January 22, 2026
iso 27001 certification requirementsiso 27001 clausesisms frameworkannex a controlsinformation security compliance
Your Practical Guide to ISO 27001 Certification Requirements
Master the ISO 27001 certification requirements with our step-by-step guide. We simplify clauses 4-10, Annex A controls, and audit preparation.
23 min readAI Gap Analysis

The core of ISO 27001 certification is all about building and running a living, breathing Information Security Management System (ISMS). Think of it as a blueprint with two main parts: first, you construct the management framework, and then you install the specific security features needed to protect your data. Nail these two, and you’re demonstrating that your organization has a systematic, repeatable way to manage information security.
Decoding the ISO 27001 Blueprint
Getting started with ISO 27001 can feel a bit like trying to read a technical manual in another language. You'll run into terms like "clauses," "controls," and "risk treatment," but don't get intimidated. At its core, the standard is simply a logical framework for protecting your company’s most critical asset: its information.
The trick is to stop seeing it as a rigid checklist and start seeing it as a flexible guide for building a security-first culture.
And it seems more businesses are catching on. The adoption of ISO 27001 is exploding, with 81% of companies reporting they either have or plan to get certified in 2025—a huge jump from just 67% in 2024. As of 2024, there are roughly 96,000 valid certificates out there, which is a 65% increase in only four years. These numbers aren't just a trend; they show that ISO 27001 is quickly becoming a requirement to do business. For a deeper dive, you can explore more about these compliance statistics to see just how much the market expects it.
Core Components of Certification
To get a handle on the ISO 27001 certification requirements, it helps to break the standard down into its three main pillars. These pieces fit together to create a solid, functional ISMS.
Let's quickly summarize what each component does before we dive deeper.
Core Components of ISO 27001 Certification at a Glance
| Component | Purpose | Key Requirement |
|---|---|---|
