January 18, 2026
vendor risk assessmentthird-party riskISO 27001supply chain securityrisk management
A Practical Guide to Vendor Risk Assessment
Master vendor risk assessment with our step-by-step guide. Learn to identify, analyze, and mitigate third-party risks to protect your business.
21 min readAI Gap Analysis

A vendor risk assessment is the process you use to pinpoint, analyze, and neutralize potential threats that third-party suppliers bring into your business. Think of your organization as a secure fortress; every vendor you work with is essentially a new gate in your walls. This assessment is your way of thoroughly inspecting each gate, ensuring it's just as strong as your own defenses and won't become an easy entry point for trouble.
Why Vendor Risk Assessment Is No Longer Optional
In today's interconnected world, your business is only as secure as your weakest partner. A single vulnerable vendor can create a domino effect, compromising your entire operation. This reality makes a structured vendor risk assessment an essential business strategy, not just another item on a compliance checklist. The old days of sealing a deal on a handshake are over; now, rigorous, evidence-based evaluation is the only way forward.
This shift is a direct response to the explosion of supply-chain attacks. When one of your vendors gets breached, it can become a backdoor right into your own systems. Suddenly, your sensitive data is exposed, your operations grind to a halt, and your reputation takes a serious hit. The whole point of a Vendor Risk Assessment (VRA) is to get ahead of these dangers before they turn into full-blown disasters.

The Soaring Stakes of Third-Party Risk
The scale of this problem is staggering. Between 2021 and 2023, supply-chain cyber incidents shot up by an incredible 431%. That has pushed third-party risk management straight to the top of the boardroom agenda.
Despite this alarming trend, there's a huge disconnect. A recent study found that a mere 4% of organizations feel confident that their questionnaire-based assessments actually reflect real-world security postures. This is especially concerning when you consider that 44% of these companies are assessing over 100 third parties every year.
This data tells a very clear story: traditional, manual methods just aren't cutting it anymore. The consequences of this failure are real and costly.
- Data Breaches: A compromised vendor can lead to unauthorized access to your customer data, intellectual property, or financial records.
- Operational Disruptions: If a critical supplier has an outage, it can shut down your production lines or stop your service delivery, leading to massive revenue loss.
- Compliance Failures: Regulators and certification bodies don't care if the breach started with your vendor—they hold you accountable. A weak partner can put your certifications at risk.
Understanding the Key Risk Domains
A thorough assessment looks at more than just cybersecurity. It's a holistic review of all the ways a vendor could impact your business. To get a clear picture, we can break down the risks into several key domains.
Here's a look at the primary categories of risk you should be covering:
| Risk Domain | Description | Example Threat |
|---|---|---|
| Cybersecurity Risk | Assesses the vendor's information security controls, policies, and ability to protect data from unauthorized access or breaches. | A vendor's unpatched software could be exploited, leading to a ransomware attack that exposes your shared data. |
| Operational Risk | Evaluates the vendor's ability to deliver their products or services reliably without interruption. | A key supplier's factory is shut down due to a natural disaster, halting your entire production line. |
| Compliance & Legal Risk | Examines the vendor's adherence to relevant laws, regulations (like GDPR or HIPAA), and industry standards. | A marketing partner violates data privacy laws, resulting in hefty fines and legal action against your company. |
| Financial Risk | Determines the vendor's financial stability and viability, ensuring they won't go out of business unexpectedly. | A critical software provider suddenly declares bankruptcy, leaving you without support or access to your data. |
| Reputational Risk | Considers how a vendor's unethical behavior or negative publicity could damage your own brand's reputation by association. | Your supplier is exposed for using unethical labor practices, leading to a public backlash against your brand. |
Looking at these domains helps ensure you're not leaving any major blind spots in your assessment process. A problem in any one of these areas can have serious ripple effects across your entire organization.
A Cornerstone of Compliance and Resilience
For any organization chasing certifications like ISO 27001, ISO 13485, or ISO 9001, a solid vendor risk program isn't just a good idea—it's a requirement. These standards demand you prove you have control over your entire information security ecosystem, and that absolutely includes your supply chain. A VRA is the hard evidence that shows auditors you're actively managing these external risks.
A mature vendor risk assessment program isn't just a reactive, box-ticking exercise. It's a proactive strategy for building a more resilient and trustworthy business. It's about making sure every partner you bring on board strengthens your fortress, rather than creating a new vulnerability.
