January 30, 2026
information security policyISO 27001 compliancecybersecurity policydata protectionGRC framework
Creating an Information Security Policy That Actually Works
Build a robust information security policy with our step-by-step guide. Learn to define controls, meet compliance, and protect your most valuable assets.
21 min readAI Gap Analysis

Think of an information security policy as the constitution for your company's data. It’s a formal set of rules that dictates how your organization will protect its digital assets and sensitive information. In simple terms, it tells everyone what they can and can’t do with company data and systems.
This isn't just an IT document; it's the strategic blueprint for your entire security program.
What Is an Information Security Policy and Why It Matters
Imagine trying to build a secure facility without architectural plans. You might install strong locks and reinforced walls, but you'd likely end up with security blind spots, confusing emergency exits, and no clear process for managing access. That's what running a business without an information security policy (ISP) is like.
This policy is a high-level guide that touches everyone, from the executive team down to the newest intern. It’s designed to embed security into your company culture by clearly defining roles, responsibilities, and the expected behaviors for handling information.
But a great policy does more than just list rules—it becomes a tool for building your business. When you can show customers and partners that you have a documented commitment to protecting their data, you build trust. In many industries, the lack of a formal security policy is an immediate deal-breaker.
The Foundation of Trust and Compliance
At its core, an ISP is built to protect the Confidentiality, Integrity, and Availability of information. This is often called the "CIA Triad," and it's the bedrock of information security. You need to keep data private, ensure it's accurate, and make sure people can get to it when they're supposed to.
But the policy's role goes much deeper. It's the cornerstone of your compliance efforts. If you're aiming for certifications like ISO 27001, HIPAA, or SOC 2, your information security policy is the first piece of evidence auditors will ask for. It’s the central document that connects all your technical controls and operational procedures back to a single, unified strategy.
An effective information security policy isn't just a list of "don'ts." It's a strategic document that aligns your security measures with your business goals, turning security from a cost center into a competitive advantage.
For anyone in a leadership or management role, the policy makes life easier. It creates a clear framework for making tough decisions, whether you're evaluating a new software vendor, managing third-party risk, or responding to a security incident. Instead of guessing, your team has an authoritative guide to follow.
Core Objectives of an Information Security Policy
To put it all together, a well-defined policy is built around a few fundamental goals. The table below breaks down the primary objectives, which you'll often see referred to as the "CIA Triad" plus the crucial element of accountability.
| Objective | Description |
|---|---|
| Confidentiality | This is about secrecy—ensuring that information is only seen by authorized people. It’s what prevents data leaks and protects privacy. |
| Integrity | This guarantees that your data is accurate and trustworthy. It prevents unauthorized changes, whether malicious or accidental. |
| Availability | This ensures that your systems and data are up and running for authorized users when they need them. It's the key to business continuity. |
| Accountability | This ties actions to individuals. It establishes clear ownership for information assets so that every action can be traced back to who did it. |
These four pillars are what give your security program its structure and purpose, ensuring that every control you implement serves a clear business-driven objective.
The Three Pillars of an Effective Security Policy
A truly effective security policy isn't just about the latest software or fanciest firewall. It’s built on a foundation of three distinct, yet deeply connected, pillars. Get one wrong, and the whole structure becomes wobbly.
Think of it like building a fortress. You need more than just high walls. You also need well-trained guards who know the rules and strong gates to control who comes and goes. Security works the same way.