| Management System Clauses (4-10) | To build and operate the ISMS itself. | Defines how to manage security—from leadership buy-in to continuous improvement. |
| Risk Assessment & Treatment | To identify and prioritize security threats. | The "engine" that drives decisions on which security measures are actually needed. |
| Annex A Controls | A reference list of security controls. | A menu of 93 potential safeguards to choose from based on your risk assessment. |
These three pillars work in tandem to ensure your security measures are not only comprehensive but also perfectly suited to your organization's specific needs.
Here’s a great visual that shows how these pieces connect.
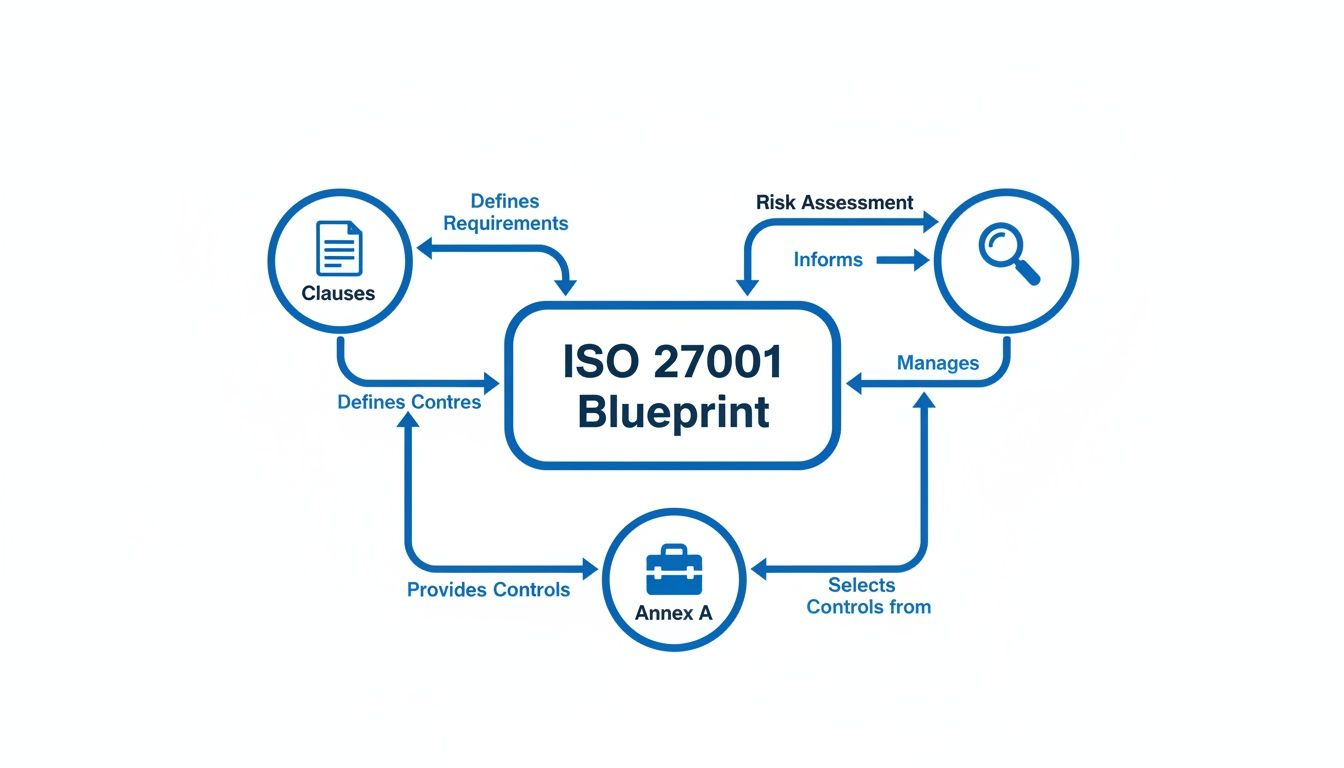
As you can see, the risk assessment is the central hub. It’s the process that links the high-level management rules in the clauses to the practical, on-the-ground security controls you’ll pick from Annex A.
An ISMS isn’t a "set it and forget it" project; it’s a living system. The whole point of ISO 27001 is to embed a cycle of planning, doing, checking, and acting into your company’s DNA. This continuous loop makes sure your defenses evolve right alongside emerging threats.
In this guide, we’ll walk through each of these areas, turning abstract requirements into concrete, actionable steps. We're here to demystify the process and show you exactly how to build your ISMS, choose the right controls, and gather the evidence you need to ace your certification audit.
Building Your ISMS with Clauses 4 Through 10
The real muscle behind your ISO 27001 certification isn’t a fancy firewall or some expensive new software. It’s the rock-solid management foundation you build using Clauses 4 through 10 of the standard. These aren't just recommendations; they are the mandatory blueprint for creating, running, and improving your Information Security Management System (ISMS).
Think of these clauses as the structural frame of a house. You can't just start hanging pictures on the walls or installing a high-tech alarm system until the foundation is poured and the frame is secure. In the same way, you can’t effectively implement the security controls from Annex A until your core ISMS framework is properly built.