Ultimately, performing a thorough vendor risk assessment is fundamental to modern business survival. It protects your assets, keeps you in good standing with regulators, and builds trust with customers who expect their data to be safe, no matter whose hands it's in. By truly understanding the intersection of compliance and risk assessment, you can build a stronger, more secure organization from the ground up.
Your Weakest Link Can Wreck Your Bottom Line
Skipping a proper vendor risk assessment isn't just a matter of ticking a compliance box—it's an open invitation to financial and operational disaster. When one of your third-party partners gets compromised, the fallout isn't some abstract cybersecurity problem. It shows up as real, hard costs that can bring a company to its knees.
The first hit is usually financial. Think about the immediate costs of investigating a breach, notifying every affected customer, and paying for credit monitoring. On top of that, you're looking at potentially massive regulatory fines, especially under frameworks like GDPR or HIPAA, which can easily run into the millions.
But the bleeding doesn't stop there. What happens when a critical vendor's failure brings your own services to a screeching halt? Every hour of downtime is an hour of lost revenue, frustrated customers, and eroding trust in your brand.
The Hidden Costs of Doing Things the Old Way
Long before a breach ever happens, outdated vendor assessment methods are already quietly draining your resources. Many teams are stuck in a time-consuming loop of manual processes, which acts like a hidden tax on their productivity.
Picture your top security and compliance people buried in spreadsheets, sending endless follow-up emails to vendors, and manually checking documents. It’s not just inefficient; it’s a colossal waste of their expertise. Instead of focusing on high-level strategy to protect the business, they’re bogged down in administrative busywork.
This manual approach is slow, incredibly prone to human error, and simply doesn't scale. As you bring on more vendors, the cracks in the system get wider, and your risk exposure grows right along with it.
A recent analysis really highlights the inefficiency. Over 50% of companies are spending at least 20 hours a week on these assessments. A third are spending over 30 hours—and most of that time is just spent chasing down information from vendors. The average company has 4-6 people tied up in this process.
The Shocking Truth About Vendor-Related Breaches
There's a direct line between this operational drag and real-world security failures. According to Whistic's 2023 State of Vendor Security Report, an eye-opening 77% of businesses that had a data breach last year said it came from a compromised vendor. That number confirms what many in the industry already knew: third-party risk is a massive, ecosystem-wide problem that needs a better solution.
These stats make it painfully obvious that the old way of doing things is broken. The time, money, and effort poured into manual assessments just aren't leading to better security.
- Financial Losses: The direct cost of a single vendor-related breach can easily exceed the entire annual budget for a modern risk assessment program.
- Reputational Damage: Trust is incredibly hard to build but can be destroyed in an instant. A public breach tied to one of your partners can do lasting damage to your brand.
- Competitive Disadvantage: While you're stuck in manual workflows, your competitors are using smarter tools to build more resilient and secure supply chains.
The argument for modernizing your vendor risk assessment process is crystal clear. Investing in an efficient, automated system isn't just another expense; it’s a critical defense against financial loss, operational chaos, and brand damage. Once you understand the true cost of a weak link in your supply chain, making the switch to a smarter approach becomes an easy decision.
Your Step-by-Step Vendor Risk Assessment Workflow
Running a solid vendor risk assessment isn't a one-and-done task; it’s a living, cyclical process. Think of it like building a custom security checkpoint for every partner, one that's designed specifically for the kind of access they need. A well-defined workflow turns this from a chaotic scramble into a predictable system that makes your entire supply chain stronger.
This flow shows how even a seemingly small vendor issue can snowball into a major business problem, drawing a straight line from a vulnerability to operational delays and, ultimately, financial damage.
