January 19, 2026
pci dss compliance checklistpci compliancedata security standardpayment card industrycompliance automation
The Ultimate 12-Point PCI DSS Compliance Checklist for 2026
Navigate payment security with our definitive 12-point PCI DSS compliance checklist. Get actionable steps, expert tips, and audit guidance for 2026.
25 min readAI Gap Analysis

Navigating the Payment Card Industry Data Security Standard (PCI DSS) can feel like deciphering a complex, high-stakes code. Non-compliance carries significant risks, including steep financial penalties, severe reputational damage, and a critical loss of customer trust. However, achieving and maintaining this crucial certification does not have to be an insurmountable challenge. This article provides a definitive PCI DSS compliance checklist, designed to transform the standard's 12 core requirements from abstract principles into a concrete, actionable plan.
We will move beyond generic advice to deliver specific, practical guidance for each control. You will learn not just what to do, but how to implement security measures, what evidence auditors will demand, and how to identify common gaps before they become critical failures. This checklist details everything from firewall configuration and data encryption to physical security and incident response planning.
For each of the 12 requirements, this guide breaks down:
- Core Objective: The specific goal of the requirement.
- Required Evidence: The documentation and proof you'll need for an audit.
- Common Pitfalls: Frequent mistakes that lead to non-compliance.
- Testing & Validation: How to verify your controls are working effectively.
Whether you are preparing for your first Report on Compliance (ROC), managing ongoing adherence, or seeking to streamline your audit process, this comprehensive checklist serves as your roadmap. It is structured to help GRC teams, security professionals, and operations leaders build a robust security posture that not only protects cardholder data but also turns compliance from a stressful obligation into a strategic business advantage.
1. Requirement 1: Build and Maintain a Secure Network and Systems
As the first pillar in any robust PCI DSS compliance checklist, this requirement focuses on creating a secure network foundation to protect the cardholder data environment (CDE). The core principle is to establish strong access controls at the network perimeter and between internal network segments. This involves implementing and maintaining firewalls and routers configured to block unauthorized traffic, effectively creating a barrier against external and internal threats.
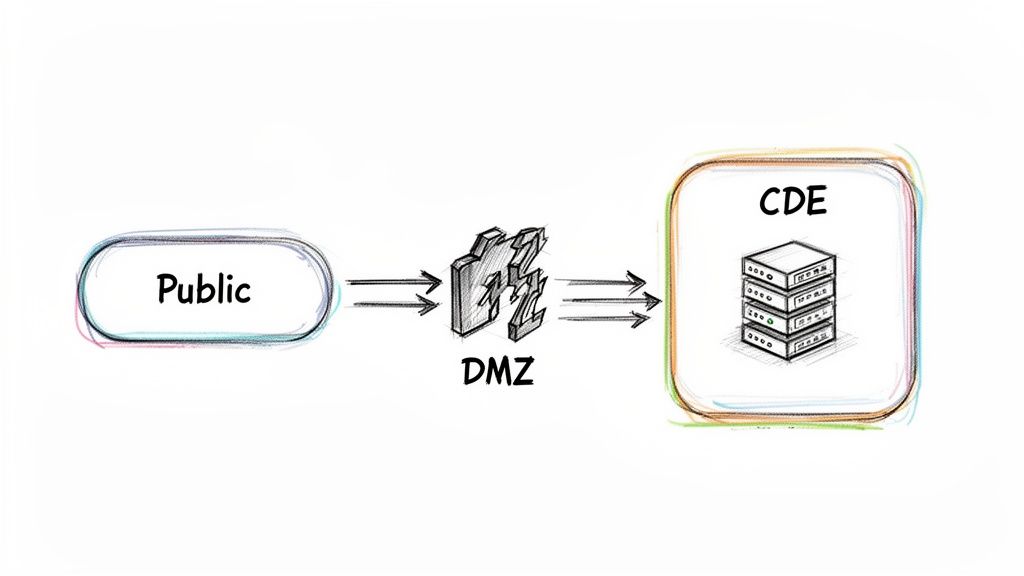
This foundational control is crucial because it limits the pathways attackers can use to access sensitive systems. Proper network segmentation isolates the CDE from less secure parts of your network, significantly reducing the scope of a potential breach and simplifying compliance efforts.