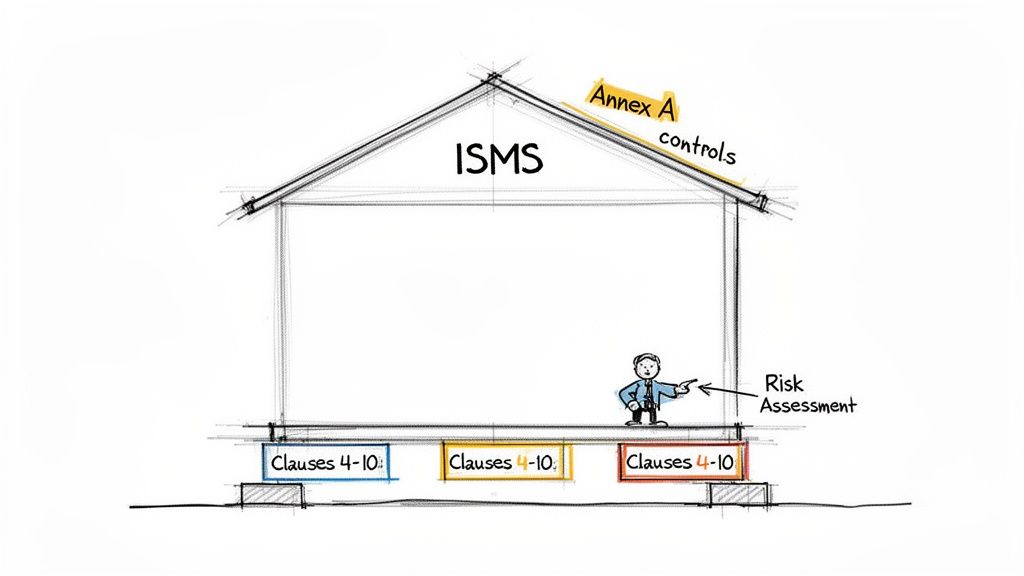
Each clause logically builds on the one before it. The process takes you from understanding your organization's unique place in the world all the way to proving you're serious about long-term improvement. Let’s break down what each clause actually asks of you in practical terms.
Clause 4: Understanding the Organization and Its Context
Before you can protect your information, you have to know what you’re protecting, who you’re protecting it for, and what challenges you face. Clause 4 is all about discovery, forcing you to look both inward at your company and outward at the world around you.
You’ll need to identify your interested parties—these are the people and groups who have a stake in your security. Think customers, employees, regulators, and even investors. What do they expect from you? A customer’s contract might demand ISO 27001 certification, while a regulator is focused on data privacy laws.
The final, crucial step here is defining the Scope of the ISMS. This document draws a crystal-clear boundary line. It specifies exactly which parts of your organization the ISMS covers—is it the whole company, a single product line, or just the London office? An auditor will use this scope document as a map to ensure your security efforts cover everything you promised.
Clause 5: Leadership and Commitment
Let's be blunt: an ISMS without genuine leadership buy-in is dead on arrival. Clause 5 is about demonstrating that top management isn't just giving a polite nod to security but is actively driving the initiative. This is one of the most critical ISO 27001 certification requirements.
An auditor needs to see hard evidence of this commitment, not just hear about it. This means having:
- A signed Information Security Policy: This is the high-level declaration from the top, setting the tone for the entire security program.
- Defined Roles and Responsibilities: Who owns what? A clear chart or document must show who is accountable for different parts of the ISMS.
- Resource Allocation: You need to prove that leadership has put its money where its mouth is by providing the budget and people to make the ISMS work.
An auditor will almost always want to speak directly with senior leaders. If your CEO can't articulate why the information security policy matters, it sends up a huge red flag.
Clause 6: Planning for the ISMS
With your scope set and leadership on board, Clause 6 is where the real strategy begins. This is where you map out your plan for managing information security risks. It's the strategic heart of your ISMS.
A key part of this is establishing clear information security objectives. Vague goals like "get better at security" won't cut it. Your objectives must be specific and measurable.
- Weak Objective: "We will improve our password security."
- Strong Objective: "We will reduce password-related security incidents by 25% over the next 12 months by rolling out multi-factor authentication for all critical systems."
This clause requires you to formally document how you'll achieve these objectives, complete with timelines and assigned responsibilities. This plan becomes a primary piece of evidence during your audit.
Clause 7: Support and Resources
An ISMS doesn't run on good intentions. It needs fuel. Clause 7 is about ensuring you have all the necessary support structures in place, from knowledgeable people to the right technology.
A huge piece of this is competence, awareness, and communication. You have to prove that your employees don't just know about the security policy, but that they also understand the specific role they play in making it a reality.
Evidence an auditor will look for includes:
- Records from your security awareness training sessions.
