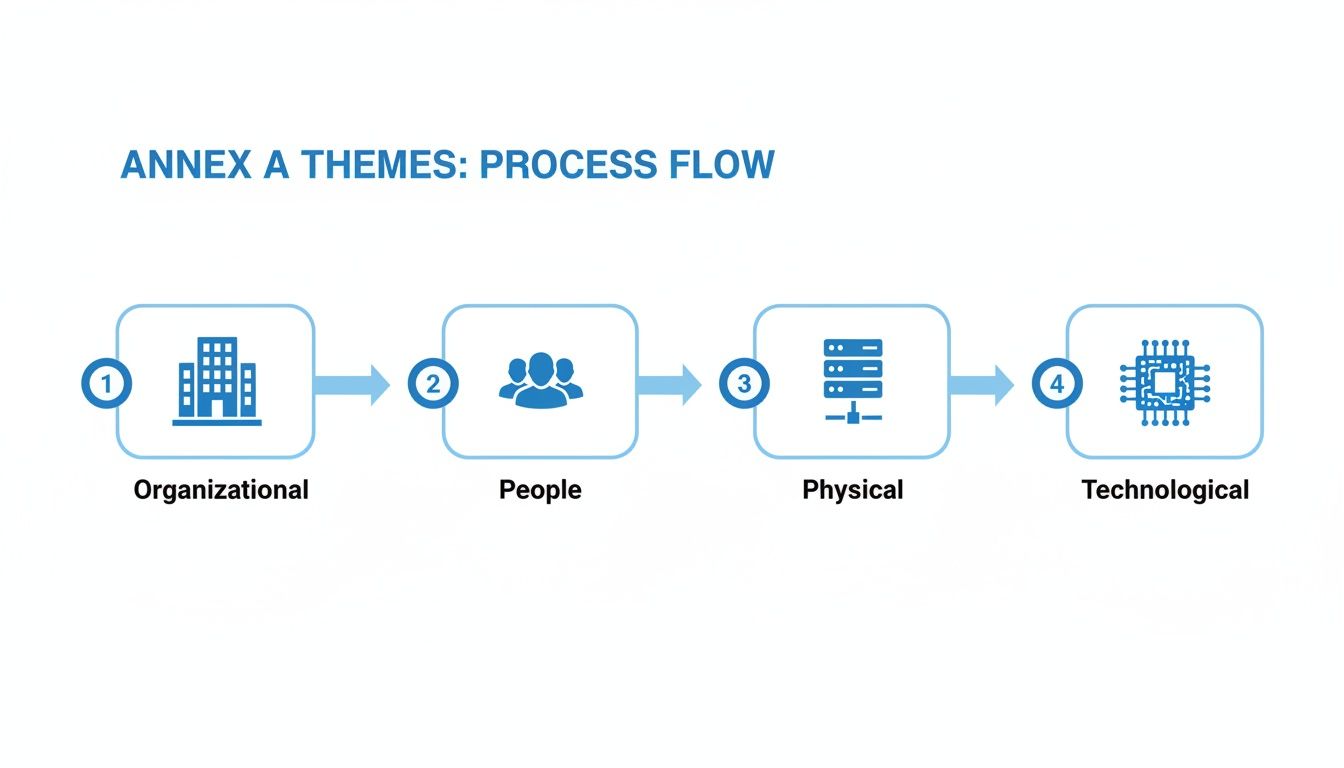
As you can see, these controls cover everything from how the organization is structured to the people within it, the physical environment, and the technology you use.
The Two-Stage Audit Process
Once your ISMS is up and running, it's time for a practice run—the internal audit. This is a self-assessment, either done by your own team or a third-party consultant, to check your readiness for the official audit. It's your last, best chance to find and fix any problems before the external auditors show up.
Finally, you have the formal certification audit, which unfolds in two distinct stages:
- Stage 1 Audit: The auditor focuses entirely on your documentation. They'll review things like your ISMS scope, risk assessment methodology, and key policies to make sure everything is designed correctly and ready for the main event.