Implementation and Best Practices
To effectively meet Requirement 1, organizations must go beyond simply installing a firewall. A comprehensive approach involves several key actions:
- Network Segmentation: A common strategy is implementing a demilitarized zone (DMZ) to isolate public-facing servers from the internal CDE. For example, an e-commerce platform would place its web servers in a DMZ, while the payment processing and database servers reside in a more secure, isolated CDE.
- Firewall Rule Management: Each firewall rule must have a documented business justification, an owner, and a review date. Restrict traffic based on a "deny all" principle, only allowing explicitly authorized services and ports. For instance, a retailer should configure rules to permit database server access only from specific application servers, blocking all other internal traffic.
- Documentation and Diagrams: Maintain up-to-date network diagrams that clearly illustrate all CDE boundaries, connections to other networks, and the flow of cardholder data. These diagrams are essential for auditors and internal security teams to validate control effectiveness.
- Regular Reviews: Establish a formal process for reviewing firewall rules and network configurations at least every six months. Involve security, network operations, and business teams to ensure rules are still necessary and haven't introduced new vulnerabilities.
2. Requirement 2: Do Not Use Vendor-Supplied Defaults for Passwords and Other Security Parameters
This requirement addresses a fundamental and commonly exploited vulnerability: the use of vendor-supplied default credentials and settings. Attackers often use widely known default passwords (like "admin/admin" or "cisco/cisco") as an initial entry point to compromise systems. This control mandates that all default passwords and security parameters on devices like routers, firewalls, servers, and software are changed before they are installed in the cardholder data environment (CDE).
This is a critical step in any PCI DSS compliance checklist because default credentials provide a direct, low-effort path for unauthorized access. Failing to change them leaves the CDE exposed to automated attacks that scan networks for these known weaknesses. Enforcing unique, complex credentials from the outset hardens each component against compromise.
Implementation and Best Practices
Simply changing passwords is not enough; a systematic approach is necessary to ensure no defaults are overlooked. Organizations should implement the following best practices:
- System Hardening Procedures: Develop and follow a formal process for hardening all new systems before they are deployed. This checklist-driven process must include changing all default passwords, removing or disabling unnecessary default accounts, and configuring security settings to align with industry best practices.
- Inventory Management: Maintain a comprehensive inventory of all system components within the CDE. This inventory should track each device and software instance, confirming that its default credentials have been changed and documenting the date of the change for audit purposes.
- Automated Scanning: Use configuration management and vulnerability scanning tools to automatically detect systems that are still using default credentials. For example, a network infrastructure team can run automated scans to verify that all newly deployed routers and switches have had their default passwords rotated before going live.
- Credential Vaulting: Store administrative credentials in a secure password vault rather than using shared or easily guessable passwords. This centralizes management and ensures that access is controlled and audited, preventing the re-introduction of weak or default-like credentials.
3. Requirement 3: Restrict Access to Cardholder Data by Business Need-to-Know
This requirement establishes one of the most critical security principles in any PCI DSS compliance checklist: the principle of least privilege. Its focus is on ensuring that personnel can only access cardholder data (CHD) when there is a legitimate and documented business need. This involves implementing technical and administrative access control measures to restrict data visibility and interaction based on an individual's specific job function.
This control is vital because it significantly minimizes the risk of both intentional and accidental data exposure. By limiting access, an organization reduces its internal attack surface. If an employee's account is compromised, the potential damage is contained to only the data that person was authorized to see, rather than the entire cardholder data environment (CDE).
Implementation and Best Practices
Meeting Requirement 3 requires a systematic approach to defining, assigning, and reviewing user access rights across the CDE. This goes beyond simple user accounts and extends to applications, databases, and network systems.
- Implement Role-Based Access Control (RBAC): Define specific roles based on job responsibilities. For example, an e-commerce platform should create distinct roles for customer service representatives (who may only see the last four digits of a credit card) and a smaller, more privileged group of finance personnel who can view full transaction details for chargeback processing.
- Default to "Deny-All": Access permissions should operate on a "deny-all" basis, where access is explicitly granted only when a business justification is provided and documented. Access should never be granted by default.
- Centralized Identity Management: Use a centralized system like Active Directory or Okta to manage user identities and enforce access policies consistently across all systems within the CDE. This simplifies provisioning, de-provisioning, and auditing.
- Regular Access Reviews: Conduct formal access reviews at least quarterly. Managers must verify that their team members' access rights are still appropriate for their job roles. Any unnecessary or excessive permissions identified during these reviews must be promptly revoked.
