January 21, 2026
iso 27001 certification processisms implementationinformation security auditiso 27001 compliancerisk assessment
A Practical Guide to the ISO 27001 Certification Process
Navigate the ISO 27001 certification process with confidence. This practical guide covers scoping, risk assessment, audits, and maintaining compliance.
22 min readAI Gap Analysis

The journey to ISO 27001 certification is far more than a box-ticking exercise. It's a structured path to building a robust Information Security Management System (ISMS) that protects your company's most critical asset: its data. Think of it less as a technical chore and more as a strategic business decision that pays dividends in customer trust and enterprise sales.
Why Bother With the ISO 27001 Certification Process?
In a world where a single data breach can shatter a company's reputation overnight, simply saying you take security seriously isn't enough. You have to prove it. The ISO 27001 certification process offers a clear, globally respected framework to manage and protect your information assets. It’s a powerful signal to clients, partners, and regulators that your security posture is mature and reliable.
This guide isn't about reciting the standard. It’s about connecting the dots between the rigorous certification process and the real-world business advantages it creates.
Build Trust, Close Deals
Let's be blunt: ISO 27001 certification is one of the fastest ways to build credibility. When a potential enterprise customer sees that seal, a whole raft of their security concerns evaporate. It smooths out the sales cycle because you've already demonstrated a commitment to security that aligns with their own strict risk management policies.
The process I've seen play out time and again follows a simple, powerful logic.
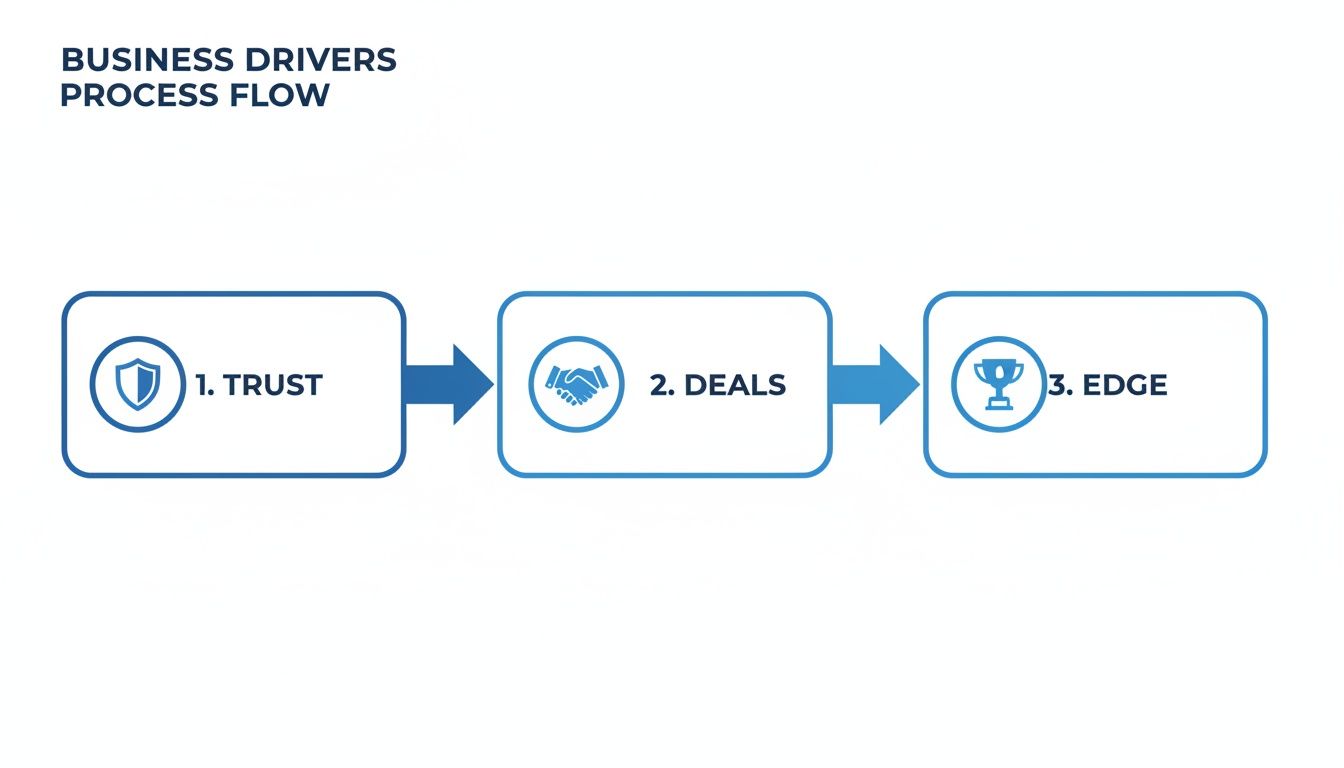
As you can see, establishing that baseline of trust through certification is the key that unlocks bigger deals and gives you a real competitive advantage.