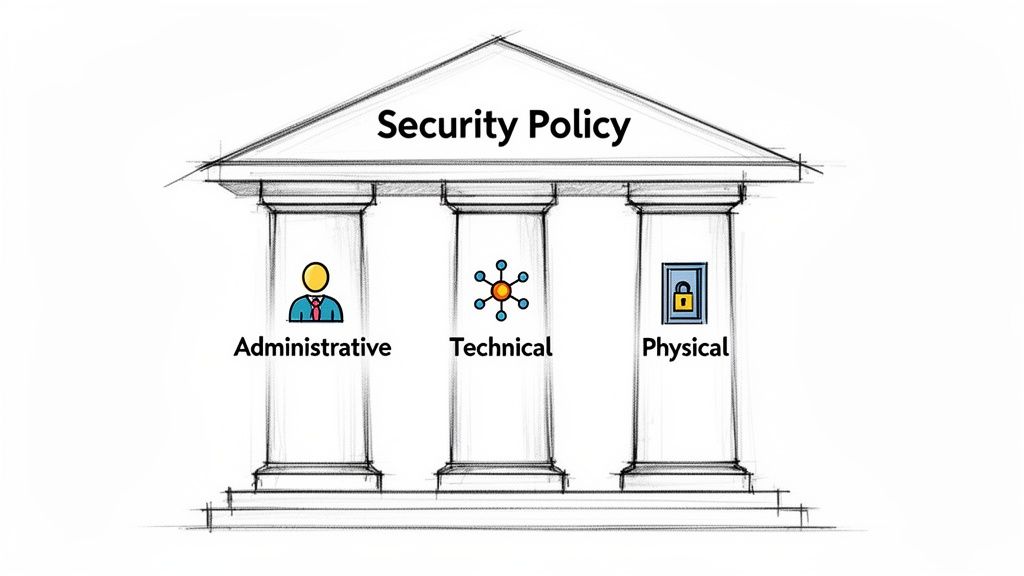
These three pillars are Administrative Controls, Technical Controls, and Physical Controls. When they work in harmony, you create a robust, layered defense where a failure in one area can be caught by another.
Administrative Controls: The Human Element
Let’s start with the people. Administrative controls are all about the rules, procedures, and day-to-day practices that guide how your team handles information. This is where you set the "who, what, when, and why" for your entire security program.
At its core, this pillar is about managing human risk. A state-of-the-art firewall is useless if an employee accidentally emails a customer list to a competitor. Good administrative controls build a security-first culture to prevent exactly that.
Key examples of administrative controls include:
- Security Awareness Training: This is non-negotiable. Regular training teaches employees how to spot phishing emails, handle sensitive information correctly, and follow security protocols.
- Risk Assessments: These are formal processes for hunting down, analyzing, and grading potential security threats to your business. We actually have a detailed guide on how to conduct a cybersecurity risk assessment.
- Vendor Management Policies: You need clear rules for vetting and keeping an eye on third-party suppliers who touch your data or systems.
- Incident Response Plans: A playbook for what to do when a breach happens. It's about minimizing the damage and getting back on your feet—fast.
Think of these policies as the brain of your security operations. They guide every single decision.
Technical Controls: The Digital Defenses
While administrative controls steer your people, technical controls are what protect your actual systems. This is the hardware and software you put in place to guard your digital assets—the digital locks, alarms, and surveillance systems for your network.
This is the stuff most people picture when they hear "cybersecurity." Technical controls are the tools that actually enforce the rules you’ve laid out in your administrative policies.
Common technical controls include:
- Firewalls and Intrusion Detection Systems: These are your digital gatekeepers, constantly watching network traffic to spot and block anything that looks malicious.
- Encryption: This involves scrambling data so it's completely unreadable without the right key. It protects information whether it's sitting on a server (at rest) or flying across the internet (in transit).
- Multi-Factor Authentication (MFA): This simple but powerful control requires users to provide a second piece of evidence (like a code from their phone) to log in, making stolen passwords almost useless.
- Access Control Lists (ACLs): These are the rules that dictate exactly who can access what, enforcing the critical principle of "least privilege."
These controls are the digital muscle that actively defends your IT infrastructure.
Physical Controls: Securing The Real World
The final pillar is all about protecting your tangible assets—everything from the server room down to individual laptops and paper files. It’s easy to get so focused on digital threats that you forget about the physical world, but a stolen server is just as catastrophic as a data breach.