4. Requirement 4: Protect Cardholder Data with Strong Cryptography
This requirement mandates the use of strong cryptography and security protocols to protect cardholder data (CHD) during transmission over open, public networks and when stored. The primary goal is to render CHD unreadable and unusable to unauthorized individuals, whether intercepted in transit or stolen from storage systems. Protecting data at these two critical points is a cornerstone of any effective PCI DSS compliance checklist.
This control is vital because it acts as a last line of defense. If other security measures fail and an attacker gains access to data files or network traffic, strong encryption ensures the sensitive information remains confidential and secure, drastically mitigating the impact of a breach.
Implementation and Best Practices
To meet Requirement 4, organizations must implement robust cryptographic controls and key management processes. A comprehensive strategy involves several key actions:
- Secure Transmission Protocols: Always use strong, industry-accepted security protocols like TLS 1.2 or higher for transmitting CHD over networks like the internet. For example, an e-commerce website must use HTTPS (which implements TLS) for its entire checkout process, from the shopping cart to the final payment confirmation page.
- Data-at-Rest Encryption: Implement strong encryption for stored cardholder data. This can be achieved through various methods, such as transparent database encryption (TDE) for a retailer's customer database or full-disk encryption on servers storing payment processing logs.
- Cryptographic Key Management: Document and implement formal policies for managing all cryptographic keys. This includes secure key generation, distribution, storage, and periodic rotation. Keys must be stored separately from the encrypted data and access to them strictly controlled.
- Never Store Sensitive Authentication Data: Prohibit the storage of sensitive authentication data (SAD), such as the full magnetic stripe data, CAV2/CVC2/CVV2/CID, or PINs, after authorization. This data is for transaction authorization only and storing it creates unnecessary risk.
5. Requirement 5: Protect Cardholder Data Against Unauthorized Access by Encrypting Transmission Across Open, Public Networks
A critical component of any PCI DSS compliance checklist, this requirement mandates the protection of cardholder data during transmission over open, public networks. The core principle is to prevent eavesdropping and man-in-the-middle attacks by using strong, industry-standard cryptographic protocols. Any time cardholder data travels outside of a trusted, internal network, such as over the internet, it must be encrypted.
This control is vital because unencrypted data in transit is highly vulnerable to interception. By enforcing strong encryption like Transport Layer Security (TLS) 1.2 or higher, organizations create a secure tunnel for data, ensuring that even if traffic is captured, the sensitive information remains confidential and unusable to unauthorized parties.
Implementation and Best Practices
To properly meet Requirement 5, organizations must go beyond basic encryption and adopt a comprehensive strategy for securing data in transit:
- Enforce Strong Protocols: Implement and configure all public-facing systems, such as web servers and APIs, to use only strong cryptographic protocols like TLS 1.2 or TLS 1.3. For example, an e-commerce platform must ensure its entire checkout process, not just the final payment page, is served over HTTPS with a valid certificate and modern cipher suites.
- Disable Insecure Protocols: Proactively disable outdated and vulnerable protocols like SSL, early TLS (versions 1.0 and 1.1), and weak cipher suites across all systems. This prevents downgrade attacks where an attacker forces a connection to use a weaker, more easily breakable protocol.
- Secure Remote Access: All administrative and remote access to the Cardholder Data Environment (CDE) must use multi-factor authentication and be encrypted with strong cryptography. A common implementation is using an IPsec or SSL/TLS VPN configured with robust encryption for all remote connections.
- Certificate Management: Maintain a detailed inventory of all SSL/TLS certificates used to protect cardholder data, including their expiration dates. Use automated tools like Let's Encrypt or cloud provider services (e.g., AWS Certificate Manager) to manage the certificate lifecycle and prevent service disruptions from expired certificates.
- Regular Scanning and Testing: Periodically scan all external-facing systems and internal connections for SSL/TLS misconfigurations, weak ciphers, and expired certificates. Use both automated tools and manual verification to confirm that encryption controls are correctly implemented and effective.
6. Requirement 6: Develop and Maintain Secure Systems and Applications
Requirement 6 is a critical component of any PCI DSS compliance checklist, focusing on embedding security into the entire lifecycle of systems and software within the cardholder data environment (CDE). The core principle is to prevent vulnerabilities from being introduced during development and to promptly remediate any that are discovered. This involves establishing secure coding practices, managing software patches, and protecting systems from malicious code.