A Framework That Keeps Getting Better
ISO 27001 isn't a one-and-done project. Its real power lies in embedding a culture of continual security improvement right into the DNA of your organization. The standard mandates regular risk assessments, internal audits, and management reviews, forcing your ISMS to adapt and evolve as new threats emerge. It’s a proactive stance that dramatically reduces the likelihood and impact of a security incident.
The demand for this kind of verified security is exploding. Valued at USD 18.59 billion in 2025, the global ISO 27001 certification market is expected to rocket to USD 74.56 billion by 2035. This incredible growth, tracked in detail by firms like Business Research Insights, shows just how critical the standard has become for companies wanting to prove their diligence.
At its heart, the ISO 27001 certification process turns information security from a siloed IT problem into a strategic business advantage. It gives everyone a common language for talking about risk and a reliable playbook for managing it.
As we'll walk through in this guide, the path to certification is detailed, but it's absolutely achievable. With the right roadmap and the right tools, any organization can navigate the process and unlock some very significant business rewards.
Defining Your Scope and Conducting a Gap Analysis
So, you're starting the ISO 27001 journey. The first move isn’t to start writing policies or buying new security tools. It's about drawing a map. This initial phase boils down to two critical tasks: defining the scope of your Information Security Management System (ISMS) and then running a thorough gap analysis.
Nail these two steps, and you've built a solid foundation. Get them wrong, and you're setting yourself up for wasted time, money, and a whole lot of frustration down the road.
What's In and What's Out? Defining Your Scope
Your scope is simply the boundary line for your ISMS. It answers the fundamental question: "What exactly are we trying to protect and get certified?" This isn't just a paperwork exercise—it has very real consequences.
Scope it too narrowly, and you might leave a critical system or data set unprotected, defeating the whole purpose. Scope it too broadly, and you'll bury your team under an avalanche of unnecessary work and ballooning costs.
Let's look at a couple of real-world examples. For a B2B SaaS company, the scope might be tightly focused on the cloud infrastructure, code repositories, and support systems directly tied to its main product. They could intentionally exclude internal corporate functions like HR or finance systems if those don't process customer data or impact service delivery.
On the other hand, a manufacturing firm might have a much wider scope. Their ISMS could need to cover not just their office network but also the Operational Technology (OT) on the factory floor, their supply chain management systems, and sensitive intellectual property in product design databases. The key is to protect what’s most critical to your specific business.
Taking Stock: The Gap Analysis
Once you’ve drawn your map, it’s time to figure out where you are right now. That’s what a gap analysis is for. Think of it as a comprehensive health check for your security posture. You're systematically comparing what you’re currently doing against the requirements of the ISO 27001 standard, especially the 93 controls listed in Annex A.
This process shines a bright light on your security gaps. The final report is your roadmap, showing you what's already solid, what needs a little tweaking, and where the major holes are that demand new policies, processes, or technology. For a deep dive, check out this guide on how to perform an effective ISO 27001 gap assessment.
Not long ago, this meant getting buried in spreadsheets and sitting through endless meetings, painstakingly trying to match company documents to the standard's clauses. It was slow, painful, and honestly, pretty easy to mess up.
A proper gap analysis isn't just about finding problems. It's about creating a prioritized, actionable plan for your ISMS implementation. It stops you from wasting effort on controls you already meet or that don't apply to your actual risks.
AI-Powered Gap Analysis: A Smarter Way Forward
Thankfully, we're not stuck in the spreadsheet era anymore. Modern compliance platforms have completely changed the game by using AI to automate the most grueling parts of a gap analysis. Instead of a team spending weeks manually reading through policies, you can now upload your entire evidence library—company wikis, PDFs, security reports—and let an AI do the heavy lifting.