Physical security is simply about stopping unauthorized people from getting their hands on your equipment and facilities.
Your digital fortress is only as strong as the physical locks on its doors. A sophisticated firewall is useless if an attacker can simply walk into your server room and unplug it.
Essential physical controls cover a few key areas:
- Secure Facility Access: Using things like key cards, biometric scanners, or security guards to control who gets into your buildings, especially sensitive spots like data centers.
- Equipment Security: This can be as simple as locking server racks and using cable locks on laptops to prevent theft.
- Clean Desk Policy: An administrative rule with a physical result, this policy requires employees to clear their desks of sensitive documents at the end of the day.
The need for a comprehensive approach is clearer than ever. By 2025, it's estimated that 35% of data breaches will come from third parties, which underscores the importance of administrative controls like solid vendor management. At the same time, while 87% of organizations are using multiple clouds, only 26% have adequate security tools in place—a glaring gap in technical controls. You can find more insights on these security policy trends on SecurityScorecard.com.
How to Structure an Information Security Policy That Actually Works
A good information security policy is more than just a list of rules; it's a blueprint for protecting your entire company. If it's a jumbled mess, it’ll just collect dust. But if it's well-organized, it becomes a practical guide that your team can actually use and that auditors will respect.
Think of it like building a house. You wouldn't just start throwing up walls randomly. You’d start with a solid foundation and a clear architectural plan. Your policy needs that same logical structure to be effective and easy to follow.
Start with the "Why" and "Who": Purpose and Scope
Every policy needs to begin by answering two simple questions: why does this exist, and who does it apply to?
The Purpose section is your mission statement. In plain English, it should state the policy's main goals—usually, this boils down to protecting the confidentiality, integrity, and availability of the company's information. No jargon, just a clear statement of intent.
Next, the Scope section draws the boundaries. It needs to be crystal clear about who and what is covered. This means everyone from full-time employees and contractors to third-party vendors, and all assets from company data and systems to networks and physical offices. Getting this right from the start eliminates confusion down the road.
Define What Success Looks Like: Security Objectives
Once you've established the "why," it's time to get specific about your goals. The Information Security Objectives section turns your broad purpose into concrete, measurable targets. These are the real-world outcomes you're aiming for.
Good objectives aren't vague. They look something like this:
- Cut down on phishing-related security incidents by 30% this year by rolling out new mandatory training.
- Maintain 99.9% uptime for all critical business systems, as defined in our Business Continuity Plan.
- Get our access controls fully compliant with ISO 27001 by the end of Q4.
Notice a pattern? They are specific, measurable, achievable, relevant, and time-bound (SMART). These objectives become the yardstick you use to measure how well your security program is actually performing.
Lay Down the Rules of the Road
With your objectives in place, the next few sections get into the nitty-gritty. These are the core rules that guide day-to-day work and form the backbone of your policy.
Acceptable Use Policy (AUP)
This is probably the section your employees will interact with the most. It sets the ground rules for using company tech. It answers everyday questions like, "Can I connect my personal phone to the office Wi-Fi?" or "Am I allowed to install that design software on my work laptop?" A clear and reasonable AUP is your first line of defense against simple human error.
Data Classification
Let's be honest, not all data is created equal. Your customer's credit card numbers are a lot more sensitive than the menu for the company cafeteria. The Data Classification section creates a simple tier system based on sensitivity.
A typical structure might be:
- Public: Information that's fine for anyone to see.
- Internal: Everyday business data, not for public eyes but not highly sensitive.
- Confidential: Sensitive information that could cause some damage if it got out.
- Restricted: The real crown jewels—PII, trade secrets, etc.—that would cause serious harm if compromised.
This framework is crucial because it dictates the security controls needed for each data type, from how it's stored to who can access it.
Access Control
This section is all about the principle of least privilege. It lays out the process for who gets access to what, how that access is reviewed, and how it’s removed when someone leaves. The rule is simple: people should only have the bare minimum access they need to do their jobs. Nothing more.