- Stage 2 Audit: This is the deep dive. The auditor will be on-site (or virtual), interviewing your staff, examining records, and verifying that your security controls aren't just written down, but are actively working as intended.
If you pass both stages, you'll be awarded your ISO 27001 certificate. For a more detailed look at what's involved, check out our guide on the full ISO 27001 certification process.
Avoiding Common Pitfalls on Your Compliance Journey
Getting ready for an ISO 27001 audit is a big undertaking, and it’s easy to get tripped up along the way. Even companies with the best intentions run into the same, predictable roadblocks. Knowing what these hurdles are ahead of time is half the battle.
These common missteps can quickly turn a smart business decision into a draining, expensive ordeal. Let's walk through the most frequent mistakes so you can steer clear of them and make your path to certification as smooth as possible.
The "IT Project" Trap
One of the biggest mistakes we see is treating ISO 27001 like a one-and-done IT project. This mindset completely misses the whole point. An ISMS isn't something you install and forget; it's a living, breathing part of your business that needs constant attention and fine-tuning.
When security gets locked away in the IT department, it never truly becomes part of the company culture. Leaders from other departments will see it as "the IT team's problem," which means you'll struggle to get the cooperation and resources you need. This narrow view guarantees your ISMS will become obsolete, turning that expensive certificate into just a piece of paper on the wall.
So, how do you avoid this?
- Build a Cross-Functional Team: From the very beginning, create a steering committee with leaders from HR, legal, finance, and operations. This gets everyone invested and ensures you’re not working in a bubble.
- Connect Security to Business Outcomes: Don't just talk about firewalls and policies. Explain how a strong ISMS protects revenue, helps the sales team close deals, and reduces overall business risk. Frame it as a competitive edge, not a technical chore.
The Documentation and Evidence Nightmare
Another classic pitfall is creating beautiful-looking policies that have absolutely no connection to reality. Auditors are trained to spot this a mile away. They won't just read your documents; they'll ask for proof that people are actually following them.
If you don't have a solid system for collecting and organizing evidence, your audits will be a nightmare. Frantically digging for proof at the last minute is a surefire way to rack up non-conformities and fail your audit.
Key Takeaway: Your documentation has to be a mirror of your actual operations. An auditor should be able to point to any policy, ask for proof, and get a concrete piece of evidence—like a training log, a system alert, or a signed access form—right away.
This is why the conversation around compliance has shifted. For companies that are already certified, the top concerns are now supplier security (58%), business continuity management (55%), and risk management (47%). These are all areas where the link between policy and practice is absolutely critical. It's no wonder that investment in advanced tools is on the rise; you can explore more about these key topics shaping ISO 27001 in 2025.
Forgetting About Leadership and Letting the Scope Run Wild
Without real, visible support from the top, any ISO 27001 project is dead in the water. Your leadership team holds the keys to the budget, the resources, and the authority to get things done. If they aren't championing the effort, no one else will take it seriously.
Just as dangerous is "scope creep." If you don't nail down exactly what your ISMS covers from the start, the project will keep growing, burning through money and time with no end in sight. You have to be crystal clear about which departments, locations, systems, and assets are in scope. This keeps the project manageable and focused on protecting what matters most.
Common ISO 27001 Pitfalls and Strategic Solutions
To help you stay on track, we've put together a quick summary of the most common stumbles and how to sidestep them. Think of this as your field guide to avoiding unnecessary pain on your ISO 27001 journey.