This turns the gap analysis from a dreaded manual audit into a fast, data-driven process. The AI can instantly identify existing controls, point out the gaps, and even link its findings directly to the specific sentence in your documents. It saves a staggering amount of time—often hundreds of hours—and delivers a far more accurate baseline for the entire ISO 27001 certification process.
The human expert is still vital for validating the AI's findings and making the final strategic calls, but all that tedious, error-prone groundwork is now handled for you.
How Long Will ISO 27001 Certification Take?
One of the first questions everyone asks is, "How long will this take?" The honest answer is, it depends. The size and complexity of your organization are the biggest factors. A small startup with a simple tech stack will move much faster than a global enterprise with legacy systems and multiple business units.
To give you a realistic idea, here’s a breakdown of typical timelines based on company size. These are estimates, of course, but they provide a solid starting point for your planning.
| Phase | Small Business (Under 50 Employees) | Medium Business (50-250 Employees) | Large Enterprise (250+ Employees) |
|---|---|---|---|
| Preparation & Scoping | 2-4 weeks | 3-6 weeks | 6-12 weeks |
| Gap Analysis & Risk Assessment | 3-6 weeks | 4-8 weeks | 8-16 weeks |
| ISMS Implementation | 2-4 months | 3-6 months | 6-12+ months |
| Internal Audit & Review | 1-2 weeks | 2-4 weeks | 4-8 weeks |
| Stage 1 & 2 Audits | 2-4 weeks | 3-6 weeks | 4-8 weeks |
| Total Estimated Time | 3-6 Months | 6-9 Months | 9-18+ Months |
Remember, these timelines assume you have dedicated resources. If key personnel are juggling this project with their full-time jobs, expect to add more time to each phase. The key is to be realistic and plan accordingly.
Building Your ISMS: From Risk Assessment to Real-World Controls
Once your gap analysis has laid out the roadmap, it's time to roll up your sleeves and start building your Information Security Management System (ISMS). This is where the project really takes shape. It’s not about just ticking boxes or writing documents that will gather dust; it’s about constructing a security framework that actually works for your business and protects what matters most.
At the very heart of the entire ISO 27001 certification process is the risk assessment. Everything flows from this. It's the critical step where you translate security theory into tangible actions by identifying the specific threats and vulnerabilities that could hit your information assets.
Making Sense of the Risk Assessment
The term "risk assessment" can sound overly formal, but the logic behind it is refreshingly simple. You're just systematically figuring out what could go wrong, how likely it is to happen, and what the fallout would be. It boils down to asking practical, real-world questions.
Imagine you're a healthcare tech company. A critical risk might be "unauthorized access to patient data stored in our cloud database." The vulnerability? Maybe it's weak password policies or a lack of multi-factor authentication. The threat? A malicious actor trying to steal that data.
The process itself involves a few core activities:
- Identify Risks: Brainstorm what could go wrong. This covers everything from a ransomware attack and an employee accidentally emailing sensitive data, to a fire at your data center.
- Analyze Risks: For each risk, you’ll estimate the likelihood of it happening and the potential impact if it does. This is how you start to prioritize.
- Evaluate Risks: Based on your analysis, you’ll decide which risks are just too high to ignore and must be addressed.
You absolutely need a structured methodology for this. Whether it’s a simple high-medium-low scale or a more detailed numerical matrix, consistency is key to making sound decisions. If you want to dive deeper into this foundational step, you can learn more about crafting a comprehensive cybersecurity risk assessment.
From Risk to Selecting the Right Controls
After identifying your biggest risks, you have to decide what to do about them. This is what the standard calls risk treatment. For any given risk, you really only have four choices:
- Treat: This is the most common path. You implement security controls to lower the risk to an acceptable level.
- Tolerate: You formally accept the risk. This usually happens when the cost of fixing it is far greater than the potential damage.
- Transfer: You shift the financial burden of the risk to someone else, most often by buying a cybersecurity insurance policy.
- Terminate: You get rid of the risk entirely by stopping the activity that causes it (e.g., decommissioning a legacy system).
This decision-making process is what connects your risks directly to the 93 security controls listed in Annex A. Here’s a common mistake I see all the time: people think they have to implement every single one of those controls. That's just not true. You only pick and implement the controls that are necessary to treat your specific, identified risks.
For instance, if you’re a fully remote company with no physical office, you likely don't have risks related to physical security monitoring (A.7.4). You wouldn't implement that control, and your risk assessment is the proof that justifies that decision.