Think of a well-defined Access Control policy as the bouncer for your company's most valuable information. It ensures only the right people get past the velvet rope, at the right time, and for the right reasons.
Plan for When Things Go Wrong
No matter how good your defenses are, you have to assume that someday, something will go wrong. A strong policy is proactive and has a plan ready for the worst-case scenario.
The Incident Response section is your playbook for a security breach. It outlines the step-by-step process for detecting, containing, and recovering from an incident. It should clearly define what counts as an "incident," who needs to be on the response team, and how to conduct a post-mortem to learn from what happened.
Finally, the Roles and Responsibilities section makes it clear who owns what. From the CISO to every single employee, this section assigns specific security duties. When everyone knows what they're responsible for, things actually get done.
Mapping Your Policy to Compliance Frameworks Like ISO 27001
An information security policy isn't just an internal document collecting digital dust. It's your master key for compliance. A well-crafted policy acts as the central pillar for proving you meet demanding standards like ISO 27001, HIPAA, or SOC 2. It’s how you turn internal company rules into auditable evidence of control.
Think of it like this: compliance frameworks give you the exam questions, and your policy provides the answers. When an auditor asks how you govern access to sensitive data, you don’t just point to a piece of software. You show them your Access Control section, which lays out the principles, processes, and responsibilities your organization lives by.
This shifts your policy from a passive document to an active, strategic asset. For any Governance, Risk, and Compliance (GRC) team, this is a game-changer. It creates a clear, defensible story about your security posture, satisfying auditors and proving a mature commitment to protecting information.
Connecting Policy Sections to Framework Controls
The real "aha!" moment comes when you see how the core sections of your policy map directly to specific controls within these frameworks. It's often a surprisingly direct relationship that takes the pain out of the audit process. Instead of scrambling to find evidence last minute, you already have the roadmap.
Here’s a quick look at how common policy sections line up with a standard like ISO 27001:
- Access Control Policy: This directly addresses the entire A.9 family of controls in ISO 27001, covering everything from user registration and de-provisioning to enforcing the principle of least privilege.
- Incident Response Plan: This is your proof for the controls in A.16, which outlines the requirements for managing information security incidents and making improvements.
- Data Classification Policy: This aligns perfectly with control A.8.2, which mandates that information is classified based on its value, legal requirements, and sensitivity.
- Roles and Responsibilities: This forms the foundation for A.7, the section on human resource security. It ensures everyone understands their security duties before they start, during their employment, and after they leave.
This direct mapping is what it truly means to be audit-ready. Your policy becomes the central index for all your security activities.
An auditor doesn't just want to see that you have a firewall. They want to see the policy that governs its configuration, the procedures for updating its rules, and the records of its reviews. Your policy is the source of truth that ties it all together.
This simple concept map shows how a policy's core components—its scope, rules, and roles—create the foundation for any structured security program.