- A communication plan showing how security updates are shared.
- Job descriptions that explicitly list security responsibilities.
Clause 8: Operational Planning and Control
This is where the rubber meets the road. Clause 8 is about taking all the plans you made back in Clause 6 and putting them into action in your daily operations.
This clause is tightly linked to your risk assessment. If you identified phishing as a top risk, Clause 8 is where you would show the auditor your documented anti-phishing training campaigns and the email filtering tools you've deployed. The goal is to prove your security processes aren't just on paper—they're alive and functioning.
Clause 9: Performance Evaluation
How do you know if any of this is actually working? Clause 9 is all about measurement. It requires you to constantly monitor, measure, and evaluate your security performance to see what's effective and what isn't.
Two activities are non-negotiable here: internal audits and management reviews.
- Internal Audits: You have to audit yourself. The goal is to find weaknesses and nonconformities before the external auditor does. This is a mandatory, impartial health check for your ISMS.
- Management Reviews: Leadership must regularly sit down to review the ISMS performance, looking at key metrics, audit findings, and incident reports. The minutes from these meetings are vital evidence that your ISMS is being steered from the top.
Clause 10: Improvement
ISO 27001 is not a one-and-done project. It's about getting better over time. Clause 10 solidifies the principle of continual improvement. When something goes wrong (a "nonconformity"), you are required to have a systematic process for dealing with it.
This means you don't just patch the immediate problem. You have to conduct a root cause analysis to figure out why it happened in the first place. From there, you implement corrective actions to ensure it never happens again. A log of these issues and your fixes is exactly what an auditor wants to see—it proves your ISMS is a living system that learns and evolves.
Picking the Right Tools from Annex A
When people first lay eyes on Annex A of the ISO 27001 standard, it’s easy to feel a bit of panic. It looks like a rigid, non-negotiable checklist of 93 different security controls you have to implement. But that’s a common misconception, and thinking that way makes the whole process seem far more daunting than it really is.
The trick is to stop seeing Annex A as a list of rules and start seeing it as a professional’s toolkit. Think of a master carpenter—they have a workshop full of specialized tools, but they don't use every single one for every project. Instead, they carefully select the right tool for the job at hand. That's exactly how you should approach Annex A.
Your Risk Assessment Is the Blueprint
So, if Annex A is the toolkit, how do you know which tools to grab? Your guide is the risk assessment process we just covered. It acts as the blueprint for your security program, pinpointing your organization’s unique threats and vulnerabilities.
For every significant risk you uncover, you'll turn to Annex A to find the right control—or tool—to manage it. This isn't guesswork. The connection has to be direct and logical. You don’t just implement controls because they sound like a good idea; you implement them because your risk assessment proves they are essential. This is the exact logic you’ll walk an auditor through.
This entire selection process culminates in a crucial document called the Statement of Applicability (SoA). The SoA is your master list of all 93 controls from Annex A. For every single one, you have to document two things:
- Whether you’re using the control, explaining why it’s necessary by linking it directly back to a risk you identified.
- If you're not using it, you need to provide a solid justification for why it's not applicable to your organization.