This requirement is essential because software vulnerabilities are a primary attack vector. By building security into applications from the ground up and maintaining a robust vulnerability management program, organizations can significantly reduce their attack surface and protect sensitive cardholder data from being compromised through application-layer weaknesses.
Implementation and Best Practices
Achieving compliance with Requirement 6 necessitates a formalized and proactive approach to software and systems security. Key actions include:
- Secure Software Development Lifecycle (SDLC): Integrate security at every stage of development. For example, a fintech company must mandate peer code reviews for all changes to its payment processing API, specifically checking for common flaws like those in the OWASP Top 10.
- Vulnerability Management: Establish a process to identify and address security vulnerabilities promptly. This includes using reputable sources for security patch information and assigning risk rankings to new threats. Critical patches, such as one for a remote code execution flaw, must be deployed within 30 days.
- Integrated Security Testing: Automate security testing within your development pipeline. A SaaS provider could integrate Static Application Security Testing (SAST) and Dynamic Application Security Testing (DAST) tools into their CI/CD process to automatically scan code for vulnerabilities before deployment.
- Developer Training: Provide developers with regular training on secure coding techniques and emerging threats. This training should cover PCI DSS requirements and secure coding standards relevant to the technologies used. Successful programs often go hand-in-hand with a comprehensive cybersecurity risk assessment to identify key training areas.
7. Requirement 7: Restrict Access to Cardholder Data by Business Need-to-Know (with ongoing verification)
This requirement moves beyond static access control policies to an active, ongoing verification process. The core principle is "least privilege," ensuring that users only have the absolute minimum access required to perform their jobs. This principle is not a one-time setup but a continuous cycle of review, adjustment, and removal of access privileges to protect the cardholder data environment (CDE) from both internal and external threats.
This control is vital because excessive or outdated user permissions are a primary target for attackers. By regularly verifying that access remains appropriate and promptly revoking it when a user's role changes or they leave the organization, you significantly reduce the potential attack surface. It's a key part of any modern pci dss compliance checklist.
Implementation and Best Practices
To meet Requirement 7, organizations must establish a formal, repeatable process for managing the entire access lifecycle, from provisioning to de-provisioning.
- Role-Based Access Control (RBAC): Instead of assigning permissions to individuals, create predefined roles based on job functions (e.g., "Cashier," "Database Admin," "Customer Service Tier 1"). This simplifies administration and makes access reviews more efficient, as you review role membership rather than hundreds of individual permissions.
- Formal Access Reviews: Schedule and conduct regular access reviews, typically on a quarterly basis. A healthcare organization, for example, would have department managers formally sign off on the access rights of each team member with access to patient payment systems.
- Automated Offboarding: Integrate your access control system with HR workflows. When an employee is terminated, an automated process should be triggered to immediately revoke all their access to the CDE and other critical systems, minimizing the risk of post-employment data theft.
- Segregation of Duties: Maintain documented reviews to ensure no single individual has control over an entire transaction process without a secondary check. A payment processor's audit team, for instance, would verify that the person who can issue refunds cannot also approve their own refund requests.
8. Requirement 8: Assign a Unique User ID to Each Person with Access to Cardholder Data
This requirement establishes a fundamental principle of accountability: every action taken within the cardholder data environment (CDE) must be traceable to a specific, unique individual. By assigning a unique identifier (user ID) to every person with computer access, organizations can eliminate the ambiguity of shared or generic accounts, which make it impossible to determine who performed a specific action.
This control is a cornerstone of any effective PCI DSS compliance checklist because it underpins forensic investigations, incident response, and non-repudiation. Without unique identification, it is nearly impossible to hold individuals accountable for their actions, whether malicious or accidental, rendering other security controls less effective.
Implementation and Best Practices
To properly implement Requirement 8, organizations must create and enforce a strict identity and access management (IAM) policy. This involves several critical steps:
- Centralized Identity Management: Use systems like Active Directory, Okta, or Azure AD to manage user identities centrally. This ensures consistent application of policies for creating, modifying, and disabling user accounts across the entire CDE. For example, a payment processor can use a central directory to enforce unique IDs for all administrators, with access logged for auditing.