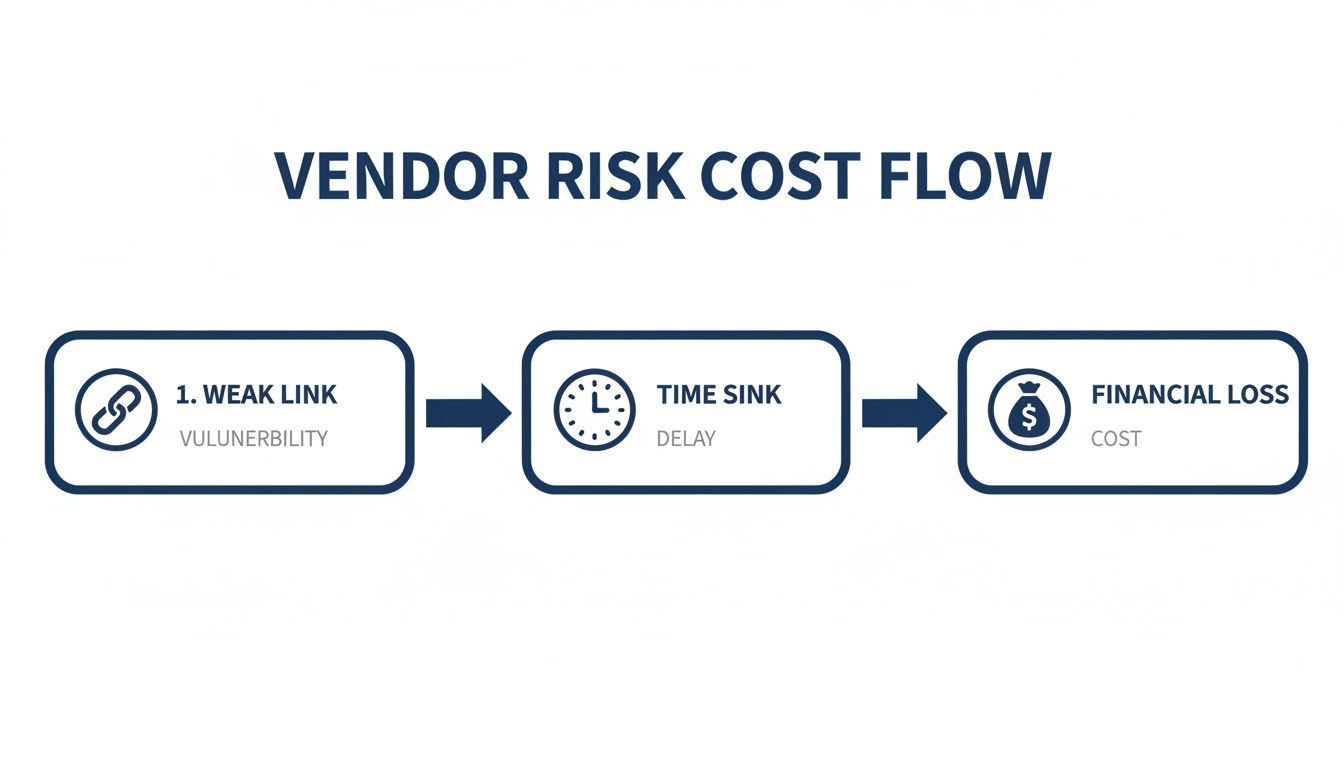
The diagram above paints a clear picture: a weak link in your supply chain becomes a time sink, draining resources and hitting your organization's bottom line.
Stage 1: Identify and Categorize Your Vendors
First things first, you need a complete and accurate inventory of every single vendor you work with. You can't manage risks you don't even know exist, and many companies have huge blind spots here—sometimes with hundreds of unvetted partners who could pose a threat.
Once you have a full list, it's time to sort them. Not all vendors carry the same weight. The company that supplies your office coffee is in a completely different risk category than the cloud provider hosting your customer's sensitive data.
You’ll want to categorize them based on two key factors:
- Criticality: How vital is this vendor to your day-to-day operations? If they disappeared tomorrow, would your business grind to a halt?
- Data Access: What kind of data do they touch? Is it public information, internal documents, or highly sensitive personally identifiable information (PII)?
This initial triage is crucial. It lets you focus your energy where it matters most, saving the deepest scrutiny for your high-risk, high-criticality partners.
Stage 2: Distribute Tailored Risk Questionnaires
With your vendors neatly categorized, you can start gathering information. Whatever you do, avoid the one-size-fits-all approach. Blasting a massive, 200-question security survey to a low-risk vendor is a waste of everyone's time and is likely to be ignored.
Instead, create questionnaires that match the vendor's risk tier. A high-risk vendor handling customer PII should get the full treatment, covering everything from encryption standards to their incident response plans. A low-risk vendor, on the other hand, might only need to answer a handful of basic questions about their general security policies. This targeted method respects your vendors' time and makes it far more likely you'll get prompt, accurate answers.
Stage 3: Collect and Analyze Evidence
A completed questionnaire is just a claim, not proof. The real work in a vendor risk assessment is verifying those claims with hard evidence. This is where you shift from simply trusting your vendor to actively verifying their security posture.
You'll need to systematically gather and review key documents. This often includes:
- Security Policies: Their official information security policy documents.