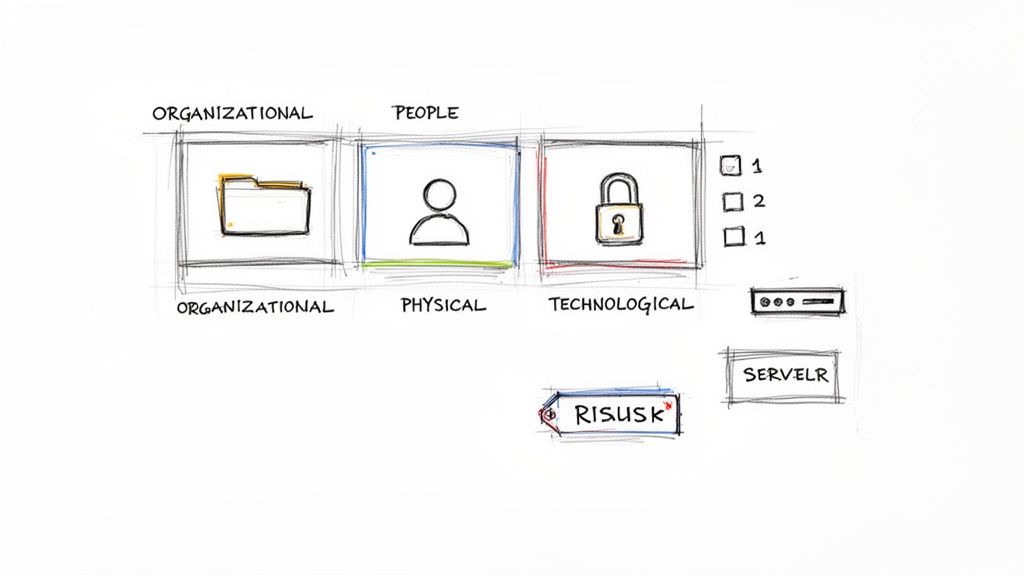
The Four Themes of Annex A Controls
To make this toolkit easier to sort through, the latest version of the standard (ISO 27001:2022) groups the 93 controls into four distinct themes. Getting familiar with these categories helps you think about security in a more holistic and organized way.
Let's break down what each theme is all about.
| Control Theme | Number of Controls | Core Focus |
|---|---|---|
| Organizational | 37 | The big-picture stuff: policies, governance, and the overall structure of your security program. |
| People | 8 | All about the human element—security awareness, responsibilities, and user behavior. |
| Physical | 14 | Protecting your tangible assets, like offices, server rooms, and company hardware. |
| Technological | 34 | The technical safeguards you build into your IT systems, networks, and applications. |
As you can see, a strong security program is about much more than just firewalls and antivirus software. It’s a complete strategy that covers policies, people, and places, too.
People Controls in Action
Let’s bring this to life with an example. The "People" theme has 8 controls focused on the human side of security—often the most vulnerable area. One of these is A.7.4 Physical security monitoring, which is all about keeping sensitive areas secure.
Imagine your risk assessment highlights a serious risk of an unauthorized person getting into your server room. This could lead to a data breach or equipment being stolen.
To tackle this risk, you decide to implement control A.7.4. The "tool" you choose from your kit might be installing security cameras covering the server room entrance and setting up a key card access system that logs who comes and goes. This concrete action directly reduces the risk you identified and demonstrates you're meeting the control's objective.
Technological Controls in Action
Now let's look at the "Technological" theme, which contains 34 controls. A classic and absolutely critical control here is A.8.2 Privileged access rights, which focuses on limiting who has powerful "admin" accounts.
Your risk assessment might flag the danger of too many employees having admin permissions in your company’s CRM system. This creates a huge risk, as one compromised account could lead to a massive data breach, or a simple mistake could wipe out critical customer information.
To treat this risk, you apply the A.8.2 control. Here’s what that looks like in the real world:
- You write up a formal access control policy that clearly defines who gets admin rights and under what circumstances.
- You then review every existing admin account and strip those permissions from anyone who doesn’t absolutely need them for their job.
- Finally, you put a new process in place where temporary admin access has to be formally requested and approved by a manager.
These actions are the practical application of the control. When the auditor asks how you're managing privileged access, you won't just talk about it—you'll show them the policy, the logs from your access review, and the approval workflow.
The main thing to remember is that Annex A tells you what controls are available, but it's your risk assessment that dictates the why and the how. This risk-based approach is the very heart of ISO 27001. It ensures your security program is smart, efficient, and built specifically for your organization's reality.
Driving Your Strategy with Risk Assessment
If you think of the ISO 27001 management clauses as the blueprint for your security program, then the risk assessment is its beating heart. It's the dynamic process that pumps life and logic into every security decision you make. Without it, your security controls are just expensive shots in the dark—guesswork that will quickly fall apart under an auditor's scrutiny.