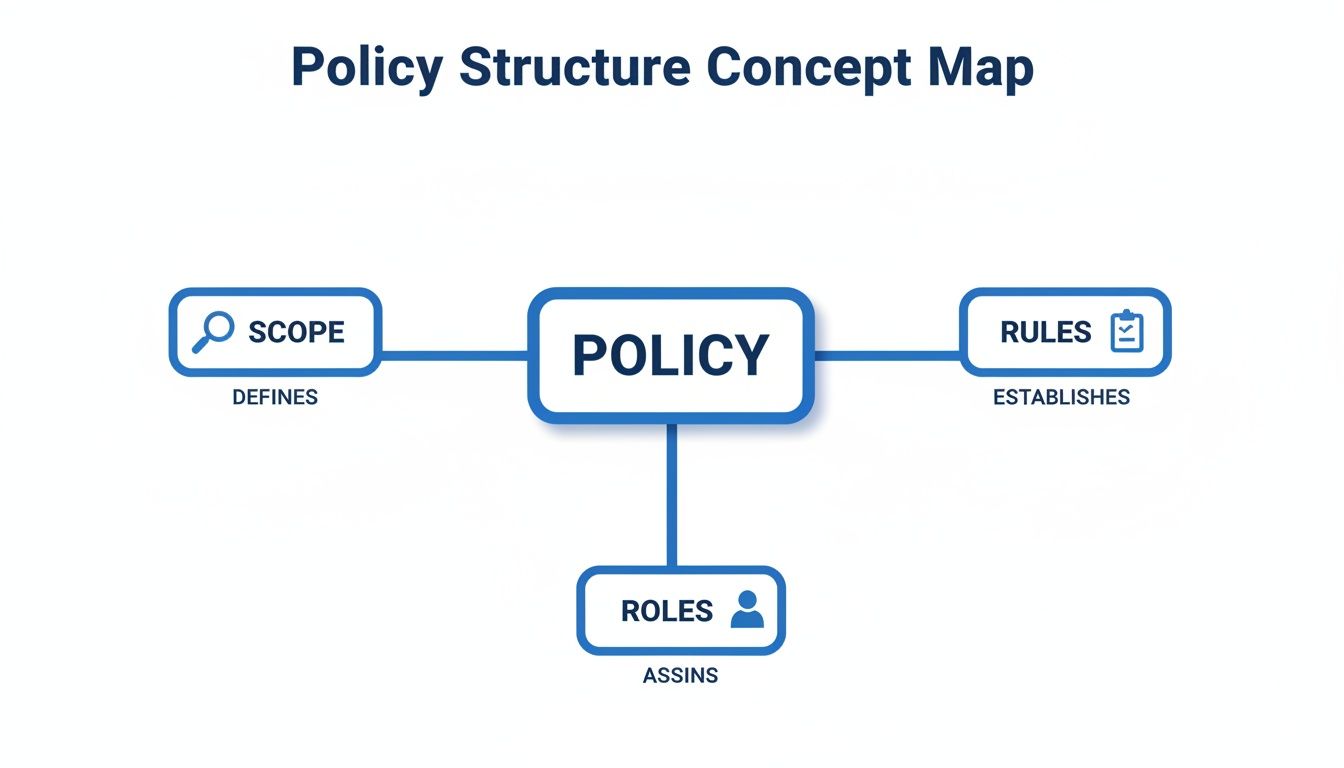
This structure is critical. It guarantees that every security control and decision is rooted in a clearly defined purpose and assigned to a specific owner, which is a non-negotiable requirement for any major compliance framework.
Your Policy as Auditable Evidence
Ultimately, the goal of mapping your policy to a framework is to create a seamless audit trail. Every statement in your policy should be a signpost pointing to tangible evidence—a documented procedure, a system log, a training record, or a specific configuration setting.
For example, your policy might state: "All privileged access must be reviewed quarterly." That single sentence establishes a clear, measurable requirement. During an audit, you simply present the records of those quarterly reviews. This proves you don't just have a rule; you consistently follow it.
This proactive approach completely changes your relationship with audits. Instead of a stressful, reactive hunt for documents, the audit becomes a straightforward process of walking the auditor through your established, policy-driven controls. You are in command of the narrative because you’ve already built the framework to support it. To get a better feel for this, you can explore the key ISO 27001 certification requirements and see why a strong policy is always the first step.
From Manual Drafting to AI-Powered Policy Creation
Moving an information security policy from theory to an actual, audit-ready document is where the real work begins. Traditionally, this meant a mountain of manual effort—endless meetings, massive spreadsheets, and stacks of paper. It was a grind.
Today, that whole workflow is being turned on its head. Let’s walk through the classic, manual way of doing things, and then dive into how modern, AI-powered tools are helping teams get this done faster and more accurately.
The Traditional Policy Drafting Checklist
No matter what tools you use, understanding the foundational, step-by-step process of building a policy is essential. This is how you ensure the final document actually reflects how your organization works.