- Eliminate Shared Accounts: Proactively identify and decommission all shared or generic user accounts (e.g., "admin," "webmaster"). Each administrator, operator, and user must have their own named account. A healthcare system, for instance, must provide a unique login for each clinician accessing payment records.
- Automated User Provisioning: Integrate your IAM system with your HR system to automate the user lifecycle. Accounts should be automatically created upon hiring and, critically, disabled immediately upon employee termination to prevent unauthorized access by former staff.
- Regular Account Audits: Conduct quarterly reviews of all user accounts with access to the CDE. This process helps identify and remove dormant accounts, orphaned accounts, or any remaining shared credentials that may have been missed.
9. Requirement 9: Restrict Physical Access to Cardholder Data
As a critical layer in a defense-in-depth strategy, this requirement addresses the physical security of systems that store, process, or transmit cardholder data. The fundamental goal is to prevent unauthorized physical access to facilities, server rooms, and data media that could lead to tampering, theft, or unauthorized viewing of sensitive information. This involves implementing robust entry controls, monitoring physical locations, and managing the entire lifecycle of physical media.
This control is vital because even the most sophisticated digital security can be bypassed if an attacker gains direct physical access to a server or network device. A comprehensive physical security program, a key part of any PCI DSS compliance checklist, ensures that the cardholder data environment (CDE) is protected from on-site threats.
Implementation and Best Practices
Meeting Requirement 9 demands more than just locked doors; it requires a multi-faceted and documented approach to physical security.
- Controlled Facility Access: Use appropriate entry controls to limit and monitor physical access to sensitive areas. For example, a data center should implement multi-factor authentication, such as requiring an access card and a biometric scan, to grant entry to the server room.
- Visitor Management: Establish and enforce strict procedures for identifying and authorizing visitors. This includes issuing temporary identification badges that expire, maintaining a visitor log, and ensuring visitors are escorted by authorized personnel at all times within the CDE.
- Media Handling and Destruction: Create secure procedures for handling, storing, and ultimately destroying media containing cardholder data. This means using cross-cut shredders for paper documents or degaussing and physically destroying hard drives when they are decommissioned, with all destruction activities logged.
- Device Security: Protect devices that capture payment card data via direct physical interaction, such as point-of-sale terminals. Regularly inspect devices for evidence of tampering or substitution, and train staff to recognize suspicious activity.
10. Requirement 10: Log and Monitor All Access to System Components and Cardholder Data
Requirement 10 of the PCI DSS compliance checklist is centered on comprehensive logging and monitoring. The core principle is to track and analyze all access to network resources and cardholder data, enabling the organization to detect, prevent, and minimize the impact of a data breach. Without detailed logs, identifying unauthorized activity or investigating a security incident becomes nearly impossible.
This control is vital because it creates a digital trail of user activities, system events, and data access. By monitoring these logs in near real-time, security teams can quickly identify suspicious behavior, such as repeated failed login attempts or access to sensitive files outside of normal business hours, and respond before significant damage occurs.
Implementation and Best Practices
Meeting Requirement 10 requires more than just enabling system logs; it demands a systematic approach to log management and review. Key actions include:
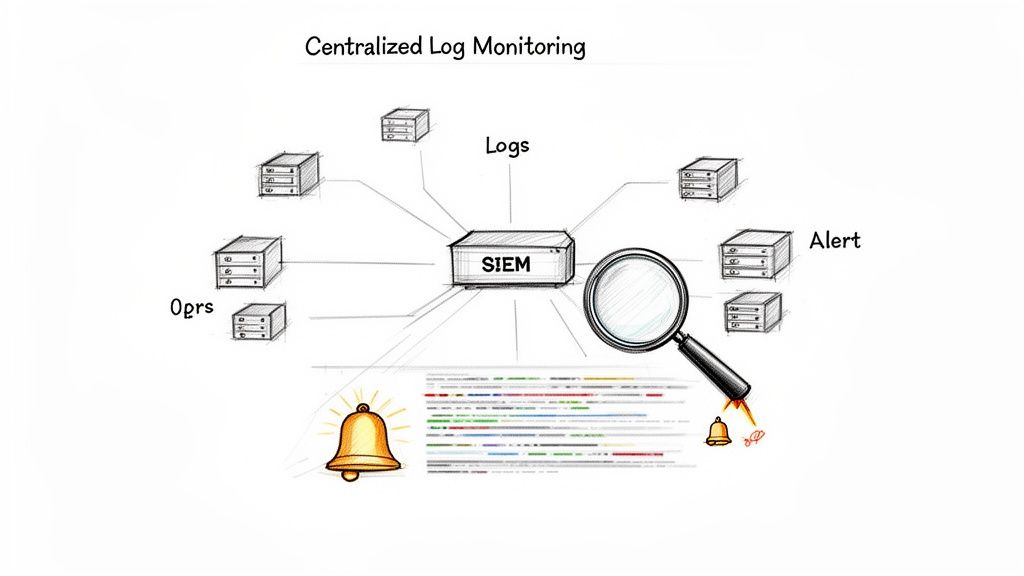
- Centralized Logging: Implement a Security Information and Event Management (SIEM) solution to aggregate logs from all critical systems within the CDE. For example, a retail business would forward logs from its point-of-sale terminals, payment application servers, and firewalls to a central SIEM for unified analysis.