- Compliance Certifications: Proof of certifications like ISO 27001 or SOC 2 reports.
- Penetration Test Results: Reports from third parties that detail their security testing.
- Business Continuity Plans: Documentation that shows how they'd recover from a disaster.
This stage is frequently the most time-consuming, requiring you to dig through technical documents to find specific controls and procedures. Understanding the complete gap assessment process can give you a great framework for structuring this kind of deep dive.
Stage 4: Score Risk and Report Findings
After digging through the evidence, you need a way to quantify what you've found. This is where a risk scoring model becomes indispensable. By assigning scores based on the likelihood of a threat and its potential business impact, you can turn a pile of complex findings into a clear, prioritized list of risks.
For instance, a vendor who lacks a formal incident response plan (high impact) and has a history of minor security incidents (moderate likelihood) might earn a "High" risk score.
The whole point of scoring is to create an objective, data-driven picture of your vendor landscape. This gives you the ammunition to clearly communicate the most urgent issues to leadership and justify allocating resources for mitigation.
Your final report should be short, sharp, and actionable. It needs to highlight the top risks and spell out the recommended next steps.
Stage 5: Mitigate Risks and Monitor Continuously
Finally, your assessment has to lead to action. For every risk you've uncovered, you need a mitigation plan. This doesn’t always mean cutting ties with the vendor.
There are several ways to handle risk:
- Risk Acceptance: Formally accepting a low-level risk that would cost more to fix than it's worth.
- Risk Avoidance: Deciding not to partner with a vendor who is just too risky.
- Risk Transference: Using contracts or insurance to shift the financial impact of a risk.
- Risk Mitigation: Working directly with the vendor to implement new controls and close the security gaps you found.
Once a plan is in motion, the job isn't done. Vendor risk management is never a one-time event. You have to set up a schedule for ongoing monitoring and periodic reassessments to make sure your vendors' security doesn't slip over time. This continuous cycle keeps your defenses strong as new threats emerge and your relationships evolve.
How to Automate and Scale Your VRA Program
Let's be honest. The step-by-step workflow for a vendor risk assessment is solid in theory, but doing it manually is often the biggest bottleneck a compliance team faces. We see teams burning an enormous amount of time—often 30+ hours a week—just chasing down documents and reading through dense security policies. That kind of administrative drag makes it almost impossible to scale a VRA program.
As your company grows and you bring on more vendors, the manual process starts to buckle. It either breaks down completely, or worse, you're forced to cut corners. That creates dangerous blind spots you can't afford. To keep up, you have to find a smarter way to work, one that shifts the burden from manual drudgery to intelligent automation.
This is where modern AI tools are changing the game. They can turn the most time-consuming parts of an assessment into a fast, data-driven process. Think of it like having an AI agent that acts as your tireless compliance analyst, one that can read and actually understand hundreds of pages of vendor security documents in minutes, not weeks.
From Manual Review to Automated Insight
The real grind in any assessment is evidence discovery. You have a simple question—"Does this vendor have an incident response plan?"—and the answer is buried somewhere in their SOC 2 report, a security whitepaper, or a business continuity plan. Manually, this means hours of skimming, searching, and hoping you don't miss a critical detail.
Automation flips this whole model on its head. Instead of your team hunting for evidence, an AI agent does the heavy lifting. You just upload all the vendor's documentation, and the system gets to work.
This technology automates several key functions:
- Evidence Discovery: The AI reads and understands the context of the documents, pinpointing the exact sentences and paragraphs that answer your compliance questions.
- Cited Answers: It doesn't just give you a "yes" or "no." It provides a clear answer and links directly back to the source text, so you can verify it in a single click.
- Gap Identification: By comparing the vendor's evidence against a specific framework like ISO 27001, the AI instantly flags where controls are missing or just aren't described well enough.
This screenshot from AI Gap Analysis shows exactly how the platform presents these evidence-linked answers, making verification immediate and painless.
The interface neatly separates the compliance question from the AI-generated answer and the original source text. This builds a transparent and fully auditable trail.
A Tale of Two Workflows
To see the real-world impact, let's compare the old way and the new way of assessing a single high-risk vendor.
The Manual Workflow (Before Automation):
- Week 1: You request security documents from the vendor. Then you follow up. A few more times.
- Week 2: You finally get a jumble of PDFs. You start reading the 150-page SOC 2 report, trying to find evidence for just the first few controls.
- Week 3: Still slogging through documents, you're cross-referencing your findings in a massive spreadsheet. You think you found a gap but have to re-read a 50-page section to be sure.