-
Assemble a Cross-Functional Team: First things first, policy creation is a team sport, not an IT solo mission. You absolutely need people from IT, legal, HR, and other key business units at the table. This is the only way to create a policy that’s both technically solid and practical for people to follow day-to-day.
-
Define a Clear Scope and Objectives: Before you write a single word, you have to know what you’re trying to achieve. Start by documenting the policy's purpose, exactly who and what it covers (the scope), and the specific goals you're aiming for. This sets the direction for everything that follows.
-
Conduct a Comprehensive Risk Assessment: You can't protect what you don't understand. A proper risk assessment is non-negotiable. It’s how you identify your most valuable assets, figure out what threatens them, and find the weak spots in your current defenses. This is what tells you which security controls to prioritize.
-
Draft Core Policy Sections: With your risk assessment as a guide, you can start writing. This is where you flesh out all those core components we've discussed, like Acceptable Use, Data Classification, Access Control, and Incident Response.
-
Secure Stakeholder Buy-In: A policy without support from leadership is just a piece of paper. You have to circulate the draft among department heads and executives to get their feedback and, ultimately, their backing. If they don't buy in, nobody will follow it.
This manual process works, but it’s painfully slow and riddled with opportunities for human error. It often involves hundreds of hours just digging through documents to find proof that a specific control is being met—a tedious task that simply doesn't scale.
Accelerating Compliance with AI-Powered Tools
The single biggest bottleneck in policy management isn't writing the rules; it’s proving you follow them. This is exactly where AI-driven platforms are changing the game. Instead of manually digging through procedures, system logs, and training records, these tools automate the entire evidence-gathering and gap-analysis process.
Think about what it takes to verify one control from ISO 27001. The old way involves firing off emails to multiple teams, searching through shared drives, and hoping you find the right document. An AI-powered system can do that in minutes.
The real value of AI in compliance is not replacing human judgment, but supercharging it. By automating the low-level, repetitive task of finding evidence, AI frees up compliance professionals to focus on high-impact strategic work like risk mitigation and policy improvement.
This screenshot shows how an AI Gap Analysis platform can ingest all your documentation and automatically map it to compliance requirements, instantly flagging where the gaps are.
The key here is the shift from manual searching to automated discovery. The tool doesn't just tell you there’s a gap; it gives you direct links to the exact page in your documentation that serves as evidence. A task that used to take a week now takes a single click.
Bridging the Policy Gap for Emerging Technologies
This ability to quickly analyze your documentation becomes even more crucial as new technologies pop up. Take AI, for instance. A recent report found that while 66% of organizations expect AI to have the biggest cybersecurity impact in 2025, a shocking 37% have no process to assess an AI tool’s security before deploying it. That's a huge gap, and it's where existing security policies often fall short. You can read the full report here: WEF Global Cybersecurity Outlook 2025.
AI-powered tools can close this gap fast. They can scan your entire policy framework in minutes to find missing clauses related to AI governance, data usage, or model security. By automating this review, you can update your information security policy to cover these new risks much more quickly, keeping your defenses in sync with the real-world threats you face. To learn more, check out our guide on using AI for regulatory compliance.
Keeping Your Policy Relevant Through Continuous Improvement
Think of your information security policy as a living, breathing part of your organization, not a "set it and forget it" document. The real work begins after you’ve written it. A policy gathering dust on a shelf is worse than useless; it creates a false sense of security while leaving you wide open to very real threats.
The entire process is a constant cycle: enforce the rules, audit how well you're doing, and then use what you learn to make the policy better. This is how you build a resilient security posture that actually keeps up with your business goals and the ever-present reality of new threats.
Driving Adoption Through Enforcement and Training
Let's be blunt: a policy only matters if people follow it. This starts with clear communication and solid training. Your team needs to understand not just what the rules are, but why they exist. Consistent, engaging security awareness training is what shifts the culture from seeing security as a roadblock to seeing it as a shared responsibility.