| Common Pitfall | Why It Happens | How to Avoid It |
|---|---|---|
| Treating it as a one-off IT project | Security is viewed as a technical task, not a core business function. | Frame it as a strategic, business-wide initiative. Involve leaders from HR, legal, and finance from day one. |
| Weak management buy-in | Leadership doesn't see the direct link between security and business goals. | Quantify the risks and rewards. Present a business case focused on revenue protection, brand reputation, and sales enablement. |
| Poor documentation and evidence | Policies are written but not followed; evidence collection is an afterthought. | Implement a system to continuously collect evidence as you work. Treat your documentation as a living, operational guide. |
| An undefined or creeping scope | The initial boundaries of the ISMS are vague, leading to endless expansion. | Define a clear, defensible scope before you begin. Start with your most critical assets and expand methodically later. |
| Ignoring the "people" part | The focus is entirely on technology and processes, overlooking security awareness. | Develop an ongoing training program. Make security everyone's responsibility through regular communication and practical exercises. |
By keeping these points in mind, you're not just aiming for a certificate—you're building a resilient security culture that truly protects your organization.
Your Top ISO 27001 Questions, Answered
As you get closer to kicking off an ISO 27001 project, a few practical questions always bubble to the surface. Getting a handle on the timeline, key terms, and budget will help you map out a realistic plan and avoid surprises down the road. Let’s dig into the common questions we hear from people in your shoes.
How Long Does ISO 27001 Certification Take?
There's no magic number, but for a typical small or medium-sized business, you're looking at a timeline of 6 to 12 months. That window can shrink or expand based on a few critical factors.
- Your Starting Point: Are you starting from a solid foundation with good security habits already in place? Or from square one? A company with mature processes will get there much faster than one building everything from the ground up.
- Company Size and Complexity: A 50-person startup in one office has a much simpler path than a 500-person company with multiple international locations and intricate IT systems. More complexity means more time.
- Available Resources: This is a big one. Having a dedicated project manager, team buy-in, and a clear budget can dramatically cut down the timeline.
The whole process has several distinct phases, from the initial gap analysis all the way to the formal two-stage audit. Each one needs its own time and attention.
What Is the Difference Between Compliance and Certification?
This is a really important distinction, and it trips a lot of people up. I like to use a driver's license analogy.
Compliance is like knowing and following the rules of the road. You stop at stop signs, stick to the speed limit, and use your turn signals. For ISO 27001, being compliant means you've built your Information Security Management System (ISMS) and are running your security program according to the standard's rules.
Certification is the actual driver's license. It’s the official proof from an independent, third-party authority—the DMV in our analogy—that you've passed the test and know what you're doing. An accredited auditor comes in, inspects your ISMS, and if you pass, they issue a certificate that proves you're compliant.
You can be compliant without being certified, but you can't get certified without first being compliant. That certificate is the trusted, external validation that customers and partners are really looking for.
How Much Does ISO 27001 Certification Cost?
The total investment can vary wildly, but the costs typically break down into a few key buckets:
- Internal Resources: This is the time your own team spends on everything from risk assessments to policy writing and employee training. It's often the biggest cost, even if it doesn't show up on a single invoice.
- External Support (Optional): Many companies bring in consultants to guide them. Depending on the level of support, this can run anywhere from a few thousand to tens of thousands of dollars.
- Audit Fees: The certification body charges for the Stage 1 and Stage 2 audits, plus annual surveillance audits to keep your certificate active. For a small to mid-sized business, this often lands in the $10,000 to $25,000 range for the initial three-year cycle.
- Tools and Technology: You might need to invest in new security software, monitoring tools, or a platform to help you manage all the documentation and controls.
Can Software Help Manage ISO 27001 Compliance?
It absolutely can, and for many, it's a lifesaver. Modern Governance, Risk, and Compliance (GRC) platforms are built to wrangle the mountain of documentation and evidence that ISO 27001 demands. The right tool can help automate things like risk assessments, control monitoring, and internal audits.
But—and this is a big but—a tool is just that: a tool. It's an aid, not a replacement for human oversight. It can’t create your security culture for you, nor can it make strategic risk decisions. A platform is only as effective as the ISMS framework you build and the people who manage it.
Accelerate your readiness for any audit. AI Gap Analysis automates the painstaking process of evidence discovery, reading your documents and instantly mapping what you have against ISO 27001 requirements. Stop searching and start analyzing at https://ai-gap-analysis.com.