- Week 4: You finally finish the review, draft a report, and schedule a call to clear up all the ambiguities. Total time spent: 30-40 hours.
The Automated Workflow (With AI):
- Day 1 (Hour 1): The vendor sends their documents. You upload them all to the platform.
- Day 1 (Hour 2): The AI has already analyzed everything. You're looking at a dashboard with clear, cited answers and a tidy list of identified gaps against your chosen framework.
- Day 1 (Hour 3): You export an audit-ready report and share it with the vendor. The conversation is now focused on a handful of specific, pre-identified issues. Total time spent: 2-3 hours.
This isn't just about saving time; it's about fundamentally changing the nature of the work. Automation frees your expert team from low-value administrative tasks and empowers them to focus on what humans do best: strategic risk mitigation and building strong vendor relationships.
By automating the evidence discovery and analysis, you can dramatically increase the number of vendors you assess without having to hire more people. This is how you effectively scale your vendor risk assessment program, improve the accuracy of your findings, and ultimately build a more resilient supply chain.
Essential Templates to Streamline Your Assessments
Knowing the theory behind a vendor risk assessment is great, but the real magic happens when you have practical tools to make it happen. Without them, every assessment feels like starting from scratch. You can’t compare vendors apples-to-apples, and tracking risk over time becomes a complete mess.
Consistency is everything. That’s why using templates is a non-negotiable for building an efficient, repeatable system. To get you started, we’ve laid out two fundamental tools: a checklist for gathering your evidence and a scoring matrix for making sense of it. These are your best bet for bringing order to the chaos and making decisions based on data, not just a gut feeling.
Vendor Risk Assessment Checklist
Think of this checklist as your pre-flight inspection before you bring a new vendor on board. It’s a simple, structured list of questions and document requests designed to make sure nothing critical gets missed. It’s all too easy to get tunnel vision on one risk area while completely ignoring another; a checklist forces a methodical, holistic approach.
A solid checklist should break down the vendor’s operations and security posture into clear categories.
- Information Security and Cybersecurity: Do they have documented security policies? Can they show you recent penetration test results or evidence of how they manage vulnerabilities?
- Data Privacy and Compliance: How are they handling sensitive data, particularly PII? What proof can they offer for compliance with regulations like GDPR or HIPAA?
- Business Continuity and Disaster Recovery: What’s the plan if their service goes down? More importantly, have they actually tested that plan, and can they share the results?
- Financial Viability: Is the company on solid financial ground? For critical partners, asking for financial statements or credit reports can save you from a huge headache later.
- Fourth-Party Risk Management: How does the vendor manage risk with their own critical suppliers? Understanding this is key to getting ahead of downstream risks that could impact you.
Using a consistent checklist ensures that every vendor risk assessment you conduct is both thorough and uniform. And when auditors come knocking, this level of documented diligence is exactly what they want to see. For a deeper look, our audit readiness checklist details what to prepare across your entire organization.
Vendor Risk Scoring Matrix
After you’ve gathered all that information with your checklist, you need a way to interpret it. This is where a risk scoring matrix comes in. It’s a simple but incredibly effective tool for turning qualitative findings into quantitative, objective scores. You can finally move beyond "this vendor feels risky" and into a clear, defensible scoring system.
The matrix works by assessing two key dimensions for every risk you identify:
- Likelihood: How likely is it that this will actually happen? You can score this on a simple scale, like 1 (very unlikely) to 5 (almost certain).
- Impact: If it does happen, how bad would it be for your business? This is also scored on a scale, like 1 (minor inconvenience) to 5 (catastrophic failure).
Multiply the two numbers together, and you get an overall risk score. This one calculation instantly tells you which problems need your immediate attention.
By plotting risks on a matrix, you create a visual heat map of your vendor's risk profile. Issues that land in the high-likelihood, high-impact quadrant become your immediate priorities for mitigation.
A scoring matrix helps you focus your energy where it matters most. Here's a sample of what that could look like.
Sample Vendor Risk Scoring Matrix
This table shows a straightforward way to combine the likelihood and impact scores to get a final risk rating and determine the next steps.
| Risk Level | Likelihood (1-5) | Impact (1-5) | Overall Risk Score (Likelihood x Impact) | Required Action |
|---|---|---|---|---|
| Low | 1-2 | 1-2 | 1-4 | Accept risk or monitor periodically. |
| Medium | 2-4 | 2-4 | 5-12 | Develop a mitigation plan; active monitoring required. |
| High | 4-5 | 4-5 | 13-25 | Immediate mitigation required; may need executive approval. |
By weaving these templates into your workflow, you’re well on your way to building a standardized and scalable vendor risk assessment program. They provide the structure you need to leave chaotic, one-off reviews behind and build a mature process that genuinely protects your organization.