Of course, you also need a plan for when people don't follow the rules. Having a fair, well-defined process for disciplinary action is critical. It's not about being punitive; it's about correcting risky behavior and reinforcing that security is non-negotiable before a small mistake turns into a major incident.
A policy is worthless without accountability. Enforcement transforms your document from a set of suggestions into a foundational element of your operational culture, ensuring that security is everyone's responsibility.
This isn't just theory—the market reflects the high stakes. In 2025, the global cybersecurity market hit a valuation of USD 218.98 billion, and that number is expected to climb as attacks get more sophisticated. This massive spending highlights just how essential a strong, enforced security framework is for protecting your assets. You can dig into more cybersecurity market trends at Fortune Business Insights.
Auditing and Maintaining Your Living Document
Regular audits are the health checks for your security policy. Think of internal audits as your practice runs—they’re where you test your controls, find weak spots, and make sure procedures are actually being followed. These reviews are invaluable for getting ready for the big show, like an official ISO 27001 audit, because they let you find and fix problems on your own terms.
Finally, you have to put a recurring date on the calendar for a formal policy review. This should happen at least once a year, but you'll need to do it sooner if there's a major shift in your business, such as:
- Adoption of new technologies (like moving to a new cloud platform)
- Changes in business operations (like expanding into a new region)
- Emergence of new threats or updated compliance rules
This commitment to the cycle of review and improvement is what keeps your information security policy from becoming obsolete. It ensures the document remains a powerful, relevant tool that genuinely protects your organization, both today and tomorrow.
Got Questions About Security Policies? We've Got Answers.
Even with the best-laid plans, creating and managing an information security policy always brings up a few practical questions. Let's tackle some of the most common ones that compliance pros and business leaders ask.
How Often Should We Update Our Information Security Policy?
At a minimum, you need to review your policy at least once a year. But don't just set it and forget it. A security policy that just gathers dust on a shelf is worse than useless—it's a liability.
Your policy is a living document. It needs to evolve right alongside your business. Be prepared to revisit it anytime you face a significant change, such as:
- Bringing in new technologies or major systems.
- Making a big shift in how your business operates.
- Facing new legal or regulatory rules, or when new cyber threats pop up on the radar.
What’s the Difference Between a Policy, a Standard, and a Procedure?
It helps to think of these as a pyramid, going from the very broad to the very specific.
A policy is the high-level "why" and "what." It's a statement from leadership that sets the direction. For example: "All sensitive company data must be encrypted."
A standard gets more specific about the "how." It provides the mandatory rules everyone must follow to meet the policy's goal. For instance: "All encryption must use the AES-256 algorithm."
A procedure is the ground-level, step-by-step instruction manual. It spells out exactly who does what, and when. For example: "Step 1: The database administrator will enable TDE encryption on the new customer database..."
Think of it this way: The policy sets the destination. Standards and procedures are the detailed roadmap—the turn-by-turn directions that ensure everyone gets there safely and consistently, leaving a clear trail for auditors to follow.
Who Is Actually Responsible for Creating and Enforcing This Thing?
Creating a solid policy isn't a one-person job; it’s a team sport. It’s usually led by a CISO or security manager, but they need to bring in key players from HR, legal, IT, and other business units to make sure it's practical and comprehensive.
When it comes to enforcement, the security team often handles the day-to-day technical side of things. However, the ultimate accountability lies with senior management. They are the champions who have to drive the policy's adoption and make sure every single employee understands their role in protecting the company.
Tired of digging through endless documents to find compliance gaps? What if you could see them instantly? With AI Gap Analysis, you can upload your policies, procedures, and system files, and get a clear, evidence-linked assessment against frameworks like ISO 27001 in just a few minutes. It's time to streamline your audit prep and focus on strategy, not searching. Get your first analysis run credit when you sign up at https://ai-gap-analysis.com.