- Define Logged Events: Ensure logs capture all individual user access to cardholder data, all actions taken by privileged users, and all authentication attempts. Logs must include the user identification, type of event, date and time, and the outcome (success or failure).
- Log Security and Retention: Protect log files from tampering by restricting access and storing them on a secure, centralized server. Logs must be retained for at least one year, with a minimum of three months immediately available for analysis to support incident investigations.
- Regular Log Reviews: Establish a formal process for daily review of security event logs. Automated alerts should be configured for critical events, but manual reviews are still necessary to identify anomalies that automated tools might miss. Documenting these reviews provides crucial evidence for auditors.
11. Requirement 11: Regularly Test Security Systems and Processes
As a critical verification control within the PCI DSS compliance checklist, this requirement mandates that organizations regularly test their security systems and processes to identify vulnerabilities before they can be exploited. The core principle is proactive validation: security is not a "set it and forget it" activity. This involves a multi-faceted approach, including regular vulnerability scanning, penetration testing, and monitoring for unauthorized wireless access points.
This ongoing testing is vital because new threats emerge constantly, and system configurations can change, inadvertently creating security gaps. By systematically testing controls, organizations can demonstrate that their security posture is effective and resilient over time, ensuring the CDE remains secure against evolving attack vectors.
Implementation and Best Practices
To meet Requirement 11, organizations must establish a formal, repeatable testing program. This goes beyond simply running scans and involves a structured approach to identifying and remediating weaknesses:
- Vulnerability Management Program: Implement a robust vulnerability management process with clear ownership and defined remediation timelines. For example, a healthcare provider must perform quarterly external and internal vulnerability scans, classifying findings by severity and remediating critical issues within 30 days.
- Penetration Testing: Conduct annual external and internal penetration tests performed by a qualified, independent firm. An e-commerce platform, for instance, would have testers simulate real-world attacks to identify exploitable weaknesses in its payment applications and network infrastructure.
- Continuous Monitoring: Deploy solutions to detect and alert on unauthorized wireless access points at least quarterly. Additionally, incorporate automated vulnerability scanning into CI/CD pipelines to identify security flaws early in the development lifecycle before they reach production.
- Documentation and Remediation: Meticulously document all testing methodologies, scope, findings, and remediation actions. Maintain a tracking system to monitor the status of each identified vulnerability and ensure it is re-tested and confirmed as resolved. A well-documented program provides clear evidence for auditors and is a key component of a successful audit risk assessment.
12. Requirement 12: Maintain an Information Security Policy
As the capstone of any effective PCI DSS compliance checklist, this requirement establishes the governance framework for the entire security program. Requirement 12 mandates that organizations create, publish, maintain, and disseminate a comprehensive information security policy. This policy acts as the authoritative source for security directives, ensuring all personnel, contractors, and relevant third parties understand their roles and responsibilities in protecting cardholder data.

This foundational document is critical because it formalizes the organization's commitment to security and provides the basis for all security controls. A well-defined policy ensures consistent application of security practices, supports training and awareness, and demonstrates due diligence to auditors and partners.
Implementation and Best Practices
Developing and maintaining a robust information security policy requires a structured and continuous effort. Key actions for meeting this requirement include:
- Comprehensive Coverage: The policy must explicitly address all 12 PCI DSS requirements. For example, a healthcare system processing patient co-pays must integrate specific PCI DSS controls into its broader organizational security policies, covering everything from access control to incident response.