The goal is not to implement all 93 controls from Annex A. The goal is to implement the right controls that mitigate your specific, identified risks. Your risk assessment is the evidence that proves your choices are logical and justified.
Creating Your Statement of Applicability (SoA)
This leads you to one of the most important documents you'll create: the Statement of Applicability (SoA). Think of the SoA as your master inventory of all 93 Annex A controls and your organization's relationship to them.
For every single control, your SoA needs to clearly state three things:
- Is this control applicable to our ISMS? (Yes/No)
- If yes, have we implemented it?
- A short justification for including or excluding it.
A software company would absolutely mark control A.8.28 (Secure Coding) as applicable, confirm it’s implemented, and point to their secure development policy. In contrast, a small consulting firm that doesn't write any code would mark it as not applicable and state that as the reason. The "why" behind every decision comes straight from your risk assessment.
Documenting Your ISMS
Along with the SoA, you'll be creating a handful of other mandatory documents. While it can feel like a lot of paperwork, these documents are the foundation that gives your ISMS structure and clear rules of the road.
Some of the key documents you’ll need to write include:
- Information Security Policy: The high-level document, signed off by leadership, that shows your company's commitment.
- Risk Assessment and Treatment Methodology: Your playbook for how you perform risk assessments.
- Access Control Policy: The rules for who gets to see and do what with your data.
- Clear Desk and Clear Screen Policy: Practical rules to protect information in the office and at home.
The trick is to create documents that people will actually use—ones that reflect how your company truly operates. Grabbing a generic template off the internet is a recipe for failure. An ISMS that only exists on paper is worthless to an auditor and, more importantly, to your business. It has to be a living part of your day-to-day operations to be effective.
Mastering the Internal Audit and Management Review
Before you ever let an external auditor through the door, the ISO 27001 certification process demands you pass your own internal tests. This phase is built around two critical feedback loops: the internal audit and the management review. Don’t think of these as just more boxes to check. Treat them as a dress rehearsal—an invaluable chance to make sure you're truly ready for showtime.
Getting these internal steps right proves your Information Security Management System (ISMS) is a living, breathing part of your company, not just a folder of documents collecting dust.
The Internal Audit: Your Friendly Trial Run
The internal audit is your opportunity to step into the auditor's shoes. The goal here is simple but absolutely essential: methodically verify that your ISMS is working as intended and meeting all the requirements of the ISO 27001 standard. This is your best chance to find and fix any non-conformities before the official auditors do.
A common pitfall is not scheduling this early enough. You need time to act on the findings. Remember, the internal audit must be completed before your Stage 2 certification audit.
You’ve got a couple of options for who conducts it:
- Your own team: This can save money, but objectivity is non-negotiable. The people auditing can't audit their own work. Your head of IT, for instance, can't audit the very controls they are responsible for managing.
- An external consultant: This brings a fresh, expert set of eyes to the table. For companies going through this for the first time, it's often the best way to guarantee a thorough, unbiased review.
Whoever does the audit, the result is a formal report. This document will list out all the findings, detailing any non-conformities and highlighting opportunities for improvement.
The Strategic Management Review
Right after the internal audit comes another mandatory step: the management review. This isn't just another meeting on the calendar. It's a formal checkpoint where your top leadership sits down to assess the ISMS's performance and effectiveness. This is how you prove that information security has genuine executive buy-in and is being managed from the top down.
The agenda is pretty specific because it’s designed to answer one fundamental question: "Is our ISMS doing its job, and what can we do to make it better?"
The management review is the bridge that connects your ISMS to the company's overall business objectives. It elevates security from a technical silo to a strategic asset that leadership actively discusses and supports.
This meeting is where the real decisions happen. A productive review is fueled by solid data and clear inputs, ensuring everyone in the room has what they need to make informed choices.
A Typical Management Review Agenda
To be effective, the management review needs structure. While you can tailor the format, the discussion must cover a few key points that draw directly from your ISMS performance data.
- Follow-up on Previous Actions: First things first, what did we agree to do last time, and did we do it?
- Changes in the Business Context: Have any internal or external factors shifted? Think new regulations, new product launches, or market changes that could affect our security posture.
- Information Security Performance: This is the heart of the meeting. You'll want to cover:
- The findings from your recent internal audit.
- Feedback from customers, partners, or other stakeholders.
- The current status of your risk assessment and treatment plan.
- Hard data and metrics showing how you're tracking against your security objectives.