This process is what flips your security posture from reactive to proactive. Instead of just putting out fires, you start to predict where they might break out. The whole point is to identify what could go wrong, figure out just how bad it could be, and then build a smart, targeted defense. An auditor wants to see this exact logic threaded through every part of your ISMS.
Identifying Your Most Critical Assets
Let's be realistic: you can't protect everything with the same level of intensity. The first step is to figure out what truly matters most to your business. In ISO terms, an information asset is anything that holds, processes, or transmits valuable information. This goes way beyond just databases and servers.
Your asset inventory will likely include things like:
- Customer data sitting in your CRM or cloud databases.
- Intellectual property, such as your secret sauce, source code, or proprietary designs.
- Employee records managed within your HR system.
- Physical hardware like laptops, servers, and networking gear.
- Key personnel—the people whose knowledge is irreplaceable.
Once you have this list, you can start to grasp the real-world impact if any of these assets were to be compromised, lost, or leaked.
Pinpointing Threats and Vulnerabilities
With your crown jewels identified, it’s time to think like an attacker. A threat is anything that could potentially harm an asset (like a hacker), while a vulnerability is a weakness that a threat could exploit (like an unpatched server).
A classic, and brutally effective, threat is the phishing attack. The vulnerability it preys on is simple human error—someone clicking a bad link. The outcome? A full-blown data breach.
The risk assessment process isn't about getting to zero risk—that’s a fantasy. It’s about understanding your risks so well that you can make informed, defensible decisions about which ones to accept, mitigate, transfer, or avoid.
This stage works best as a collaborative effort. Get people from IT, HR, and operations in a room to brainstorm a realistic picture of your threat landscape. You can learn more about how to structure this process in our guide to conducting a comprehensive cybersecurity risk assessment.
How to Evaluate and Score Risks
After you've listed out all the potential risks, you need a way to prioritize them. A simple risk matrix is a fantastic tool for this. It helps you evaluate each risk based on two core factors:
- Likelihood: How likely is this to actually happen? (e.g., rate it from 1-5, Rare to Almost Certain).
- Impact: If it does happen, how bad will the damage be? (e.g., rate it from 1-5, Insignificant to Catastrophic).
Multiply these two scores together, and you get a risk level. This simple math instantly creates a priority list, showing you exactly where to focus your limited time and resources. A high-likelihood, high-impact risk like a phishing attack that causes a major data breach is going to demand immediate attention. A low-likelihood, low-impact risk can wait.
Choosing Your Risk Treatment Strategy
Once your risks are scored and prioritized, you have to decide what to do about them. ISO 27001 outlines four clear options for risk treatment:
- Mitigate: This is the one you'll use most often. You implement a security control (usually from Annex A) to reduce the risk's likelihood or impact.
- Avoid: You completely stop the activity that's creating the risk. For example, if an old piece of software is riddled with vulnerabilities, you might just decommission it entirely.
- Transfer: You shift the financial burden of the risk to someone else. The most common example is buying cybersecurity insurance to cover the costs of a data breach.
- Accept: For very low-scoring risks, you might decide to do nothing. You simply document the business reason for accepting it and move on.
Let's go back to our phishing example. Let's say the risk of a breach from a successful phish scores high on your matrix. You decide to mitigate it. This is where you pull out your Annex A toolkit to find the right controls for the job. See how it all connects?
Your risk assessment provides the clear, logical justification for selecting specific controls, like:
- A.5.7 Threat intelligence: To stay on top of the latest phishing campaigns.
- A.6.3 Information security awareness, education, and training: To teach your team how to spot and report suspicious emails.
- A.8.23 Web filtering: To automatically block access to malicious sites linked in those emails.