- Annual Review and Acknowledgment: Establish a formal governance process to review the entire security policy at least annually or upon significant environmental changes. All relevant personnel must review and acknowledge that they have read and understood the policy, often tracked through a learning management system.
- Risk Assessment Integration: The policy should be informed by a formal risk assessment process. A payment processor, for instance, must update its policies to address emerging threats identified during its annual risk analysis, ensuring controls remain effective.
- Security Awareness Program: The policy must be supported by a security awareness program that educates personnel on its contents. This includes initial training upon hiring and ongoing refreshers to reinforce key security principles and any policy updates. You can learn more about how a gap assessment process can help identify areas where policies may need strengthening or better communication.
PCI DSS 12-Point Compliance Comparison
| Requirement | Implementation Complexity (🔄) | Resource Requirements (⚡) | Expected Outcomes (📊 ⭐) | Ideal Use Cases (💡) | Key Advantages (⭐) |
|---|---|---|---|---|---|
| Requirement 1: Install and Maintain a Firewall Configuration | High — network segmentation & rule management 🔄 | Moderate–High — firewall appliances, engineers, monitoring ⚡ | Strong perimeter control; reduced lateral movement 📊 ⭐⭐⭐ | CDE segmentation, DMZs, payment processors 💡 | Prevents unauthorized access; audit trails; compliance support ⭐ |
| Requirement 2: Do Not Use Vendor-Supplied Defaults | Low–Moderate — inventory + configuration tasks 🔄 | Low–Moderate — asset inventory, password vaults, automation ⚡ | Eliminates common attack vectors; basic hygiene 📊 ⭐⭐ | All deployments, routers, IoT/medical devices 💡 | Reduces automated attacks; demonstrable to auditors ⭐ |
| Requirement 3: Restrict Access by Business Need-to-Know | High — RBAC across heterogeneous systems 🔄 | High — IAM, provisioning workflows, admin overhead ⚡ | Minimized exposure; targeted monitoring and fraud prevention 📊 ⭐⭐⭐ | Finance, DB access, healthcare billing systems 💡 | Least privilege enforcement; simplifies audits ⭐ |
| Requirement 4: Track and Monitor All Access to Cardholder Data | High — centralized logging & correlation 🔄 | High — SIEM, storage, analysts, retention ⚡ | Detects breaches; forensic-ready audit trails 📊 ⭐⭐⭐ | High-risk environments, privileged account monitoring 💡 | Improves detection & investigation; accountability ⭐ |
| Requirement 5: Encrypt Transmission Across Open, Public Networks | Moderate — TLS/certificate deployment 🔄 | Moderate — PKI/cert mgmt, config updates ⚡ | Confidentiality in transit; MITM protection 📊 ⭐⭐⭐ | Web checkout, APIs, remote admin access 💡 | Prevents eavesdropping; regulatory expectation ⭐ |
| Requirement 6: Develop and Maintain Secure Systems and Applications | High — SDLC integration & testing 🔄 | High — SAST/DAST, training, secure-dev resources ⚡ | Fewer vulnerabilities; lower long-term risk 📊 ⭐⭐⭐ | Payment apps, fintech, SaaS platforms 💡 | Early detection; higher code quality; reduced incidents ⭐ |
| Requirement 7: Restrict Access (with Ongoing Verification) | Moderate–High — review processes + automation 🔄 | Moderate — review tools, manager time, HR integration ⚡ | Reduces access creep; timely deprovisioning 📊 ⭐⭐ | Organizations with contractors/high turnover 💡 | Continuous governance; reduces insider risk ⭐ |
| Requirement 8: Assign a Unique User ID to Each Person | Moderate — provisioning & lifecycle management 🔄 | Moderate — IDM/SSO, MFA, provisioning automation ⚡ | Clear accountability; improved forensics 📊 ⭐⭐⭐ | Admins, clinicians, DBAs, privileged users 💡 | Attribution for actions; deters misuse; audit-friendly ⭐ |
| Requirement 9: Restrict Physical Access to Cardholder Data | Moderate — physical controls & procedures 🔄 | High — badges, biometrics, CCTV, secure media storage ⚡ | Prevents theft of hardware/media; physical audit trail 📊 ⭐⭐ | Data centers, server rooms, media storage areas 💡 | Protects physical assets; complements logical controls ⭐ |
| Requirement 10: Create, Implement, and Maintain an Incident Response Plan | Moderate–High — cross-functional planning & drills 🔄 | Moderate — IR team, tooling, tabletop exercises ⚡ | Faster containment; preserved evidence; reduced impact 📊 ⭐⭐⭐ | Any org handling cardholder data; regulated sectors 💡 | Reduces downtime; supports notifications and compliance ⭐ |
| Requirement 11: Regularly Test Security Systems and Processes | Moderate–High — scheduled scans & penetration tests 🔄 | Moderate–High — scanning tools, external testers, remediation ⚡ | Identifies weaknesses; validates controls over time 📊 ⭐⭐⭐ | CDEs, CI/CD pipelines, pre-production & production testing 💡 | Continuous improvement; objective evidence for audits ⭐ |