- Opportunities for Continual Improvement: Based on everything discussed, what concrete actions will we take to strengthen the ISMS?
The documented minutes from this meeting are gold. They, along with the assigned action items, become critical evidence for your external auditor, proving that your ISMS isn't just implemented—it's actively managed, measured, and continuously improved with full leadership backing.
Facing the Final Boss: The Stage 1 and Stage 2 Certification Audits
After all the prep work, this is it—the moment of truth. The external audit is the final hurdle, a thorough inspection conducted by an accredited certification body to see if your ISMS truly meets the ISO 27001 standard.
This whole process is split into two distinct parts: Stage 1 and Stage 2. It’s best to think of it as a two-act play. Stage 1 is the dress rehearsal; the auditor is just checking your script (your documentation) to see if you’ve designed a compliant ISMS on paper. Stage 2 is the main performance, where they watch everything in action to confirm your security controls are actually working in the real world.
The Stage 1 Audit: A Documentation Deep Dive
The Stage 1 audit is really a readiness check. An external auditor comes in to do a high-level review of your ISMS documentation, making sure it aligns with the structure and requirements of the ISO 27001 standard.
They aren't testing your controls yet. Instead, they’re confirming you have a solid, well-documented foundation to build on. This is your first impression, and it’s a golden opportunity to catch any major gaps before the much more intense Stage 2 audit kicks off.
Here’s what you absolutely need to have polished and ready for them:
- ISMS Scope Document: A crystal-clear definition of what’s in and what’s out.
- Information Security Policy: Your company's high-level commitment to security, signed off by top management.
- Risk Assessment and Treatment Plan: The full story of your risk analysis, from process to results.
- Statement of Applicability (SoA): The definitive list of all 93 Annex A controls, complete with justifications for why each one is included or excluded.
- Internal Audit Report & Management Review Minutes: Proof that you’ve already run through these critical internal checks and balances.
The Stage 2 Audit: The Main Event
This is where the rubber meets the road. The Stage 2 audit is a comprehensive, hands-on evaluation of your ISMS in practice. The auditor’s goal is to verify that your security controls aren't just pretty documents but are effectively implemented and operating just as you said they would.
Auditors have a few key methods for gathering the evidence they need:
- Interviews: They’ll talk to people across the business, from your engineers to HR staff, to understand how security policies translate into daily work.
- Observation: They might ask to watch a process happen live. For example, they could observe how a new employee is onboarded or how a visitor gets access to the office.
- Evidence Review: This means digging into records, logs, and system settings. They’ll want to see your firewall rules, access review logs, or records proving your team completed their security awareness training.
The demand for this certification is undeniably global. Interestingly, Asia now holds over 40% of all ISO 27001 certificates, with Europe close behind at about 35%. The Americas, with nearly 15% of certificates, are catching on fast, which really underscores the standard's worldwide importance. You can dig into more of this data on these global cybersecurity certification trends.
An Auditor's Pro Tip: Be honest and transparent. If an auditor asks something you don't know, just say so. Offer to find the right person who does know the answer. Trying to guess or give fuzzy information is a quick way to lose their confidence.
How to Handle Audit Findings
Don't panic if the auditor finds something. It's quite common for them to identify issues, which they'll classify as "non-conformities." How you respond is just as important as the finding itself. To get a better feel for what to expect, it’s worth reading up on the different phases of an ISO 27001 audit.
Findings typically fall into one of two buckets:
- Minor Non-conformity: Think of this as a small slip-up or an isolated incident that doesn’t threaten your whole ISMS. A classic example is a single user's access not being revoked quickly enough after they left the company. You'll just need to provide a corrective action plan.
- Major Non-conformity: This is a big deal. It points to a systemic failure, like if you skipped your internal audit entirely. A major finding is a showstopper for certification until you can prove you've completely fixed the root cause.
Once you’ve addressed every finding to the auditor's satisfaction, they will recommend you for certification. The certification body performs one final review, and with their approval, you’ll be issued your official ISO 27001 certificate.
Staying Certified: Keeping Your ISMS Alive and Kicking
Getting that ISO 27001 certificate framed on the wall feels great, but it’s not the end of the journey. Think of it as the starting gun, not the finish line. Your certification is just a snapshot, a moment in time proving you met the standard. The real work—and the real value—comes from treating your Information Security Management System (ISMS) as a living, breathing part of your company.