This direct, documented line from an identified risk to a chosen control is exactly what an auditor is looking for. It proves your ISMS isn't just a random checklist of security gadgets, but a thoughtful, risk-driven system built to protect what matters most.
Preparing Your Evidence for a Successful Audit
Passing your ISO 27001 audit isn't about having impenetrable, perfect security. It's about proving you have a functioning, documented management system in place. The auditor’s role is simply to verify that what you claim on paper is actually happening in reality.
Think of it less like a final exam and more like building a case file for a detective. You need to provide the proof that solves the puzzle.
This evidence really comes in two flavors. First, there's the formal documented information the standard flat-out requires. Second, and just as critical, are the everyday records that show your Information Security Management System (ISMS) is a living, breathing part of your organization—not just a dusty binder on a shelf.
Assembling Your Mandatory Documentation
Some documents are completely non-negotiable. They are the bedrock of your ISMS, and an auditor will expect to see them right away, neatly organized and ready for review.
Your core package of evidence has to include:
- ISMS Scope Document: This clearly draws the line in the sand, defining which departments, locations, assets, and processes are covered by your ISMS.
- Information Security Policy: This is the high-level declaration from leadership. It sets the tone and direction for the entire security program.
- Risk Assessment and Treatment Process: This document outlines your specific methodology—how you find, analyze, and ultimately treat information security risks.
- Statement of Applicability (SoA): The master list. It details all 93 Annex A controls and justifies why each one is either included or excluded from your ISMS.
- Information Security Objectives: These are your specific, measurable goals for improving your security posture over time.
Having these polished and ready is your first big step toward a smooth audit. They form the spine of your evidence and prove you’ve built the proper framework. For a deeper dive into the audit experience itself, our guide on preparing for ISO 27001 audits has you covered.
Proving Your ISMS Is a Living System
Beyond the foundational policies, an auditor needs to see your ISMS in action. This means generating records and artifacts from your daily security activities. These are the footprints that prove your policies are being followed and your system is being actively managed.
Honestly, this is where many organizations stumble. They write beautiful, comprehensive documents but have no records to show they are actually being used.
An auditor's mantra might as well be, "If it's not written down, it didn't happen." Your records are what turn your documented plans into verifiable actions.
To build a strong case, concentrate on collecting evidence that shows the "Plan-Do-Check-Act" cycle is alive and well in your company. This is what truly brings your ISMS to life for an auditor.
Key Records and Artifacts to Collect
Your evidence folder should tell the story of your ISMS journey. These artifacts demonstrate measurement, review, and continuous improvement, which are exactly what auditors are looking for.
- Evidence of Competence: Think training logs, certifications, and updated job descriptions showing your team has the skills to manage security effectively.
- Monitoring and Measurement Results: This could be anything from security tool dashboards and vulnerability scan reports to logs that prove you're tracking performance against your objectives.
- Internal Audit Program and Results: You'll need your internal audit schedule, the final reports, and records of any nonconformities you discovered.
- Management Review Minutes: These are crucial. They need to be detailed notes from leadership meetings where ISMS performance was discussed, decisions were made, and actions were assigned.
- Corrective Action Logs: This is your log of nonconformities (from audits, incidents, etc.) and the documented steps you took to find the root cause and fix the problem for good.
The audit landscape has only gotten tougher. Since the standard was first published back in 2005, it has gone through major updates. Now, organizations must transition to the ISO 27001:2022 version by October 31, 2025. Reflecting this rigor, recent data shows 92% of organizations ran at least two audits last year, with 58% conducting four or more. You can discover more insights about 20 years of ISO 27001 evolution.
Your Step-By-Step Plan from Gap to Certification
Knowing the ISO 27001 certification requirements is one thing, but turning that knowledge into a successful audit is another challenge entirely. The key is having a clear, actionable plan. This roadmap will break down the journey into manageable steps, guiding you from your initial assessment all the way to certification.
Think of this as the project plan for building your Information Security Management System (ISMS). And like any good project, it starts with understanding your baseline. You have to know where you are before you can figure out how to get where you need to go.