| Requirement 12: Maintain an Information Security Policy | Moderate — policy drafting, governance, review 🔄 | Low–Moderate — stakeholder time, distribution & training ⚡ | Organizational alignment; foundation for controls 📊 ⭐⭐ | Entire organization; compliance programs & onboarding 💡 | Sets expectations; shows management commitment; audit evidence ⭐ |
From Checklist to Continuous Compliance: The Path Forward
Navigating the intricacies of the Payment Card Industry Data Security Standard can feel like a monumental task. You have now journeyed through a comprehensive PCI DSS compliance checklist, dissecting each of the 12 core requirements, from building secure networks to maintaining a robust information security policy. We've explored the specific evidence auditors demand, pinpointed common pitfalls where organizations often stumble, and outlined actionable remediation steps to fortify your defenses.
The core lesson is clear: compliance is not a destination you arrive at once a year. It's a continuous, dynamic state of security posture. The checklist is your map, but the journey requires ongoing vigilance, cultural commitment, and the right operational rhythm. Simply "checking the box" before an audit is a recipe for stress, security gaps, and potential breaches. The true goal is to embed these security controls so deeply into your daily operations that audit readiness becomes your default state.
Key Takeaways: From Theory to Action
Mastering this checklist means shifting your mindset from a reactive, project-based approach to a proactive, process-oriented one. Here are the most critical takeaways to carry forward:
- Evidence is Everything: Compliance isn't about what you say you do; it's about what you can prove you do. Meticulous documentation, from firewall rule reviews and access control logs to vulnerability scan reports and employee training records, forms the bedrock of a successful audit.
- Automation Over Manual Effort: The days of manually sifting through hundreds of documents to find evidence are over. The sheer volume and complexity of PCI DSS requirements make manual gap analysis inefficient and highly susceptible to human error. Embracing automation is no longer a luxury but a strategic necessity.
- Security is a Shared Responsibility: From the development team implementing secure coding practices (Requirement 6) to the HR department managing user access (Requirements 7 & 8), security is a collective effort. Fostering a security-aware culture is just as important as implementing technical controls.
Your Actionable Next Steps
Completing this checklist is a significant first step, but the work has just begun. To translate this knowledge into a sustainable compliance program, you must now focus on operationalizing these principles. The path forward involves moving beyond the checklist and into a state of perpetual readiness.
This is where modern tools can revolutionize your approach. The challenge of manually gathering evidence, mapping policies to specific PCI DSS sub-requirements, and identifying gaps is a massive time sink for even the most experienced GRC and security teams. This process is often a frantic, last-minute scramble that pulls critical resources away from strategic initiatives.
Key Insight: The future of compliance isn't about working harder; it's about working smarter. Leveraging technology to automate the discovery and mapping of evidence transforms audit preparation from a high-stress event into a managed, continuous process.
Tools that leverage AI can dramatically accelerate this journey. Imagine uploading your entire repository of policies, procedures, network diagrams, and system configurations and having an intelligent system automatically identify relevant evidence, map it directly to the corresponding PCI DSS controls, and generate a precise, actionable gap report in minutes, not weeks. This is the power of AI-driven gap analysis. It closes the loop between your documented policies and your operational reality, giving you a real-time, verifiable view of your compliance posture. By adopting this approach, you not only achieve compliance with confidence but maintain it efficiently, ensuring your customers' sensitive data is always protected.
Ready to transform your audit preparation from a manual struggle to an automated, intelligent process? Discover how AI Gap Analysis can instantly map your existing documentation to the PCI DSS compliance checklist, pinpointing gaps and streamlining evidence collection. Visit AI Gap Analysis to see how you can achieve continuous compliance with confidence.