This whole process is built on a three-year cycle. Your certificate is valid for that long, but you can't just coast. To keep it, you'll have to pass annual surveillance audits in year one and year two.
These are like check-ups. They're less intense than the initial audit, but the auditor will definitely be making sure your ISMS is still running as it should and that you’re genuinely focused on improving. Once the three years are up, it’s time for a full recertification audit, which is pretty much a repeat of your original Stage 2 audit.
Making Continual Improvement Part of Your Culture
Day-to-day compliance isn’t just about ticking boxes; it's about weaving security into the very fabric of your company culture. You want to get to a place where security is everyone's job, not just the IT team's. This means keeping a few key activities on a regular rotation.
- Keep Your Risk Assessments Fresh: The threat landscape never sleeps. You should be running smaller, targeted risk assessments whenever something big changes—like launching a new service, onboarding a major vendor, or expanding into a new country.
- Train, Train, and Train Again: A once-a-year security awareness presentation is just not enough. We've seen great success with quarterly phishing simulations and quick, digestible training videos on new threats. It keeps security front-and-center for the whole team.
- Time Your Internal Audits Smartly: Don't scramble to do your internal audit a month before the surveillance audit. A much better approach is to schedule it about six or seven months after your main audit. This gives you a comfortable buffer to find and fix any issues without the pressure.
ISO 27001 is not a "one-and-done" project. It’s a permanent operational mindset. A surprisingly common mistake is letting the ISMS gather dust after certification, which is a surefire way to rack up non-conformities and jeopardize your status.
Your ISMS Needs to Grow with Your Business
Businesses change. People leave, new technologies are brought in, and company goals shift. Your ISMS has to keep pace with all of it. If it doesn't, it quickly becomes irrelevant and ineffective.
Let’s say your company acquires a smaller startup. You can't just assume your existing ISMS covers them. You’ll need to perform a whole new risk assessment to understand the threats specific to their environment. This will almost certainly lead to updates in your Statement of Applicability (SoA) as you apply new controls.
Taking this proactive approach is crucial. It shows auditors that your security posture is dynamic and responsive, which is exactly what they want to see. It’s the clearest sign that you’re managing the iso 27001 certification process as an ongoing commitment, not a one-time hurdle.
Burning Questions About the ISO 27001 Process
Getting into the weeds of ISO 27001 certification always sparks a few practical questions. Let's tackle some of the ones that come up time and time again to clear the air.
Do We Really Need to Implement All 93 Annex A Controls?
This is probably the most common question I hear, and the answer is a resounding no. Your journey is dictated by your risk assessment, not by a rigid checklist.
If a risk simply doesn't apply to your business, you don't need to implement the control designed to mitigate it. The key, however, is that you can't just ignore it. You must formally document and justify its exclusion in your Statement of Applicability (SoA). For instance, a fully remote company with no physical office space could justifiably exclude certain physical security controls.
What’s the Difference Between ISO 27001 and SOC 2?
People often lump these two together, but they're fundamentally different beasts.
- ISO 27001 is a certification. Think of it like a final exam—you either pass by conforming to the standard, or you fail.
- SOC 2 is an attestation. Here, an auditor provides a professional opinion on your controls. It's not a simple pass/fail; it's a report on the state of your security.
This is a critical distinction. ISO 27001's pass/fail nature and its status as an international standard often give it a broader, more global recognition.
How Long Does My Certificate Last?
Your ISO 27001 certificate is valid for three years. But don't pop the champagne and forget about it. This isn't a one-and-done deal.
To keep your certification active, you have to pass an annual surveillance audit in year one and year two. These are lighter-touch audits than the initial one, but they're designed to ensure your Information Security Management System (ISMS) is still running effectively and you're sticking to the plan.
Once you hit the end of the three-year cycle, you'll go through a full recertification audit to renew your certificate for another three years.
The big takeaway here is that ISO 27001 is cyclical. The standard is built around the idea of continual improvement, which means the work of maintaining and refining your ISMS is never truly finished. It's a long-term commitment to security.
This structure ensures that certified organizations don’t just hit the mark once. It forces you to consistently maintain your security posture and adapt to new threats and business changes as they happen.
Tired of manually sifting through documents? Accelerate your evidence discovery and breeze through your gap analysis. With AI Gap Analysis, you can instantly map your existing policies and procedures to ISO 27001 controls, spot the gaps in minutes, and get audit-ready faster. See how it works.