Frequently Asked Questions About Vendor Risk Assessment
Even with a perfect workflow on paper, the real world of vendor risk management is messy. This is where theory crashes into practice, and knowing how to navigate the gray areas is what turns a simple box-ticking exercise into a genuinely strategic risk program.
Let's dig into some of the most common questions that pop up once you start putting your vendor risk assessment process into action. The goal here isn't just to give you textbook answers, but to share practical advice for handling these situations with confidence.
How Often Should We Reassess Our Vendors?
This is easily the question I hear most often, and the honest answer is: it depends. A one-size-fits-all annual review for every single vendor is a classic mistake. It's not just inefficient; it’s a great way to miss a brewing problem while you’re busy chasing paperwork.
A far better approach is to tie the frequency of your reviews directly to how much risk each vendor poses. Think of it as triage for your third-party relationships.
- High-Risk Vendors: These are the partners who are deeply embedded in your operations or handle your most sensitive data. They need the white-glove treatment—a full, deep-dive reassessment at least once a year, plus ongoing monitoring for any major security events or organizational changes.
- Medium-Risk Vendors: For this group, the risk is real but not business-critical. A thorough review every 18 to 24 months usually strikes the right balance, especially when you supplement it with some form of automated monitoring.
- Low-Risk Vendors: These partners pose a very small threat. A quick check-in every 2-3 years or whenever their contract is up for renewal is typically enough to make sure nothing has dramatically changed.
Basing your schedule on risk lets you point your limited resources where they can have the biggest impact. You’ll give your most critical vendors the scrutiny they deserve without drowning your team in low-value work.
What Should We Do If a Vendor Fails an Assessment?
First off, don't panic. A failed assessment isn't an automatic "goodbye." Think of it as the starting pistol for a crucial conversation. The first step is to get on the phone and clearly walk them through your findings, pointing to the specific gaps and the evidence you found.
From there, you’ve got a few paths you can take, depending on how serious the problems are.
- Create a Corrective Action Plan (CAP): This is your go-to move. You work with the vendor to build a realistic, time-bound roadmap for fixing the issues. It’s collaborative and, most of the time, the best way forward.
- Use Compensating Controls: Sometimes a vendor just can't fix a problem. In that case, can you build a fence around the risk on your end? This might mean limiting their access to certain data or putting extra monitoring in place on your side.
- Formally Accept the Risk: If a finding is minor and the cost of fixing it is huge, your organization might decide to just live with it. If you do this, make sure you document the decision, who made it, and why.
- Cut Ties: This is the last resort. If the risks are critical and the vendor is either unwilling or unable to fix them, your only responsible move is to start planning their exit. Protecting your own organization has to come first.
How Should We Handle Unresponsive Vendors?
A vendor who ghosts you during a risk assessment is a five-alarm fire. When a partner won’t cooperate, it usually means one of two things: they have something to hide, or they have a dangerously immature approach to security. Either way, it’s a huge red flag.
Start by gently but firmly reminding them of their contractual obligations to cooperate with security reviews. If that doesn't work, you need to escalate the issue inside your own company immediately.
An unresponsive vendor is not just a frustrating administrative hurdle; it represents an unquantifiable and unacceptable risk. Their silence leaves you completely blind to potential vulnerabilities they could be introducing into your ecosystem.
If they continue to stonewall you, you have no choice but to treat them as a high-risk entity and begin the offboarding process. You can't manage a risk you can't see.
The challenge of managing these relationships is exactly why the global market for vendor risk management tools is exploding. It's projected to hit USD 24.95 billion by 2030, with a compound annual growth rate of 15.2%. This isn't just about compliance anymore; it’s about integrating third-party oversight into the very fabric of enterprise risk management. You can learn more about these vendor risk management market trends to see where the industry is heading.
Stop wasting weeks on manual evidence discovery. With AI Gap Analysis, you can upload vendor security documents and get audit-ready, evidence-linked answers in minutes, not months. Our AI-powered platform automates the most time-consuming parts of a vendor risk assessment, freeing your experts to focus on strategic risk mitigation. Start your free trial and run your first analysis today.