Begin With a Gap Analysis
Your first move, without question, should be a gap analysis. This is where you hold up your current security practices against the mirror of the ISO 27001 standard. The process is designed to show you exactly where your controls and documentation fall short, giving you a clear, prioritized to-do list.
A solid gap analysis is the bedrock of your entire project. To make sure you start on the right foot, check out our detailed guide on running an effective ISO 27001 gap assessment.
Secure Leadership and Define Scope
Once you know your gaps, you can build a compelling business case to get genuine buy-in and resources from your leadership team. This is also the perfect time to formalize the Scope of the ISMS. This mandatory document clearly defines the boundaries of your security program.
Your ISMS Scope is the map you hand to the auditor. A clearly defined scope prevents "scope creep" during the audit and ensures everyone agrees on what, exactly, is being assessed.
Execute Your Risk Assessment and Treatment
This is where the strategic work really happens. Following the risk assessment methodology you’ve already defined, you’ll begin to identify, analyze, and evaluate your organization’s information security risks. It's a deep dive into what could go wrong.
The output of that assessment is your Risk Treatment Plan. This plan spells out precisely which Annex A controls you'll use to bring unacceptable risks down to an acceptable level. It’s a primary piece of evidence that shows the auditor your decision-making process.
Implement Controls and Gather Evidence
Now it’s time to get your hands dirty. This phase is all about rolling out the controls you selected, updating your processes, and training your team on the new way of doing things. But as you implement, you have to be disciplined about collecting evidence.
This means taking configuration screenshots, keeping training logs, and saving signed policy documents. You need to prove that your controls aren't just on paper—they're actually working.
Conduct the Internal Audit and Management Review
Before the external auditor shows up, you need to audit yourself. The internal audit is your chance to kick the tires on your ISMS, checking for compliance and effectiveness. It’s a dress rehearsal for the main event.
After that, you’ll hold a management review meeting. This is where leadership gets fully briefed on the ISMS performance, the internal audit findings, and any lingering issues. The meeting minutes from this review are critical evidence you’ll need for your Stage 1 audit. This final internal check is what tells you you're truly ready for certification.
Your ISO 27001 Questions, Answered
How Long Will It Take to Get ISO 27001 Certified?
This is the classic "how long is a piece of string?" question. The honest answer is: it depends entirely on your company's size, complexity, and how mature your existing security practices are.
A smaller, agile startup might sprint through the process in as little as 3-6 months. On the other hand, a large, complex enterprise with multiple departments and legacy systems should probably budget for 12 months or more. The real bottlenecks are always the same: conducting the gap analysis, actually implementing the controls you're missing, and then gathering all the necessary proof for the auditor.
How Is ISO 27001 Different From SOC 2?
This is a common point of confusion, but the distinction is pretty clear once you get it. Think of ISO 27001 as a top-down, holistic framework for managing information security across your entire organization. You build an Information Security Management System (ISMS), get audited, and you either pass or fail. If you pass, you get a certification that’s valid for three years.
SOC 2 is different. It’s an American standard that results in an attestation report, not a certificate. An auditor examines your controls based on specific "Trust Services Criteria" you select (like security, availability, confidentiality, etc.) and then writes a detailed report on their findings. It’s less about having a management system and more about proving your specific controls work as described.
Is ISO 27001 Legally Required?
Nope, ISO 27001 is not a law. You won't get fined by the government for not having it.
However, in the real world, it's often a non-negotiable contractual requirement. If you want to land enterprise clients or work in sensitive industries like finance, healthcare, or government contracting, you'll find that they won't even consider doing business with you without it. It has become the globally recognized way to prove you take security seriously.
Accelerate your path to certification by automating your evidence discovery. AI Gap Analysis reads your documents and instantly maps them to ISO 27001 requirements, turning weeks of manual work into hours. See how it works at https://ai-gap-analysis.com.